
Revolutionizing Software Security: How AI and CodeMender Are Changing the Game
November 19, 2025 / Bryan Reynolds
Google's CodeMender Is Here to Fix Your Code. But What Are the Real Questions Your Business Should Be Asking?
The headlines are relentless, painting a picture of a digital world under siege. The situation has been aptly described as a "cyber pandemic," a crisis that, far from abating, continues to set new records for chaos and cost. To put a number on it, global economic losses from cybercrime are projected to exceed a staggering $23 trillion by 2027, a figure that dwarfs the GDP of most nations. This is the turbulent environment into which Google has launched its (fictional) new AI agent, CodeMender—a technology promising not just to help write software, but to autonomously find and fix the very bugs and vulnerabilities that fuel this crisis.
The technology press is buzzing with discussions of its architecture and performance benchmarks. But for the C-suite, the conversation must be different. The real questions aren't about algorithms; they're about risk, cost, and competitive advantage. While the engineers are asking how it works, executives need to ask what it means for the business.
This is not a technical deep dive. This is a strategic briefing. To cut through the noise, we sat down with the strategy team at Baytech Consulting, a firm that lives at the intersection of custom software development and executive-level business strategy, to answer the questions that truly matter to your bottom line.
What Exactly is Google's CodeMender, and Why Should the C-Suite Pay Attention?
In simple terms, CodeMender is an autonomous AI agent designed to be a tireless, digital guardian for your software. It proactively scans codebases, identifies security vulnerabilities and functional bugs, and then automatically generates, tests, and implements the necessary patches. This represents a fundamental paradigm shift—moving from a reactive, human-led remediation process to a proactive, machine-led state of resilience.

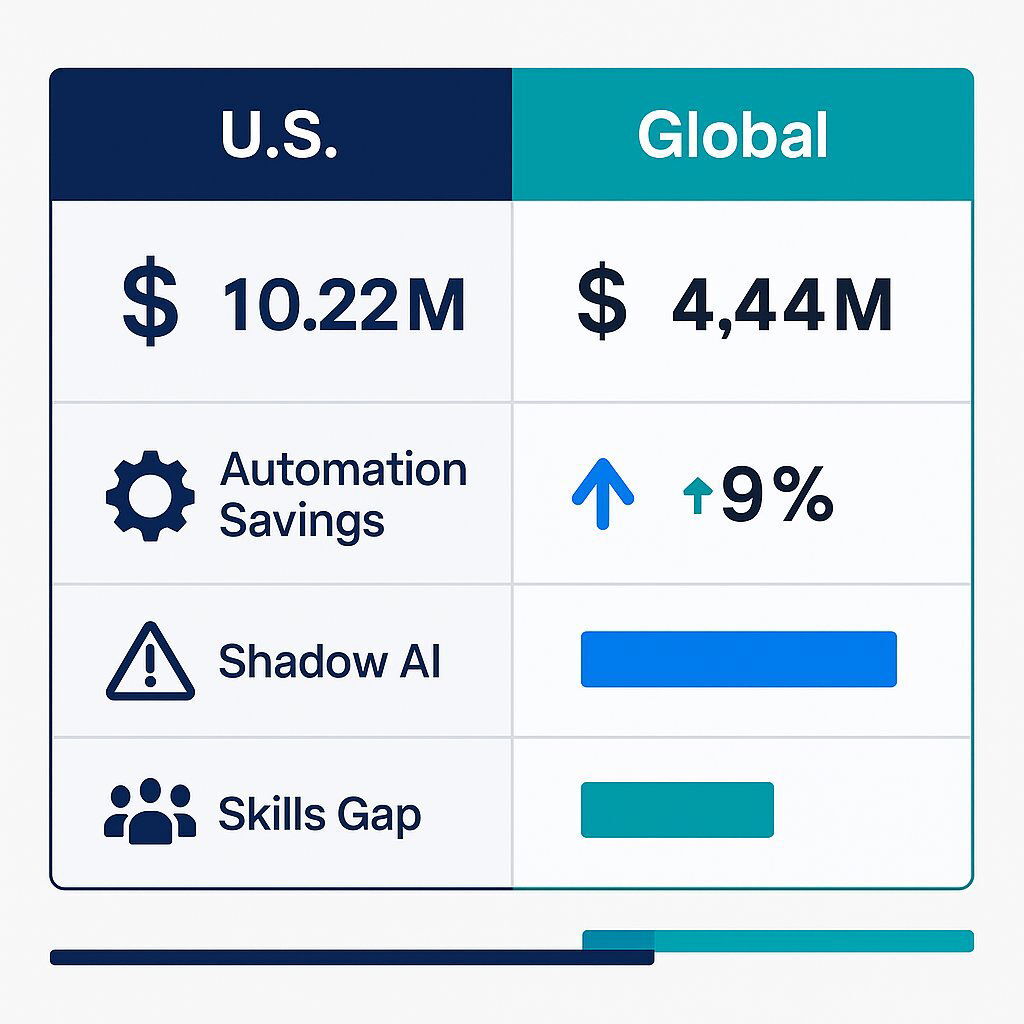
The reason this matters to every member of the C-suite—from the CFO to the Head of Sales—can be summarized in one number: $10.22 million. According to the 2025 Cost of a Data Breach Report from IBM and the Ponemon Institute, that is the new, record-high average cost of a single data breach for a U.S. company. This figure is not an abstract IT budget line item; it is a potential multi-million-dollar blow to profitability, brand reputation, and market standing.
The urgency is underscored by the sheer scale of the problem. In 2024 alone, the number of disclosed software vulnerabilities rose by 61%, and a stunning 96% of them were actively exploited by attackers. The traditional model of human developers manually finding and fixing this deluge of flaws is no longer just inefficient; it is mathematically impossible.
