
Master the Art of Software Proposal Evaluation in 2026
January 04, 2026 / Bryan ReynoldsThe High-Stakes Gamble of Digital Transformation
In the high-stakes arena of B2B technology, the software proposal is perhaps the most deceptively simple document on an executive’s desk. On the surface, it appears to be a transactional instrument: a promise of technical deliverables in exchange for capital. However, seasoned leaders—the Visionary CTOs, Strategic CFOs, and Driven Heads of Sales—know that a software proposal is actually a complex instrument of risk, innovation, and future operational capability. It is the roadmap for a journey that will either accelerate market dominance or become a sinkhole of technical debt and lost opportunity.
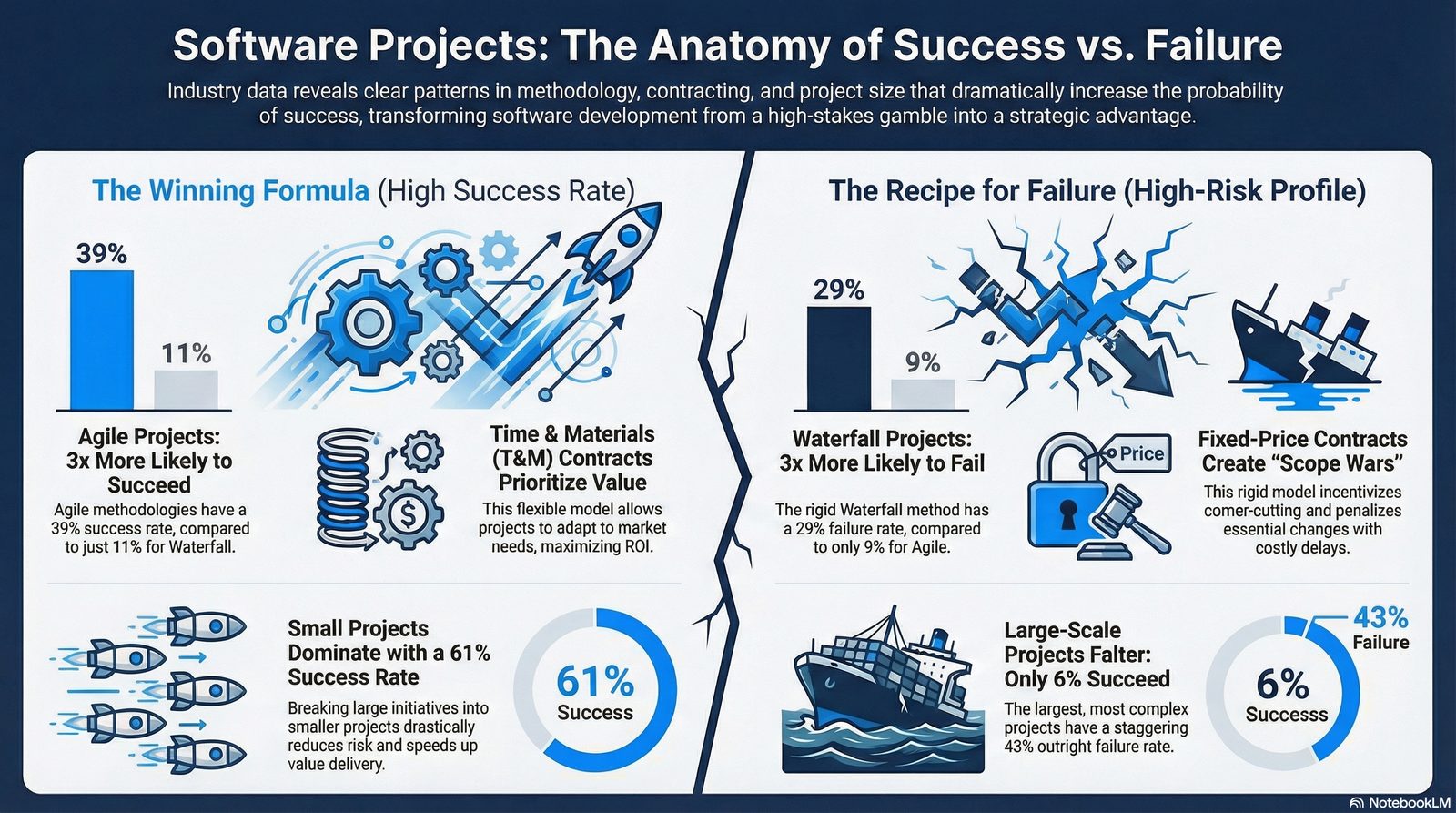
The statistics surrounding software procurement and execution are sobering, serving as a stark warning to any executive who treats a proposal review as a mere administrative formality. According to industry data, nearly 70% of IT projects fail to deliver satisfactory results, with budget overruns occurring in 45% of projects. The Standish Group’s renowned Chaos Report, a longitudinal study of software project health, consistently highlights that only a fraction of initiatives are completed on time and on budget. Specifically, data indicates that only 35% of projects are completed successfully, with nearly $1 million wasted every 20 seconds globally due to poor project management.
For an enterprise executive, the difference between a project that accelerates market dominance and one that stagnates lies in the rigorous, almost forensic, evaluation of the initial proposal. The proposal is the genetic code of the project; errors or weaknesses accepted here will replicate and compound throughout the development lifecycle.
