
SaaS Authentication Strategies: Hybrid Login, Security & User Data
November 18, 2025 / Bryan Reynolds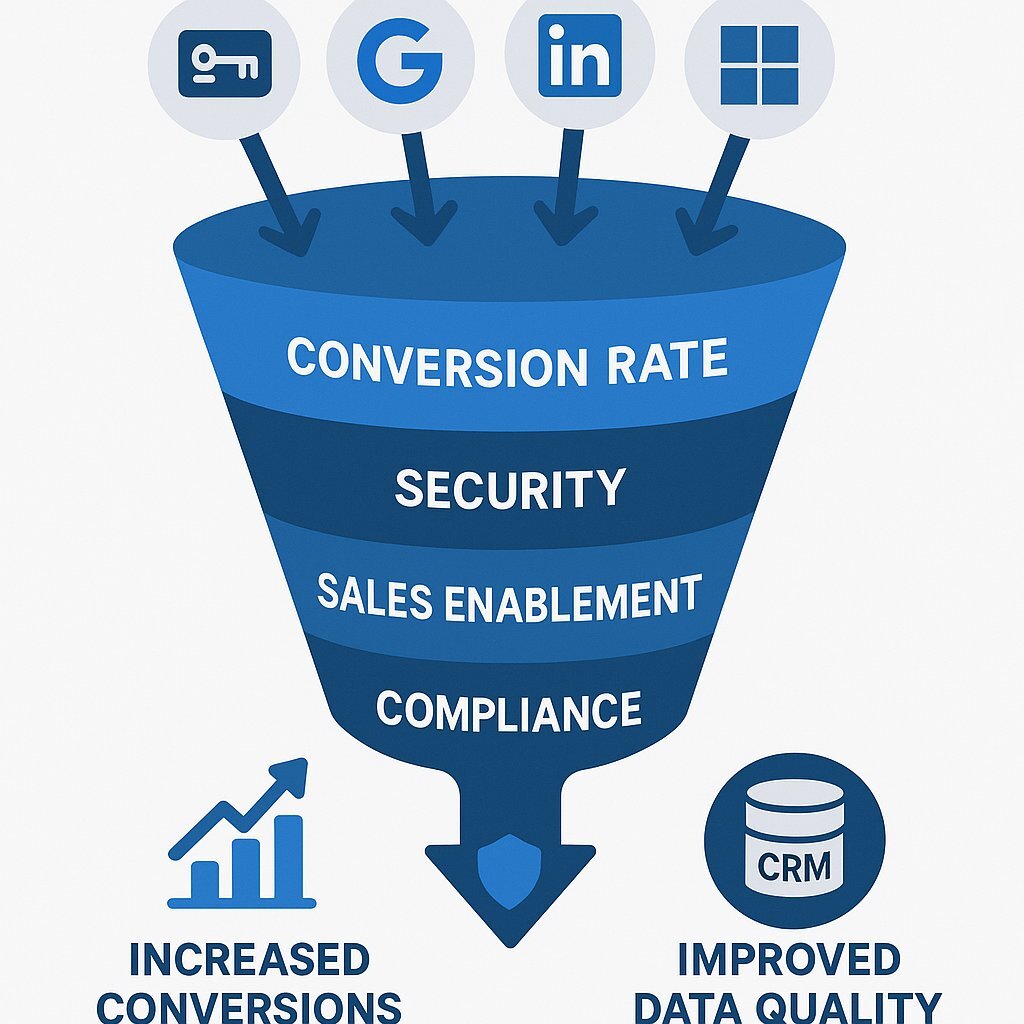
Should SaaS Products Offer Traditional Account Creation or Rely Only on Social Login? A 2025 Strategic Guide for B2B Leaders
Every SaaS executive eventually hits this same question:
“Do our users actually want to create a new username and password anymore—or should we just push everyone into Google, Microsoft, or LinkedIn login?”
It seems simple. It isn’t.
In 2025, authentication strategy has become one of the biggest drivers of conversion, security, enterprise readiness, and long-term technical scalability. And for companies moving upmarket—or trying to accelerate growth—getting this decision wrong quietly kills revenue.
This article breaks down the real data, user psychology, and enterprise expectations behind authentication so you can make a strategic choice rooted in facts, not assumptions.