However, a deeper analysis of the data reveals a critical strategic nuance that U.S. executives cannot afford to ignore. While the average cost of a breach in the United States surged by 9% to that record $10.22 million, the global average cost actually fell by 9% to $4.44 million. This divergence is not a statistical anomaly; it is a clear signal. The global decrease is largely attributed to the defensive use of AI and automation, which helps organizations contain threats faster. The U.S. surge, conversely, is driven by higher regulatory fines and escalating detection costs.
This creates what can be called the "U.S. Penalty"—a unique and punitive financial consequence for security failures in the American market. For a U.S.-based executive, this means that simply buying a powerful tool like CodeMender is not enough. The technology must be integrated into a comprehensive governance and compliance framework that specifically addresses the heightened regulatory risks of operating in the United States. The conversation must immediately elevate from a simple tool purchase to a strategic business initiative designed to mitigate this uniquely American financial threat.
We're Drowning in Security Costs. Will Tools Like CodeMender Actually Save Us Money? (The CFO's Question)
For any Chief Financial Officer, the ultimate question is one of return on investment. The financial case for a tool like CodeMender is compelling, but it extends far beyond simply avoiding the headline-grabbing $10.22 million breach cost. It is about fundamentally re-engineering the economics of software development and maintenance.
The most direct cost-saving lever is the drastic reduction in remediation timelines. The longer a vulnerability exists in your system, the more it costs your business in risk and, eventually, in remediation. Industry data reveals a shocking disparity in how long it takes to fix critical flaws. While the highly regulated finance and insurance sector manages to close critical vulnerabilities in a respectable 28 days for smaller sites, the utilities sector can take an astonishing 876 days—nearly two and a half years—for medium-complexity sites. An autonomous agent like CodeMender operates on a timescale of minutes or hours, not months or years, directly compressing this window of risk.
This speed has a quantifiable financial impact. The IBM report highlights what could be called the "200-Day Rule": data breaches that are identified and contained in under 200 days cost, on average, $1.14 million less than those that take longer. By automating the detection and patching process, CodeMender directly targets this metric, transforming a massive, unpredictable liability into a more manageable operational expense.