This guide is not merely a checklist; it is a strategic framework for deconstructing software proposals. It is designed for buyers who refuse to accept the "black box" of development and demand transparency, accountability, and technical excellence. We will explore the nuances of architectural integrity, the economics of pricing models, the legal pitfalls of intellectual property ownership, and the operational realities of agile deployment. Whether you are evaluating a boutique custom shop or a large-scale systems integrator, the principles outlined here will arm you with the insight to separate high-quality partners from high-risk vendors.
The "Black Box" Asymmetry in Procurement
A fundamental asymmetry exists in software procurement. Vendors live in the code; buyers live in the business outcomes. Bridging this gap requires a translation layer—a way to read between the lines of "scope," "timeline," and "methodology." Many proposals are designed to look attractive: aggressive timelines, low fixed costs, and promises of "cutting-edge" tech. Yet, deeper analysis often reveals red flags: monolithic architectures that cannot scale, fixed-price traps that incentivize corner-cutting, or vague IP clauses that leave you renting your own innovation.
To evaluate a proposal effectively, you must adopt three distinct lenses:
- The Technical Lens: Does the proposed architecture and tech stack align with modern standards for scalability, security, and maintainability? Consider referencing our guide on best software product development services for further discussion on aligning software investments with business strategy.
- The Operational Lens: Does the vendor’s methodology (e.g., Rapid Agile Deployment) support adaptability and speed-to-market, or is it a rigid relic of the past?
- The Commercial Lens: Do the pricing model and contract terms protect your long-term interests and intellectual property?
At Baytech Consulting, we have spent years refining the art of the Tailored Tech Advantage—delivering solutions custom-crafted with cutting-edge technology—and Rapid Agile Deployment. We understand that a proposal is more than a quote; it is a blueprint for a partnership. This guide draws on that experience, dissecting what truly matters in a software engagement.
Phase 1: Decoding the Solution Architecture (The Technical Vetting)
The heart of any software proposal is the technical solution. However, proposals often gloss over how the software will be built in favor of what it will do. This is a critical error. The architectural decisions made at the proposal stage dictate the lifespan, scalability, and maintenance costs of the application for years to come. A proposal that is vague on architecture is a proposal that is hiding future costs.
1.1 The Architecture Check: Monolith vs. Microservices
One of the first "red flags" to look for in the technical section of a proposal is the suggestion of a monolithic architecture for a complex enterprise application. A monolith—where the user interface, business logic, and data access code are woven into a single, indivisible unit—is often cheaper to build initially but disastrous to scale.
The Monolithic Trap
In a monolithic architecture, the application is a single executable. If you need to scale the "Reporting" function because it is resource-intensive, you cannot scale just that function; you must duplicate the entire application server, which is inefficient and costly. Furthermore, a single bug in one module (e.g., payment processing) can crash the entire system. Updating a monolith is also fraught with risk, as a change in one area can have unforeseen ripple effects in another, leading to "spaghetti code" and a fear of deployment.
The Superior Alternative: Containerization and Orchestration
High-quality proposals will typically advocate for a modular approach using containerization technologies like Docker and orchestration systems like Kubernetes. This approach—often referred to as microservices or service-oriented architecture—treats the application as a collection of loose, independent services.
- Resilience: If the "Invoicing" service crashes, the "User Login" and "Product Search" services remain operational.
- Efficiency: You can scale specific services independently based on demand. If your users are searching more than buying, you scale the Search service, not the Checkout service.
- Future-Proofing: Individual components can be upgraded or rewritten in different languages without rewriting the whole system.
Buyer’s Insight: If a vendor proposes a complex solution without mentioning containerization (Docker) or orchestration (Kubernetes), ask why. It may indicate they are relying on outdated, "legacy" development practices that will increase your technical debt. At Baytech, we leverage Harvester HCI, Rancher, and Kubernetes to ensure that the solutions we build are cloud-native and ready for enterprise scale from Day One.
1.2 The Trap of Low-Code/No-Code for Core IP
In an effort to lower costs and shorten timelines, many vendors are pivoting toward Low-Code/No-Code (LCNC) platforms. While these tools have a place—typically for internal, non-critical workflows or simple prototypes—they pose significant risks for enterprise-grade, customer-facing applications. The allure of "speed" often masks the reality of "debt."
The Hidden Limitations of Low-Code
- Vendor Lock-In and Exportability: You do not own the source code; you rent the functionality. Most platforms do not allow you to export clean, usable source code. If the platform raises prices or goes out of business, your application is stranded, often requiring a complete rewrite to migrate.
- Scalability Ceilings: LCNC platforms rely on generic code libraries that often become "bloated." An application carrying extra weight for features it doesn't use leads to slower load times and higher memory usage. You cannot optimize the underlying code because it is a "black box".
- Security Obscurity: You are dependent on the platform provider’s security posture. If the platform is not SOC 2 Type II compliant, your data is at risk. Furthermore, 71% of organizations report "Shadow IT" problems where citizen developers bypass IT oversight, creating security vulnerabilities.
- Integration Complexities: While vendors claim easy integration, connecting LCNC tools to legacy systems or complex proprietary APIs often requires "hacky" workarounds that are brittle and difficult to maintain.
Strategic Advice: For core business functions that provide a competitive advantage, insist on custom software development using robust, scalable approaches. Custom solutions, built on frameworks like .NET or React, ensure you own the IP, control the roadmap, and can optimize performance at the granular level. Low-code can accelerate prototypes or simple tools, but for real differentiation, owning and shaping your technology is the only path forward.
1.3 Evaluating the Tech Stack: Specificity Matters
A vague tech stack section (e.g., "We will use modern web technologies") is a warning sign. It suggests either a lack of planning or a lack of expertise. A competent proposal should specify the exact tools and justify their selection based on your specific needs.