As background: Baytech Consulting builds complex B2B applications and manages enterprise-grade software platforms across finance, education/LMS, healthcare, high-tech, and fast-scaling startups. Authentication is a challenge we solve repeatedly—across Kubernetes architectures, Postgres infrastructure, and modern SaaS stacks.
Why This Question Matters More Than Most SaaS Teams Realize
Authentication is no longer a UX detail. It’s a growth lever, a security perimeter, a sales enablement requirement, and—eventually—a compliance obligation.
Three pressures collide:
- Users want frictionless access (especially on mobile).
- CISOs demand tighter identity security after major token-theft breaches.
- CFOs track the cost of every lost signup and every password-reset ticket.
The decision you make affects:
- Visitor-to-signup conversion
- Security exposure
- Enterprise SSO readiness
- Your CRM data quality
- Your long-term infrastructure cost
Let’s break it down.
1. What Users Actually Want: The Psychology Behind Authentication
The Problem With Forcing Users to Create a Password
Users are exhausted by credential management.
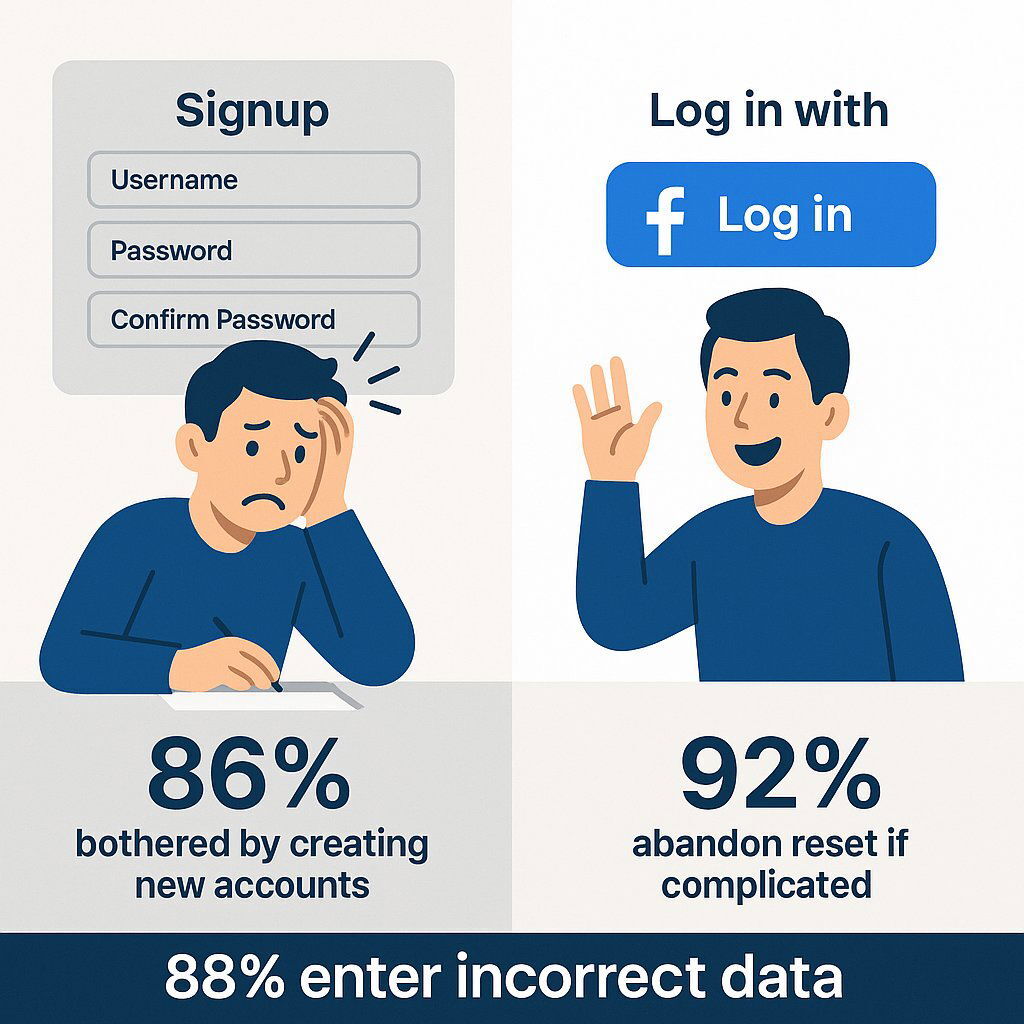
| User Behavior / Sentiment | Data Point |
|---|---|
| Users bothered by creating new accounts | 86% |
| Users abandoning complicated password resets | 92% |
| Users entering fake/incorrect registration data | 88% |
Why it matters:
Traditional signup isn’t just friction—it produces bad data. That bad data pollutes CRMs, kills segmentation accuracy, and makes personalization nearly impossible.