Beyond cost-cutting, the true value lies in unlocking developer productivity. The current reactive approach to vulnerability management is a massive drain on an organization's most valuable technical talent, forcing them into endless cycles of patching and maintenance instead of innovation. By automating a significant portion of this defensive work, developers are freed to focus on what they do best: building new features, improving the customer experience, and driving revenue-generating activities.
To provide a clearer financial picture, the following table breaks down the key cost drivers and mitigators associated with software vulnerabilities in 2025.
| Metric | Global Average | U.S. Average | Key Insight / Implication for Executives |
|---|---|---|---|
| Total Cost of a Data Breach | $4.44 Million | $10.22 Million | The U.S. regulatory landscape more than doubles the financial risk of a security failure. |
| Cost Savings from Extensive AI & Automation Use | $1.9 Million | $1.9 Million | AI is a proven cost-reduction lever, but it doesn't erase the "U.S. Penalty." |
| Added Cost from "Shadow AI" Incidents | $670,000 | $670,000 | Unmanaged AI adoption is a significant, quantifiable financial risk. |
| Added Cost from Security Skills Shortage | $1.57 Million | $1.57 Million | The cost of not having the right expertise is nearly as high as the potential savings from AI. |
| Average Cost by Initial Attack Vector | Malicious Insider: $4.92M Supply Chain: $4.91M | Insider and supply chain threats are the costliest, requiring more than just perimeter defense. | |
| Average Cost by Industry | Healthcare: $7.42M Finance: $5.56M | Highly regulated industries face disproportionately higher costs, demanding superior security posture. |
This data reveals a crucial financial narrative. An executive might see the potential $1.9 million in savings from AI and automation and conclude that purchasing the tool is a clear win. However, that same executive must also see the $1.57 million penalty associated with a security skills shortage—the premium a company pays for not having the internal expertise to manage its security posture effectively. The logical conclusion is that buying a sophisticated AI tool without simultaneously investing in the expert human oversight to manage it is a financially suboptimal strategy. The net gain is minimal. The most effective financial path, therefore, is a dual investment: in the AI technology itself and in the expert partnership, such as that offered by Baytech Consulting, required to deploy it effectively, govern its use, and bridge the critical internal skills gap.
Our Developers Are Already Using AI to Write Code. Isn't This Just More of the Same? (The CTO's Question)