Baytech Consulting Tech Stack Example
When we construct a proposal, we explicitly list the stack components to ensure transparency and alignment with client infrastructure. We believe the client should know exactly what engine is under the hood:
- Development Environments: Azure DevOps On-Prem, VS Code/VS 2022. This ensures a robust, enterprise-grade IDE and lifecycle management.
- Database Layer: Postgres & pgAdmin or SQL Server. The choice depends on the data structure needs; Postgres offers incredible open-source cost efficiency, while SQL Server offers deep integration with Microsoft ecosystems.
- Infrastructure & Orchestration: Harvester HCI, Rancher, Kubernetes, Docker. This stack guarantees that the application is portable, scalable, and resilient. Learn more about our .NET, Docker, and Kubernetes service stack.
- Hosting/Cloud: OVHCloud servers, Microsoft 365/Teams/OneDrive integration.
Why this detail matters:
- Talent Availability: Is the stack popular enough that you can hire your own developers to maintain it later? (e.g., SQL Server and Postgres are industry standards).
- Licensing Costs: Are there hidden costs for database licenses? (Postgres is free; SQL Server is proprietary and costly).
- Integration Ecosystem: Will the stack play nicely with your existing Microsoft 365 or Google Drive ecosystem? A proposal that ignores your current ecosystem is a proposal for friction.
1.4 Red Flags in Software Design
Beyond the stack, look for specific "anti-patterns" in the proposal's technical description.
- Spaghetti Code Indicators: If the proposal describes a "single large repository" or lacks mention of service boundaries, you risk spaghetti code.
- Hardcoded Configurations: Does the proposal mention a "Configuration Management" strategy? If not, developers might hardcode credentials or settings, creating security risks and deployment nightmares.
- Lack of Error Handling Strategy: A good technical proposal will mention logging and monitoring (e.g., "We will implement centralized logging to track errors"). Absence of this suggests a "happy path" mentality that ignores real-world failure modes.
Phase 2: The Process is the Product (Methodology)
The "Plan of Work" section describes how the vendor intends to deliver the software. This is where you determine if the vendor is truly Agile or merely "Waterfall in disguise." In the modern B2B landscape, the methodology is as important as the code itself, because it determines your ability to adapt to changing market conditions.
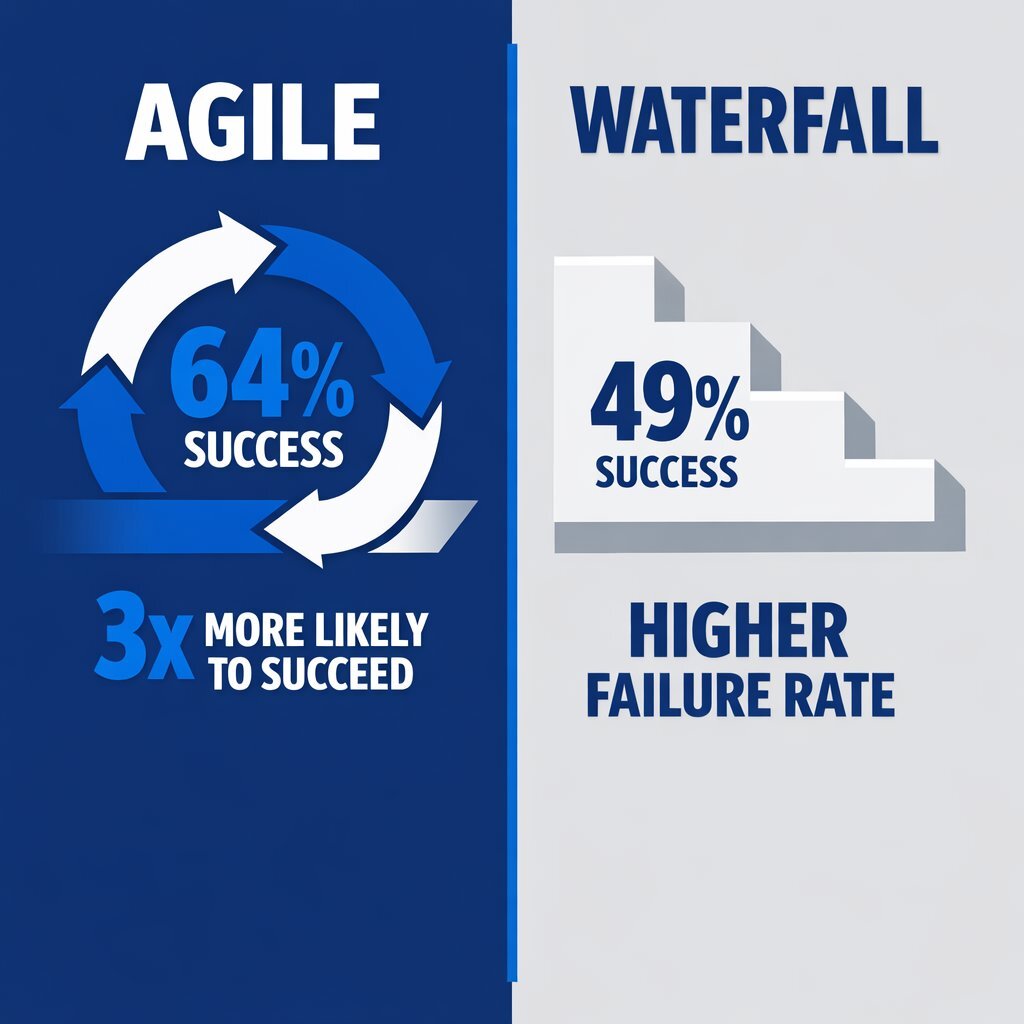
2.1 The Agile vs. Waterfall Reality: A Statistical Imperative
The debate between Agile and Waterfall methodologies is settled by the data. The Standish Group’s Chaos Report and other industry studies provide irrefutable evidence that Agile methodologies are superior for software development. You can explore a much deeper data-driven take in our analysis of enterprise productivity and agile success rates.