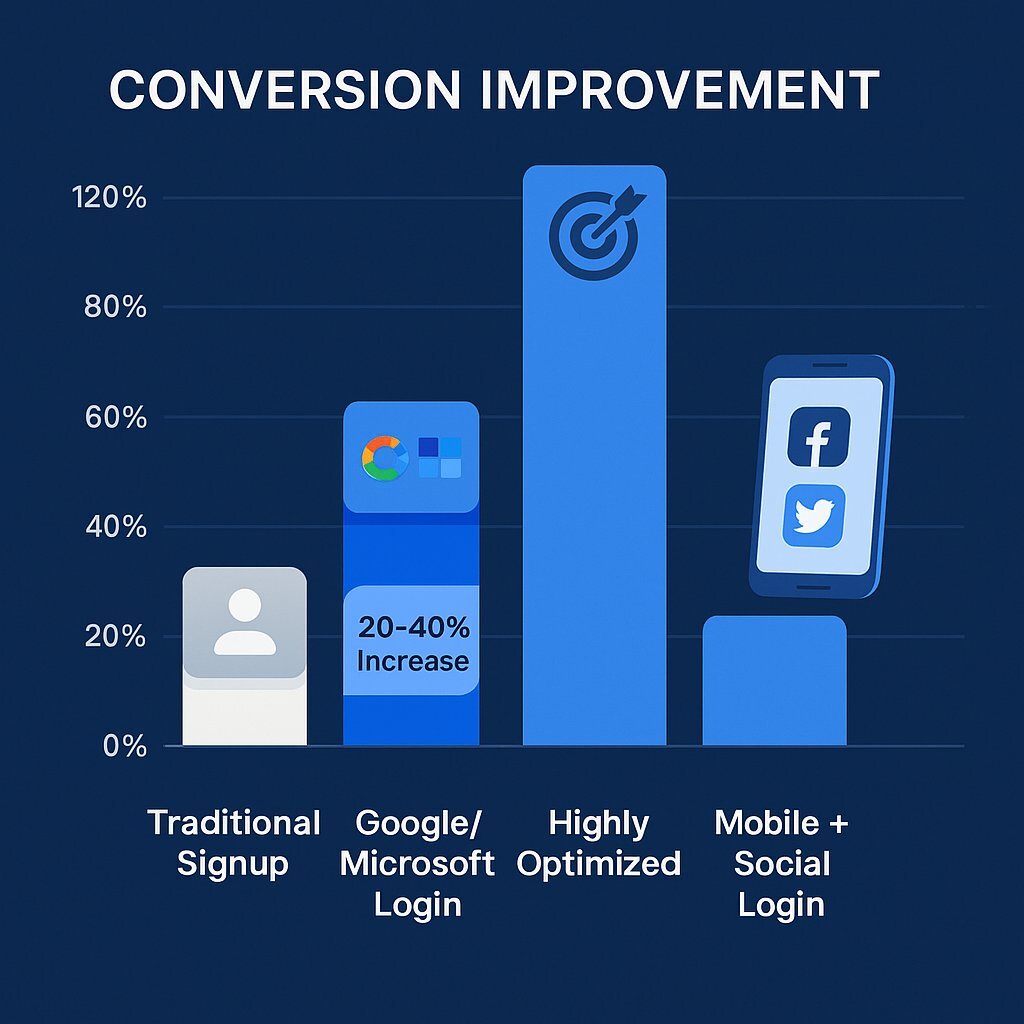
Why Social Login Converts Better
Social/SSO login removes cognitive load and minimizes clicks.
| Authentication Method | Conversion Impact |
|---|---|
| Google / Microsoft Login | 20%–40% uplift |
| Highly optimized implementations | Up to 130% uplift |
| Mobile forms with social login | Significantly reduced abandonment |
But here’s the catch: not all users trust social login, especially in B2B environments where personal and professional identities blur.