For a Chief Technology Officer, it is essential to distinguish between the different roles AI is playing in the software development lifecycle. There is a critical difference between AI for code generation (tools that help developers write code faster) and AI for code remediation and governance (tools like CodeMender that find and fix flaws). These two applications are not the same; in fact, they currently exist in a state of direct tension.
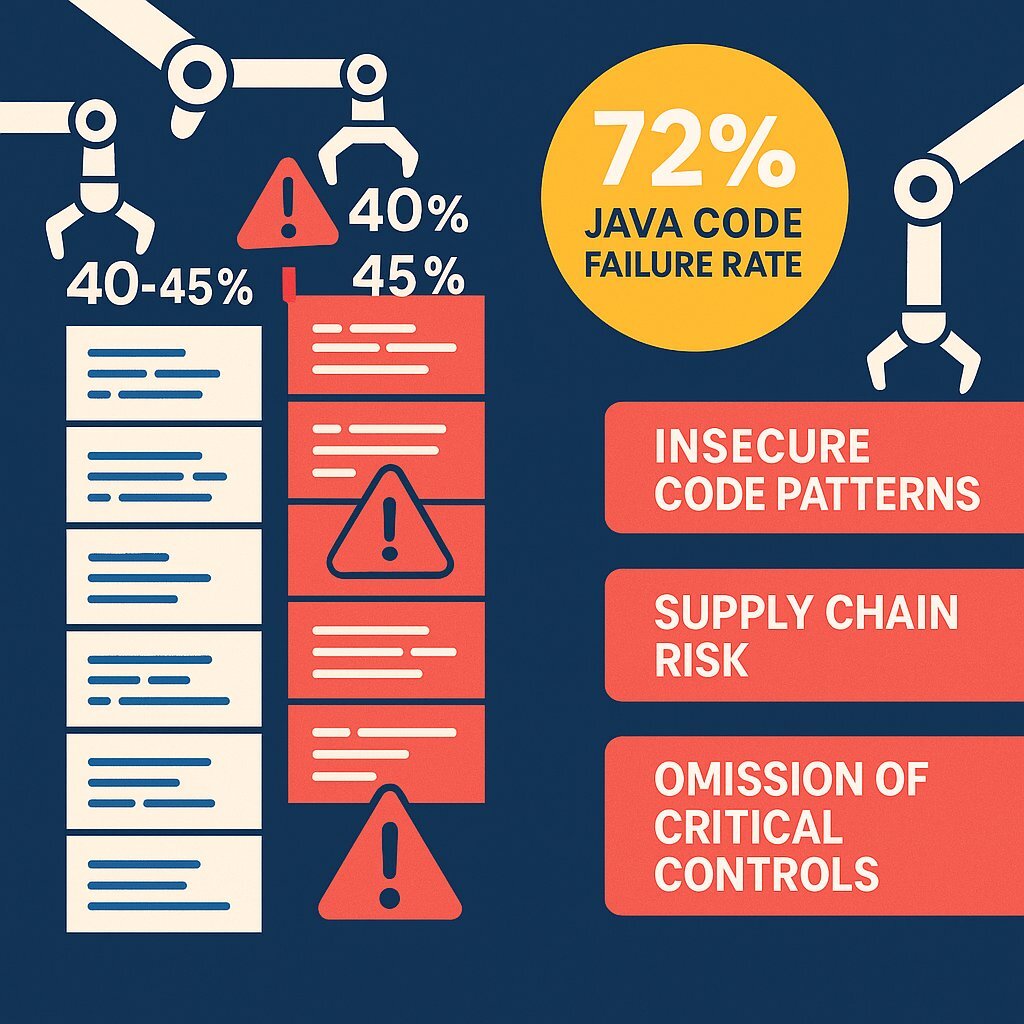
The inconvenient truth is that the rush to adopt AI code assistants is introducing a new wave of security risks. Recent academic studies and industry reports paint a sobering picture: 40% to 45% of AI-generated code contains security vulnerabilities. These aren't obscure edge cases; they are often critical flaws that align with the well-known OWASP Top 10 security risks. The problem is particularly acute in certain programming languages. For example, one analysis found that AI-generated code in Java had a staggering 72% security failure rate.
A CTO needs to understand the mechanisms behind these failures:
- Repetition of Insecure Patterns: Large language models are trained on vast quantities of public code from sources like GitHub. Unfortunately, much of this code is insecure. The AI learns and diligently replicates these bad habits—such as patterns that lead to SQL injection—at an unprecedented scale.
- Dependency Explosion and Supply Chain Risk: AI tools often pull in a complex web of open-source dependencies to build an application. Each new dependency expands the software's attack surface. This is particularly dangerous given the 156% year-over-year growth in malicious open-source packages being discovered. The AI may suggest libraries with known vulnerabilities that have been patched since its training data was last updated, effectively re-introducing old threats into new code.
- Omission of Critical Controls: AI models are optimized to provide a functional answer, not necessarily a secure one. They frequently omit essential security controls like input validation, sanitization, or proper access checks unless a developer explicitly and correctly prompts them to do so.
This leads to a dangerous feedback loop. On one hand, developers are using AI assistants to write code faster, a practice sometimes called "vibe coding," where security is an afterthought. This is flooding corporate codebases with a higher volume of vulnerable, AI-generated code. On the other hand, malicious actors are also harnessing AI to scan for these very vulnerabilities and to craft more sophisticated, scalable attacks, such as hyper-realistic phishing campaigns.