- Success Rates: 64% success rate for Agile versus 49% for Waterfall.
- Failure Rates: Agile projects are three times more likely to succeed and less than half as likely to fail outright compared to their traditional counterparts.
- Adoption: 71% of organizations have adopted Agile, yet many vendors still cling to Waterfall because it feels "safer" to contract for a fixed scope.
Why Waterfall Fails in Innovation
Waterfall assumes perfect knowledge at the start of a project. It requires rigid requirements gathering followed by months of development in a "black box," culminating in a "big bang" release. In the fast-moving B2B sector, business requirements change faster than Waterfall can adapt. By the time the software is delivered, the market need may have shifted, rendering the "perfectly built" software obsolete.
The Power of Rapid Agile Deployment
At Baytech, we utilize Rapid Agile Deployment. This methodology prioritizes:
- Iterative Delivery: Releasing working software in 2-week sprints. This allows the Visionary CTO to see progress and adjust the trajectory.
- Continuous Feedback: Stakeholders review progress constantly, preventing "scope drift" and ensuring that what is built is what is actually needed.
- Early ROI: By delivering a Minimum Viable Product (MVP) early, companies can start generating value or gathering user data months before a Waterfall project would even reach the testing phase.
Proposal Red Flag: If the proposal includes a massive, multi-month "Requirements Gathering" phase followed by a long "Development" phase with no scheduled demos or interim releases, it is a Waterfall project. Expect delays, misalignment, and a product that meets the spec but misses the market.
2.2 The Crucial Role of CI/CD and Automated Testing
A modern software proposal must address Continuous Integration/Continuous Deployment (CI/CD). This is the pipeline that automates the movement of code from the developer's machine to the production server. It is the heartbeat of a healthy engineering culture. For a comprehensive breakdown, see our DevOps efficiency service details covering CI/CD best practices.
Why CI/CD is Non-Negotiable
- Speed: Automated pipelines allow for multiple releases per day, rather than one per month. This aligns with the business need for "Faster Time to Market".
- Quality Assurance: Automated testing (Unit, Integration, Regression) runs every time code is committed. This catches bugs instantly, rather than weeks later during a manual QA phase. A proposal that relies solely on manual testing is a proposal for buggy software.
- Risk Reduction: Small, frequent updates are less risky than large, infrequent deployments. If a small deployment causes an issue, it is easy to roll back.

The "Red Flag" of Manual Deployment
If a vendor does not mention CI/CD, or if they charge extra for "setting up the environment" as an afterthought, proceed with caution. Lack of CI/CD implies manual deployments, which are prone to human error ("I forgot to copy that config file") and result in downtime. A proposal that ignores automated testing coverage—specifically referencing tools like Selenium or unit testing frameworks—is essentially planning for technical debt.
2.3 Transparency and Communication Protocols
How will you know if the project is on track? The proposal should define the communication cadence.
- Daily/Weekly Stand-ups: Are you invited? (You should be).
- Project Management Tools: Will you have access to their Jira, Azure DevOps, or Trello board? Transparency is key to trust. You should be able to see the backlog and the burn-down charts.
- The "Black Box" Warning: If the vendor insists on routing all communication through a single Account Manager rather than allowing access to the developers or Project Manager, they may be hiding resource constraints or outsourcing the work to a third party. At Baytech, we believe in direct access, ensuring that the "Visionary CTO" can speak engineer-to-engineer when necessary.
Phase 3: The Financial Framework (Pricing Models)
Pricing is often the most contentious part of a proposal. However, the amount is often less important than the model. The structure of the contract determines who bears the risk of the unknown, and consequently, how the vendor is incentivized to behave. For further analysis of pricing models, see our recently published guide to the best software outsourcing strategies.