2. Why Social-Only Login is a Strategic Mistake
Many product teams assume:
“If social login is easier, let’s remove email/password entirely.”
This is a costly error.
2.1 Privacy-Conscious Users Refuse Social Login
A meaningful portion of B2B users do not want to link personal Google, Microsoft, or LinkedIn accounts.
Reasons include:
- Perceived data sharing
- Distrust of OAuth permissions
- Desire to keep work and personal identities separate
You lose these users instantly.
2.2 You Create a Single Point of Failure
If your sole authentication provider goes down:
- All users are locked out
- Support queues explode
- Productivity halts
- Enterprise customers may enforce SLA penalties
This is not hypothetical. Major IdP outages have globally impacted SaaS access.
2.3 Centralizing Identity Raises Security Stakes
If an attacker compromises a user’s Google/Microsoft password, every connected application becomes vulnerable.
High-security users demand independent credentials for certain platforms.
3. The Hybrid Authentication Model: The 2025 Best Practice
The data is conclusive:
Offering BOTH social login and email/password converts 8.5% more users than offering just one.
This hybrid model captures:
- Convenience-first users
- Privacy-first users
- Enterprise users with SSO needs
- Mobile users who want instant access
- Power users who want account autonomy
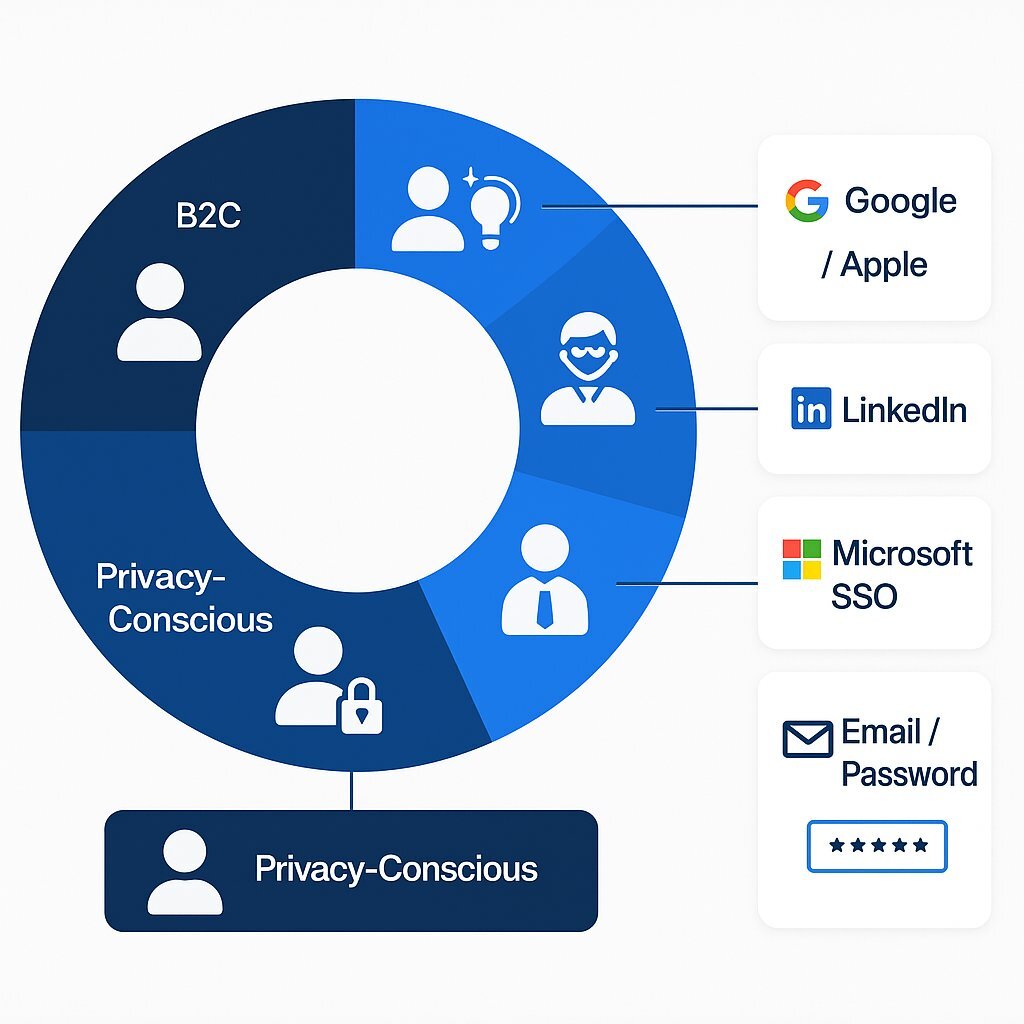
User Preference Breakdown (2025)
| User Type | Preferred Login Method | Why It Matters |
|---|---|---|
| B2C / general users | Google / Apple | Speed |
| Startup teams | Google Workspace | Existing corporate identity |
| Professional SaaS | Verified employment data | |
| Enterprise | Microsoft Entra ID (Azure AD) SSO | Security + compliance |
| Privacy-conscious | Email/password or Magic Link | Control |
The Hybrid Model is no longer optional. It’s the new standard.