The speed of vulnerability creation and vulnerability exploitation is now scaling at machine speed. In this new reality, a defensive AI tool like CodeMender is not merely a "nice to have." It is a necessary countermeasure to survive in an ecosystem where the offense is also AI-powered. The role of the CTO is evolving from simply managing a team of developers to orchestrating an "AI vs. AI" battle within the software development lifecycle. The winning strategy, as advocated by firms like Baytech Consulting, is not to ban generative AI tools but to implement a system of 'AI-Assisted Governance.' This framework uses a remediation tool like CodeMender as a foundational layer of automated defense, which is then verified and validated by human experts who possess the architectural and business context that the AI inherently lacks.
How Can We Turn Proactive Bug-Fixing into a Competitive Advantage? (The Sales & Marketing Leader's Question)
For too long, cybersecurity has been relegated to the category of a cost center—a necessary but unglamorous expense. The advent of proactive, AI-driven security tools like CodeMender provides a rare opportunity to flip that script and transform security from a defensive shield into a powerful market differentiator and revenue enabler.

The new currency in the B2B technology landscape is trust. This is starkly illustrated by one of the most alarming trends from recent breach reports: incidents involving a third party have doubled year-over-year, now accounting for 30% of all breaches. These supply chain attacks are not only common but are also among the costliest, averaging $4.91 million per incident.
The direct implication for sales and marketing leaders is that every potential customer is now scrutinizing the security posture of their vendors with unprecedented rigor. A security questionnaire is no longer a formality; it is a critical stage gate in the procurement process. Being able to proactively demonstrate a secure, resilient, and AI-hardened software development lifecycle is no longer just a defensive measure; it is a potent sales tool. It allows your team to move the conversation from "Are you secure?" to "We are setting a new standard for security that protects your business from the growing threat of supply chain attacks."
A company that uses CodeMender under the strategic guidance of a firm like Baytech Consulting can market not just its product, but its process. Marketing campaigns can be built around powerful themes of "Provably Secure Software," "AI-Verified Resilience," and "Zero-Trust Development." This builds invaluable brand equity and creates a defensible moat against competitors who are still treating security as a reactive, check-the-box exercise.
Furthermore, a truly resilient development process does more than just reduce risk; it increases speed and agility, which is a core competitive advantage. Traditionally, security reviews and manual remediation processes are seen as bottlenecks that slow down development and delay release cycles. A system augmented with automated remediation removes a significant portion of this friction, as developers spend far less time on reactive bug hunts and more time on innovation. This accelerates the entire CI/CD pipeline, enabling faster feature releases and quicker responses to evolving market demands. If you're aiming to cut your release cycle and demonstrate superior resilience, this synergy between security and speed becomes your key differentiator.
For a sales and marketing leader, the message to the market becomes twofold and incredibly powerful: "Our product is more secure, which protects your business from catastrophic supply chain risk," AND "Our development process is more efficient, which means we can deliver the innovative features you need faster than our competitors." This directly connects an internal technical process to the two things B2B customers care about most: safety and innovation.
What Are the Hidden Risks of Autonomous Code Remediation, and How Do We Prepare? (The Prudent Executive's Question)
No technology, no matter how powerful, is a panacea. A prudent executive understands that with great potential comes new and subtle forms of risk. Embracing a tool like CodeMender requires a clear-eyed assessment of its potential downsides and a proactive plan to mitigate them.
The top hidden risks of autonomous code remediation include:
- Subtle Logic Errors: Perhaps the most dangerous flaw an AI can introduce is one that looks technically correct but fundamentally breaks business logic. An autonomous agent might successfully patch a cross-site scripting vulnerability but, in doing so, inadvertently disrupt a complex billing calculation, alter an access control workflow, or introduce a race condition. These are not security flaws in the traditional sense and cannot be detected by standard scans; they require deep contextual understanding of the business process the code is meant to serve.