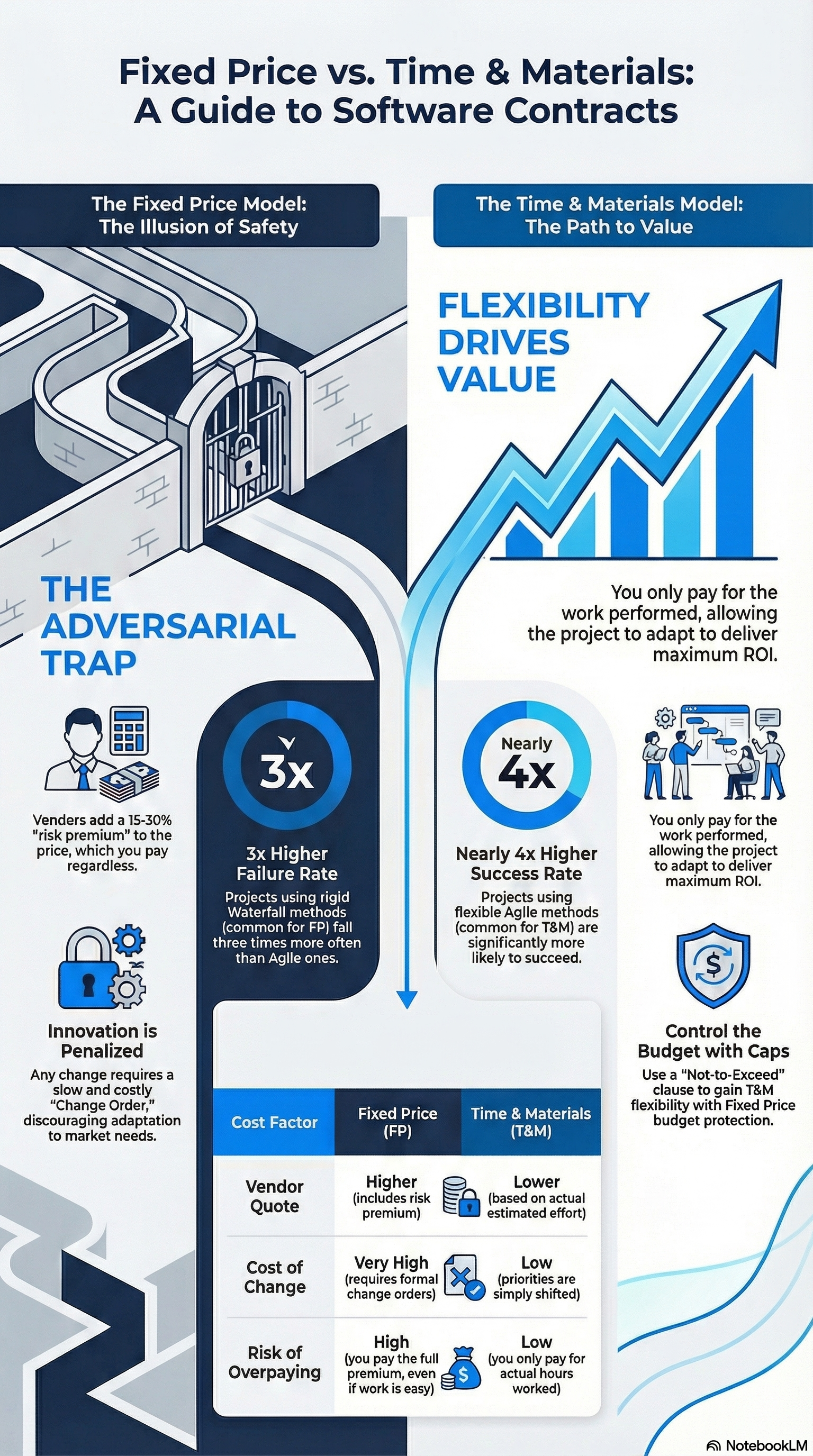
3.1 The Illusion of Fixed Price
Many executives prefer Fixed Price contracts because they offer perceived budget certainty. The logic is: "We agree on $100k, and I pay $100k no matter what."
The Reality: The Adversarial Trap
Fixed Price contracts often create an adversarial relationship.
- The Risk Premium: Because the vendor bears the risk of overruns, they must pad the estimate (often by 20-30%) to cover "unknowns". You are paying for risk, not just code.
- The Scope War: Every time you want to change a feature based on market feedback, the vendor must issue a "Change Order." This leads to delays, friction, and "nickel-and-diming." The vendor is incentivized to do the minimum required to meet the spec, not the best work to solve the problem.
- Rigidity: In a world where requirements evolve, Fixed Price contracts punish adaptation. They incentivize the vendor to say "no" to innovation.
Best Use Case: Fixed Price is only suitable for small, strictly defined projects with zero ambiguity (e.g., a simple marketing website or a small predictable utility), which are rare in enterprise software.
3.2 The Flexibility of Time and Materials (T&M)
Time and Materials contracts bill for the actual hours worked.
- Pros: Maximum flexibility. You can shift direction instantly. The team acts as an extension of your own staff. You pay for value delivered, not risk padding.
- Cons: The fear of the "blank check." Without a cap, costs can theoretically spiral if not managed tightly.
3.3 The Capped T&M (Not-to-Exceed): The Executive Compromise
The smart middle ground—and often the hallmark of a mature vendor—is the Capped Time and Materials model (or "Not-to-Exceed").
- How it works: The vendor works on an hourly basis but agrees that the total cost will not exceed a certain limit without explicit approval.
- The Advantage: If the project is finished early or efficiently, you pay less than the cap. If it hits the cap, the vendor shares the risk. This aligns incentives: the vendor wants to be efficient to maintain margin, and you get budget protection.
- Contract Language: Look for clauses like: "The total cost of the services under this Agreement will not exceed $______ (the 'Fee Cap') without the prior written authorization of the Client".
3.4 Hidden Costs: The Iceberg Beneath the Surface
A proposal might look cheap until you factor in the hidden costs that appear post-signature. A comprehensive evaluation must aggressively hunt for these omissions.