4. Strategic Recommendations by SaaS Audience
B2C or Prosumer SaaS
- Google Login
- Apple Login (if mobile focus)
- Traditional email/password
- Optional: Magic Link
Goal → Maximize signups and reduce mobile friction.
B2B SaaS (SMB → Mid-Market)
- LinkedIn (critical for professional identity validation)
- Email/password
- Optional: Magic Link
Goal → Improve data quality and accelerate onboarding.
Enterprise SaaS (Mid-Market → Fortune 500)
- Microsoft Entra ID SSO (mandatory)
- SAML/OIDC connections
- SCIM provisioning
- Email/password fallback (for break-glass access)
Goal → Win procurement and meet compliance obligations.
5. Data Integrity: The Hidden Reason Authentication Matters
Social and SSO logins do more than reduce friction—they improve data accuracy.
| Input Method | Data Quality | Notes |
|---|---|---|
| Manual form | Low | Users lie, rush, or mistype |
| Google OAuth | High | Verified email + basic profile |
| Microsoft SSO | Very High | Corporate identity |
| LinkedIn OAuth | Excellent | Verified job title, company, industry |
| SCIM provisioning | Enterprise-grade | Real-time lifecycle accuracy |
For industries like finance, education, healthcare, and real estate—accurate user data is essential.
6. Security Considerations: The 2025 Threat Landscape
Password cracking is no longer the main attack vector—token theft is.
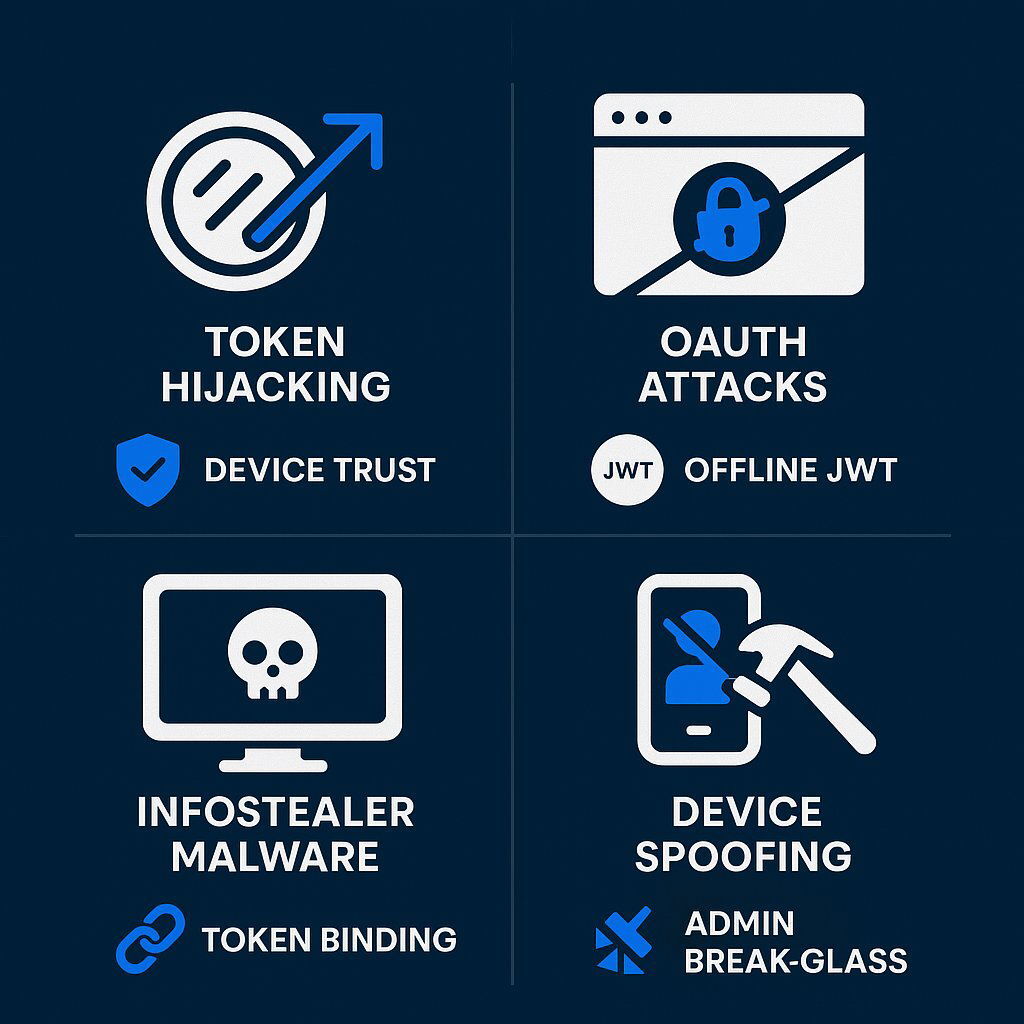
Modern threats include:
- Session token hijacking
- OAuth token replay
- Infostealer malware
- Device impersonation
To counter these, B2B SaaS platforms must implement:
- Device Trust
- Token binding
- Behavioral signal scoring
- Offline JWT validation
- Break-glass admin accounts
A hybrid model makes these architectural patterns easier to implement—see this DevSecOps executive guide for more on proactive security culture.
Conclusion: So, What Do Users Actually Want?
Users want choice.
And your business needs resilience.
The best-performing SaaS platforms offer:
- Google / Microsoft / LinkedIn Login for convenience and accuracy (discover how enterprises leverage these options with AI transformation in law firms and similar high-compliance fields)
- Email/password or Magic Link for autonomy and reliability
- Enterprise SSO (SAML/OIDC) when selling to larger clients
This hybrid strategy maximizes conversion, improves security posture, supports enterprise sales, and future-proofs your identity architecture. For a deeper exploration of the change management and best practices behind this, read these software project management tips.