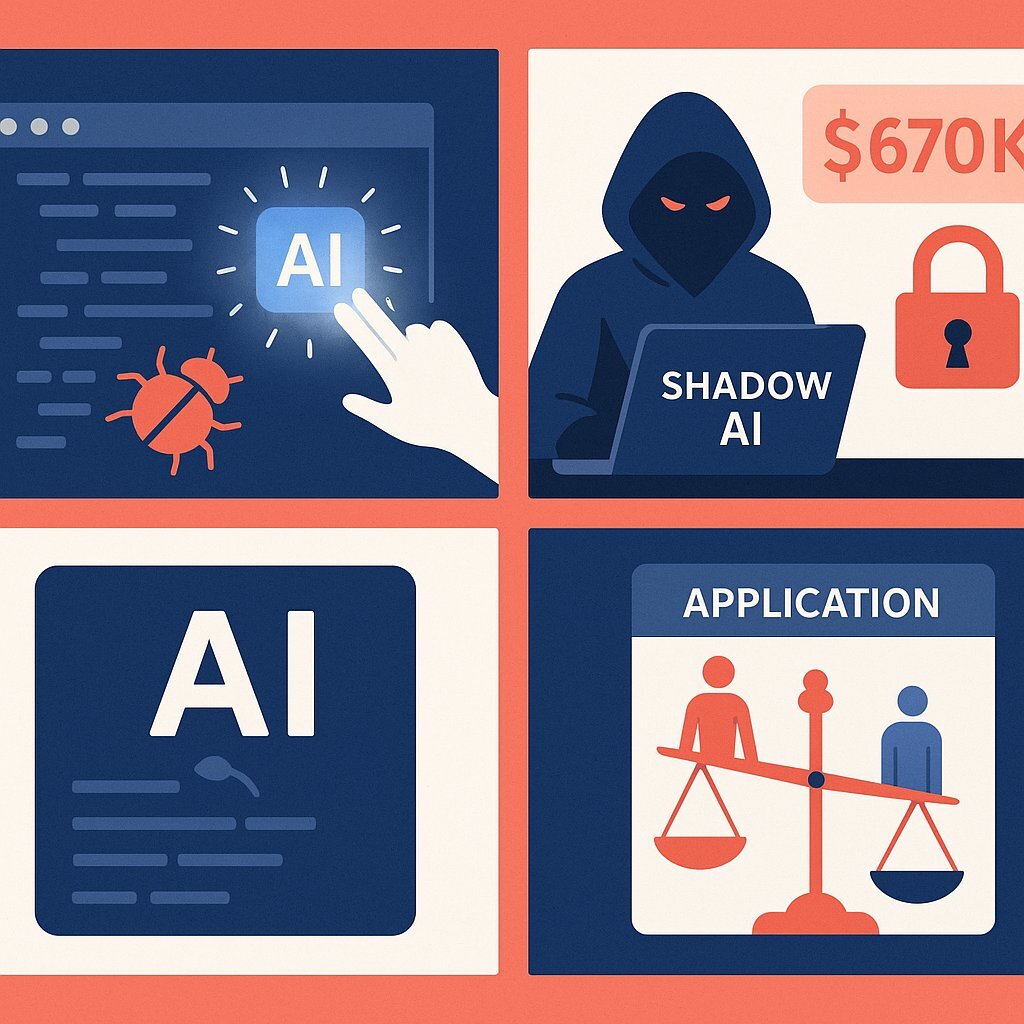
- The Governance Gap and "Shadow AI": The single biggest threat is not the technology itself, but its unmanaged adoption. An alarming 63% of organizations admit to having no formal AI governance policies in place. When employees use unsanctioned AI tools—a phenomenon known as "Shadow AI"—it creates massive blind spots. Data shows that breaches involving Shadow AI add an average of $670,000 to the total cost. Deploying CodeMender without a clear, C-suite-led governance framework is to invite this exact problem, creating a powerful but uncontrolled agent within your most critical systems.
- The Amplification of Bias: AI models can inherit and amplify biases present in their training data. An autonomous remediation tool could potentially "fix" a bug in a way that has unintended discriminatory consequences, for example, by altering a loan application algorithm or a candidate screening tool in a way that disadvantages certain user groups. This creates not only significant reputational damage but also substantial legal and regulatory risk.