Table 1: Common Hidden Costs in Software Proposals
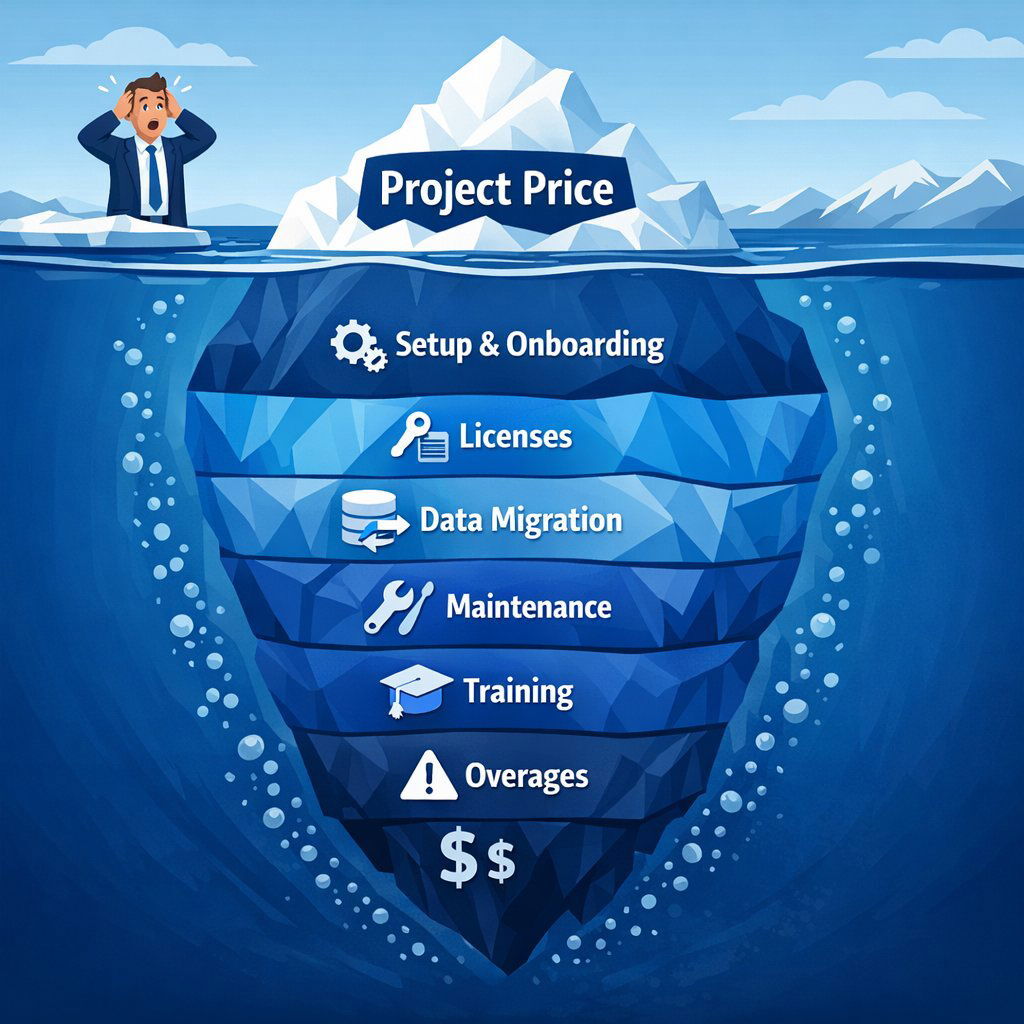
| Cost Category | Description | The Risk |
|---|---|---|
| Setup & Onboarding | Fees for server setup, environment configuration, or initial team ramp-up. | Often excluded from the "development" line item but essential to start. |
| Third-Party Licenses | Costs for database licenses (SQL Server), cloud hosting (Azure/AWS), or plugins. | Recurring costs that scale with users. Vendor proposals may only quote their labor. |
| Data Migration | Moving data from legacy systems to the new solution. | Often underestimated. Cleaning and mapping old data is time-consuming and expensive. |
| Maintenance (Retainer) | Post-launch bug fixes, OS updates, and security patches. | Software is never "done." Without a maintenance agreement, you are vulnerable to "bit rot." |
| Training | Teaching your staff how to use the admin panels and features. | If not included, user adoption—and ROI—will suffer. |
| Overages | Storage fees, API call limits, or user seat limits. | Typical in SaaS or low-code contracts; less common in custom dev but possible with cloud resources. |
Buyer’s Insight: Ask the vendor explicitly: "What line items are not included in this total that we will need to pay for to go live?" Dive further into total cost risks with our article on adaptive maintenance and software success.
Phase 4: Risk, IP, and Legalities
The legal terms of a software proposal are not just "boilerplate"; they define the asset value of the project. If you pay for custom software but don't own the code, you have paid for a liability, not an asset.
4.1 The Intellectual Property Battleground
Who owns the code? The answer is not always "you." This is the single most common pitfall in software contracts. Learn more about pitfalls and how to guard your organization's IP from the AI trust paradox in modern software development.
The "Work Made for Hire" Doctrine
In the U.S., copyright law defaults ownership to the author (the developer), not the person paying, unless there is a written agreement stating otherwise. A proper proposal or Master Services Agreement (MSA) must explicitly state that the work is a "Work Made for Hire" and that all rights are assigned to the client.
The "Magic Words" of Assignment

Do not rely on "we transfer ownership." Look for the specific legal phrasing: "Developer hereby assigns to the Company all of Developer's right, title, and interest in and to the developed software".
- License vs. Assignment: If the contract says the vendor grants you a "perpetual, exclusive license," you do not own the code. You cannot resell it, and potentially cannot take it to a new vendor without permission. You want Assignment, not Licensing.
- Background IP: Vendors often reuse code libraries (Background IP) to speed up development. This is good practice, provided the contract grants you a perpetual, royalty-free, non-exclusive license to this Background IP so your application continues to function if you part ways with the vendor.
4.2 Security and Compliance Due Diligence
For B2B firms in finance, healthcare, or high-tech, security is paramount. A proposal must demonstrate "Security by Design," not security as an afterthought. Interested in how AI is driving change in these risk-first sectors? Read our feature on revolutionizing software security with AI.
Key Questions to Ask:
- Data Handling: How is data encrypted in transit and at rest? (Standard: TLS 1.2+ and AES-256).