Next Steps for SaaS Executives
- Audit your current authentication flow for drop-off points. If you're considering moving upmarket, our step-by-step advice on aligning your IT roadmap with business goals can help build lasting improvements.
- Add the missing login options matched to your market segment.
- Build toward SSO + SCIM for enterprise readiness—review software maintenance strategies to assure long-term quality and scalability.
- Invest in a modern identity provider (Auth0, Cognito, Supabase, Kinde, Clerk). To get the project scope and cost right, check out mastering software scoping before your next build.
Baytech Consulting frequently helps firms modernize authentication—whether integrating SSO, restructuring identity architecture, or eliminating UX friction as part of custom B2B application development.
Frequently Asked Question
Should we let users create their own username and password, or push everyone into Google/Microsoft login?
Yes, you should always allow users to create their own account.
And yes, you should offer Google/Microsoft/LinkedIn login too.
A hybrid strategy delivers the highest conversion, the best user trust, and the resilience your platform needs. Stay tuned for insights about the automation paradox in AI and the continued need for human oversight in software platforms.
Further Reading
- Why Social Login Boosts SaaS Conversion Rates
- Understanding Modern Identity Threats and Token Theft
- Enterprise SSO and SCIM: What Mid-Market SaaS Companies Must Know
About Baytech
At Baytech Consulting, we specialize in guiding businesses through this process, helping you build scalable, efficient, and high-performing software that evolves with your needs. Our MVP first approach helps our clients minimize upfront costs and maximize ROI. Ready to take the next step in your software development journey? Contact us today to learn how we can help you achieve your goals with a phased development approach.
About the Author

Bryan Reynolds is an accomplished technology executive with more than 25 years of experience leading innovation in the software industry. As the CEO and founder of Baytech Consulting, he has built a reputation for delivering custom software solutions that help businesses streamline operations, enhance customer experiences, and drive growth.
Bryan’s expertise spans custom software development, cloud infrastructure, artificial intelligence, and strategic business consulting, making him a trusted advisor and thought leader across a wide range of industries.