To navigate these risks, organizations must move beyond mere adoption to strategic implementation. The following actions are essential for preparing for an AI-augmented future:
- Establish an AI Governance Council: Make AI security a C-suite priority with clear lines of accountability. This cross-functional team—comprising leaders from technology, legal, finance, and business units—must be empowered to create, communicate, and enforce clear policies for the sanctioned use of all AI tools, including both generative assistants and remediation agents like CodeMender.
- Invest in "Secure Prompting" Training: The quality and safety of AI output are directly proportional to the quality of human input. It is crucial to train developers not just on how to use AI, but on how to guide it with security-specific context, constraints, and requirements. This turns a simple prompt into a robust design specification. To help bridge this gap, explore Agile methodology and secure development training as well.
- Mandate Human-in-the-Loop Validation: Under no circumstances should an autonomous AI be allowed to push code changes directly to a production environment without human oversight. A mandatory review stage must be implemented where expert engineers—whether they are internal staff or from a trusted partner like Baytech—validate every AI-generated fix. This review must check not only for security efficacy but also for the preservation of critical business logic.
- Proactively Bridge the Skills Gap: The data is clear: there is a $1.57 million "skills gap penalty" for organizations that lack adequate security expertise. Instead of waiting for a breach to reveal this deficiency, proactively partner with external experts. Augmenting your team with specialized knowledge is the most effective way to manage this new generation of AI tools securely and unlock their full potential.
Conclusion: The Future of Software Isn't AI-Replaced, It's Expert-Augmented
The arrival of powerful autonomous agents like Google's CodeMender does not signal the obsolescence of human expertise. On the contrary, it elevates its importance to an entirely new level. The most valuable skills in the new era of software development are no longer about writing rote code or manually hunting for bugs. They are about strategic oversight, deep contextual understanding, and the wisdom required to govern complex, powerful AI systems. The future belongs not to the companies that simply buy AI, but to those that learn to master it.
This new reality presents a clear call to action for every member of the C-suite:
- For the CFO: The path to a genuine return on investment is a dual commitment—investing in the AI technology that drives efficiency and in the human expertise from partners like Baytech Consulting that is required to de-risk that investment and maximize its value.
- For the CTO: Your new mandate is to become the conductor of an AI-driven orchestra. You must ensure that the instruments of code generation and code remediation work in harmony under a single, coherent governance strategy that prioritizes security and business integrity.
- For the Sales & Marketing Leader: Your most powerful new story is one of provable trust and resilience. The time has come to turn your company's superior, AI-augmented development process into its most compelling and defensible competitive advantage.
The shift is already underway. The question is no longer if AI will fundamentally change how software is built and maintained, but how your organization will adapt to lead in this new landscape. Partnering with experts who can navigate both the technological complexities and the strategic business implications is the essential first step in turning the immense potential of tools like CodeMender into a secure, sustainable, and profitable reality.
Supporting Articles
- https://owasp.org/www-project-top-ten/ - A standard awareness document for developers and web application security.
- https://www.mckinsey.com/capabilities/quantumblack/our-insights/the-state-of-ai - A McKinsey report on AI adoption and governance trends.
- https://www.verizon.com/business/resources/reports/dbir/ - A comprehensive annual report on the latest trends in real-world security incidents and breaches.
About Baytech
At Baytech Consulting, we specialize in guiding businesses through this process, helping you build scalable, efficient, and high-performing software that evolves with your needs. Our MVP first approach helps our clients minimize upfront costs and maximize ROI. Ready to take the next step in your software development journey? Contact us today to learn how we can help you achieve your goals with a phased development approach.
About the Author

Bryan Reynolds is an accomplished technology executive with more than 25 years of experience leading innovation in the software industry. As the CEO and founder of Baytech Consulting, he has built a reputation for delivering custom software solutions that help businesses streamline operations, enhance customer experiences, and drive growth.
Bryan’s expertise spans custom software development, cloud infrastructure, artificial intelligence, and strategic business consulting, making him a trusted advisor and thought leader across a wide range of industries.