- Vulnerability Testing: Does the proposal include budget for penetration testing or security audits?
- Compliance: Does the vendor understand your regulatory environment (HIPAA, GDPR, SOC 2)?
- Documentation: Before signing, ask how they document their security procedures. Clear documentation ensures your internal IT team (or a future vendor) can maintain the system security.
Red Flag: A vendor who answers security questions with "We use standard security" without specifics is likely inexperienced in enterprise risk management.
Phase 5: The Vendor Scorecard (Decision Matrix)
Subjective feelings ("I liked their sales rep") are a poor basis for a million-dollar decision. You need a data-driven evaluation method. This removes emotion and focuses on business value and risk mitigation.
5.1 Building the Weighted Decision Matrix
Create a spreadsheet to score each proposal on a weighted scale. This objective framework helps in justifying the decision to other stakeholders (CFO, Board). For inspiration on how to keep your evaluation truly actionable, check out our recent thought-piece on the people side of system migrations and change management.
Suggested Weighting Model:
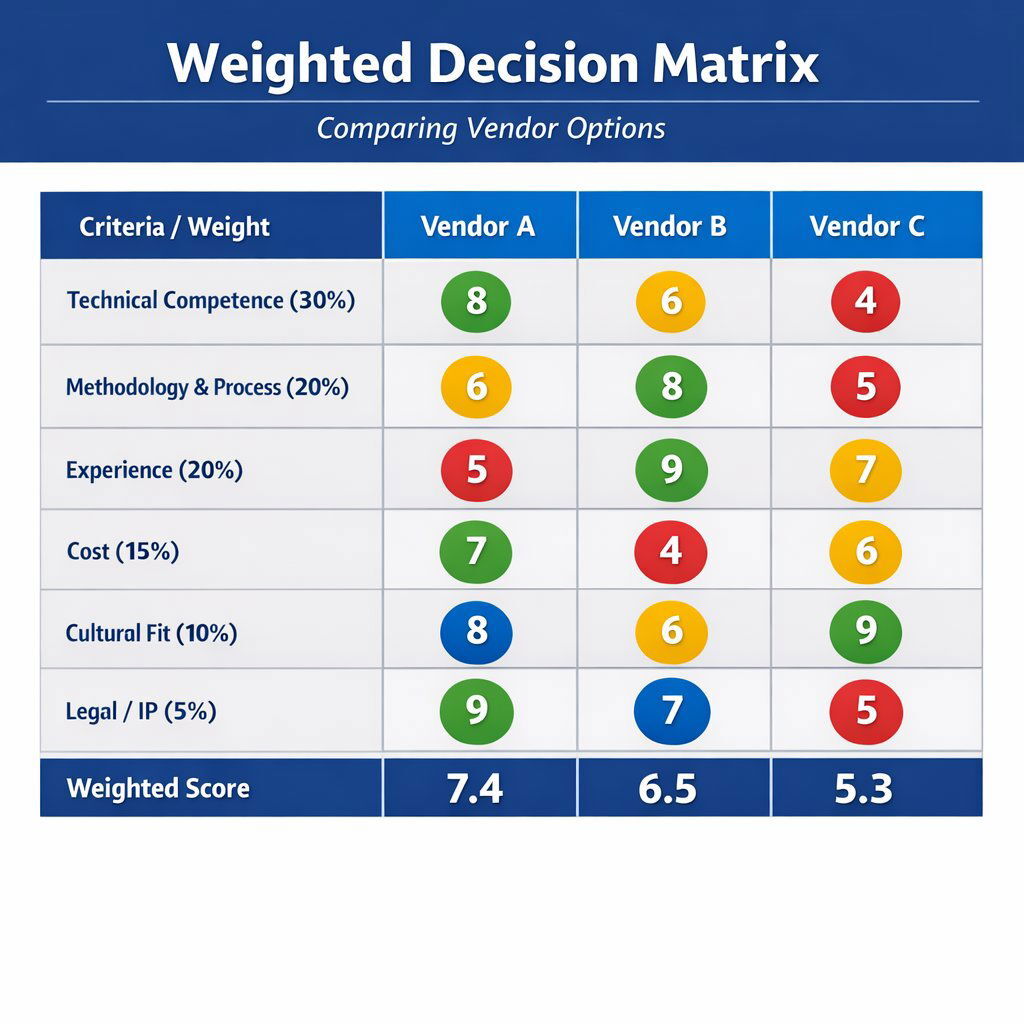
| Criteria | Weight | What to Evaluate |
|---|---|---|
| Technical Competence | 30% | Architecture quality, tech stack fit (e.g., Kubernetes, .NET), approach to scalability, and avoidance of monoliths. |
| Methodology & Process | 20% | Agile maturity, CI/CD pipelines, testing automation, transparency tools, and communication cadence. |
| Team & Experience | 20% | Proven track record in your industry, tenure of developers, verifiable references, and "Key Personnel" clauses. |
| Cost & Value | 15% | Transparency of pricing, TCO (Total Cost of Ownership), realism of the estimate (not just the lowest number), and hidden cost disclosure. |
| Cultural Fit | 10% | Communication style, responsiveness, willingness to challenge your assumptions (consultative vs. order-taker). |
| Legal & IP Terms | 5% | Clarity of IP ownership (Assignment vs. License), fair warranty terms, and security compliance. |
Scoring Guide:
- 1 (Poor): Vague, generic, or misses the requirement. (e.g., "We will build a secure app.")
- 3 (Average): Meets standard expectations but offers no competitive advantage. (e.g., "We use SSL encryption.")
- 5 (Exceptional): Demonstrates deep expertise, tailored insight, and strategic value. (e.g., "We implement AES-256 encryption at rest, utilize a zero-trust architecture, and include automated penetration testing in the CI/CD pipeline.")
5.2 The "Tough Questions" Interview (Due Diligence)
Before finalizing the score, conduct a technical interview with the vendor's delivery team (not just the sales rep).
- "Tell me about a project that went off the rails. How did you handle it?" (Tests honesty and crisis management).
- "How do you handle technical debt? Do you budget time for refactoring?" (Tests long-term thinking).
- "What is your approach to handling data growth and scalability at the storage layer?" (Tests technical depth—look for answers involving sharding, indexing, or read replicas).
- "Will you sign a Non-Disclosure Agreement (NDA) before we share our proprietary data?" (Standard, but essential).
- "Can I speak to a client who left you?" (The ultimate reference check).
Phase 6: Why "Tailored Tech" Wins in the Enterprise
In the B2B landscape, off-the-shelf software is a commodity. Your competitors can buy the same SaaS tools you can. Competitive advantage comes from Tailored Tech Advantage—software that fits your unique operational workflows like a glove. For a deep dive on tailoring technology, see our featured article: revolutionizing enterprise coding with AI in 2025.
6.1 The Customization-Efficiency Frontier
Studies show that businesses often use only 10-15% of the features in off-the-shelf enterprise software, yet they pay for 100% of the bloat. Custom software allows you to:
- Eliminate Bloat: Build only what you need, streamlining user interfaces and reducing training time.
- Integrate Deeply: Connect disparate systems (CRM, ERP, Accounting) into a unified workflow, eliminating manual data entry and reducing errors.
- Scale Indefinitely: Unlike SaaS platforms that charge per seat, custom software often has a flat cost structure for usage, becoming cheaper per-unit as you scale. You own the engine; you don't pay a toll to use it.
- Security Customization: You can build security protocols that match your specific risk profile, rather than relying on a generic vendor's "one size fits all" approach.
6.2 Baytech’s Approach: The "Anti-Black Box"
At Baytech Consulting, our proposals are designed to dismantle the common fears of software buying. We structure our engagements to be the antithesis of the "Black Box."
- Transparent Stacks: We use industry-standard, transferable technologies (Azure DevOps, VS 2022, Kubernetes). We want you to be able to hire anyone to maintain it, not just us.
- Rapid Agile Deployment: We don't ask you to wait 6 months for a "reveal." You see progress in weeks. We iterate, we adapt, and we deploy.
- Partnership: We act as your strategic technical arm, not just a vendor. Our goal is to empower your Visionary CTO and Strategic CFO with data, control, and results. We leverage our expertise in Harvester HCI and Rancher to provide infrastructure that is as robust as it is flexible.
Conclusion: The Final Verdict
Evaluating a software proposal is an exercise in risk management and strategic foresight. It requires looking past the bottom-line number to understand the engine that will drive that number.
The Winning Proposal Will Have:
- A Modular Architecture (Microservices/Containers) that ensures scalability and resilience.
- A Transparent Methodology (Agile/CI/CD) that guarantees visibility and quality.
- A Fair Pricing Model (Capped T&M) that aligns incentives and shares risk.
- Clear IP Ownership that protects your asset and future valuation.
The Next Step:
Do not simply read the proposal; stress-test it. Use the scorecard provided in this guide. Ask the uncomfortable questions. Demand to meet the lead engineer. If a vendor hesitates to provide transparency, they are showing you exactly how they will behave during the project.
Your software is the digital spine of your organization. Choose a partner who treats it with the structural integrity it deserves.
Frequently Asked Question
Q: Should I choose the lowest bidder to save money on my software project?
A: Rarely. In software development, the "lowest bid" is often a mirage that leads to higher long-term costs. Low bids frequently result from:
- Underestimation of Scope: The vendor doesn't understand the complexity and will hit you with "Change Orders" later to make up the difference.
- Junior Talent: Using inexperienced developers who take longer and write buggy code, increasing your long-term maintenance costs (Technical Debt).
- Corner Cutting: Skipping automated testing, security reviews, or documentation.
The true cost of software is the Total Cost of Ownership (TCO) over 3-5 years. A higher initial bid from a mature partner using Rapid Agile Deployment often results in a lower TCO because the software is built right the first time, scales efficiently, and requires less remedial maintenance. As the adage goes: "If you think good architecture is expensive, try bad architecture."
Further Reading
- https://koud.mx/checklist-for-evaluating-software-development-proposals/
- https://www.baytechconsulting.com/blog/time-and-materials-vs-fixed-price-2025
- https://cdn1-public.infotech.com/agile/CHAOSReport2015-Final.pdf
About Baytech
At Baytech Consulting, we specialize in guiding businesses through this process, helping you build scalable, efficient, and high-performing software that evolves with your needs. Our MVP first approach helps our clients minimize upfront costs and maximize ROI. Ready to take the next step in your software development journey? Contact us today to learn how we can help you achieve your goals with a phased development approach.
About the Author

Bryan Reynolds is an accomplished technology executive with more than 25 years of experience leading innovation in the software industry. As the CEO and founder of Baytech Consulting, he has built a reputation for delivering custom software solutions that help businesses streamline operations, enhance customer experiences, and drive growth.
Bryan’s expertise spans custom software development, cloud infrastructure, artificial intelligence, and strategic business consulting, making him a trusted advisor and thought leader across a wide range of industries.


