
Why Boards Must Treat Cybersecurity as Business Risk: A 2025 Guide
October 01, 2025 / Bryan Reynolds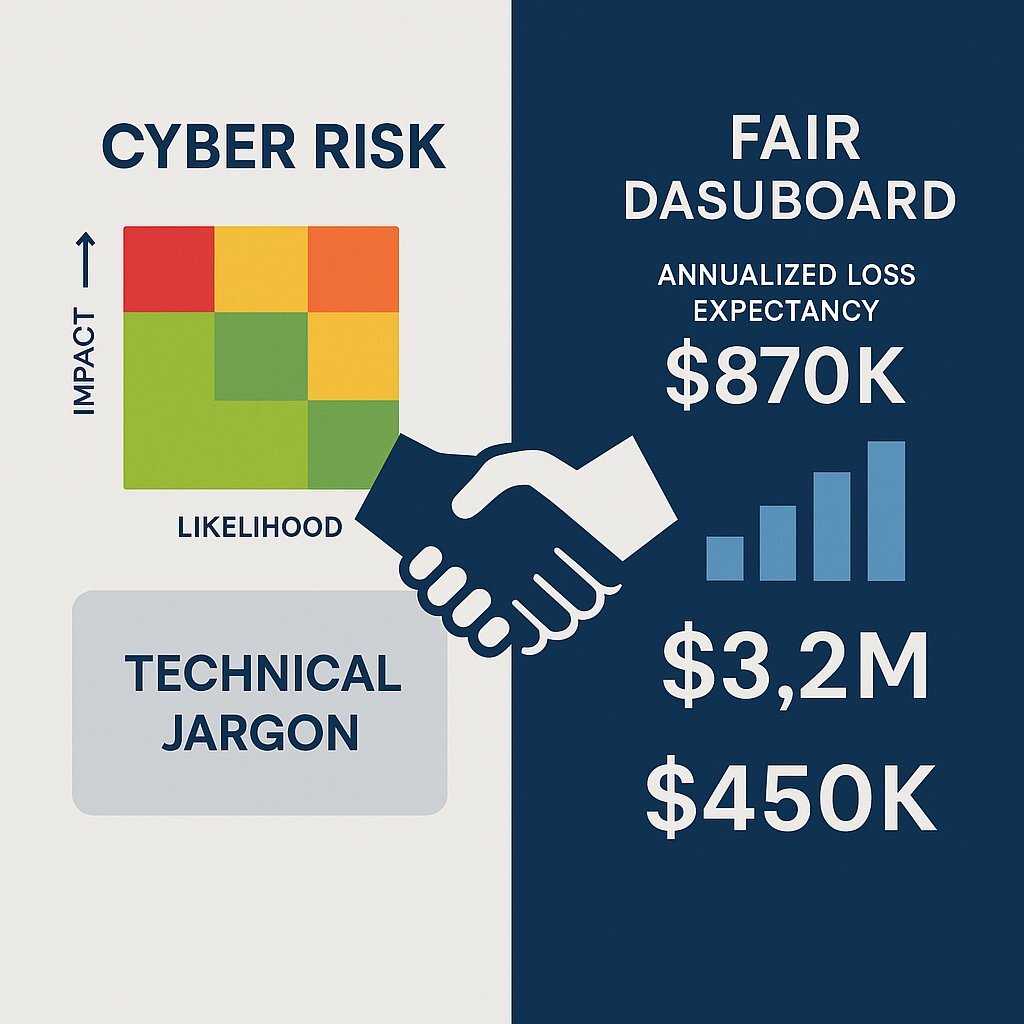
Cybersecurity is a Board-Level Issue: A Guide for Translating Cyber Risk into Business Risk
Introduction: Beyond the Firewall - Why Cyber Risk is Now Business Risk
Modern enterprises are navigating a critical paradox. The digital transformation that fuels growth and innovation has simultaneously created an expanding and complex attack surface. According to IBM's 2024 Cost of a Data Breach Report, the consequence of this exposure has never been more severe; the average global cost of a breach has surged by 10% to an all-time high of USD 4.88 million. Yet, as the financial stakes escalate, a 2024 survey from IANS and Artico Search reveals that security budget growth is slowing. The overall growth rate of 8% is roughly half of the levels seen in 2021 and 2022, creating immense pressure on leadership to do more than just spend—they must invest strategically and demonstrate a clear return on security investment.
This environment exposes a dangerous vulnerability, one that exists not in code but in communication. The persistent gap between the technical vernacular of security teams and the financial language of the boardroom is no longer a mere inconvenience; it has become a significant business liability. To bridge this divide, cybersecurity must be reframed from a technical cost center into a strategic business function. The conversation must evolve beyond vulnerabilities and patches to the universal language of business: financial exposure, operational resilience, and reputational integrity.
This article serves as a strategic guide for Chief Information Officers (CIOs), Chief Information Security Officers (CISOs), and Board Members. It provides a data-backed framework for quantifying cyber risk, understanding the transformative impact of Artificial Intelligence (AI), and making defensible, value-driven security decisions. Throughout this complex journey of strategic realignment, expert guidance is paramount. Firms like Baytech Consulting work with executive teams to implement these advanced risk management frameworks, ensuring that cybersecurity strategy is fully integrated with and enables core business objectives.
Section 1: The Tangible Costs of an Intangible Threat: A 2024 Perspective
To effectively govern risk, the board and C-suite must first grasp its true, multi-faceted cost. The headline number of a data breach is merely the tip of the iceberg; the real damage lies beneath the surface in operational paralysis, supply chain disruption, and the long-term erosion of brand equity and customer trust. A deeper analysis of breach costs reveals that the primary financial impact is now directly tied to business operations, not just IT remediation.
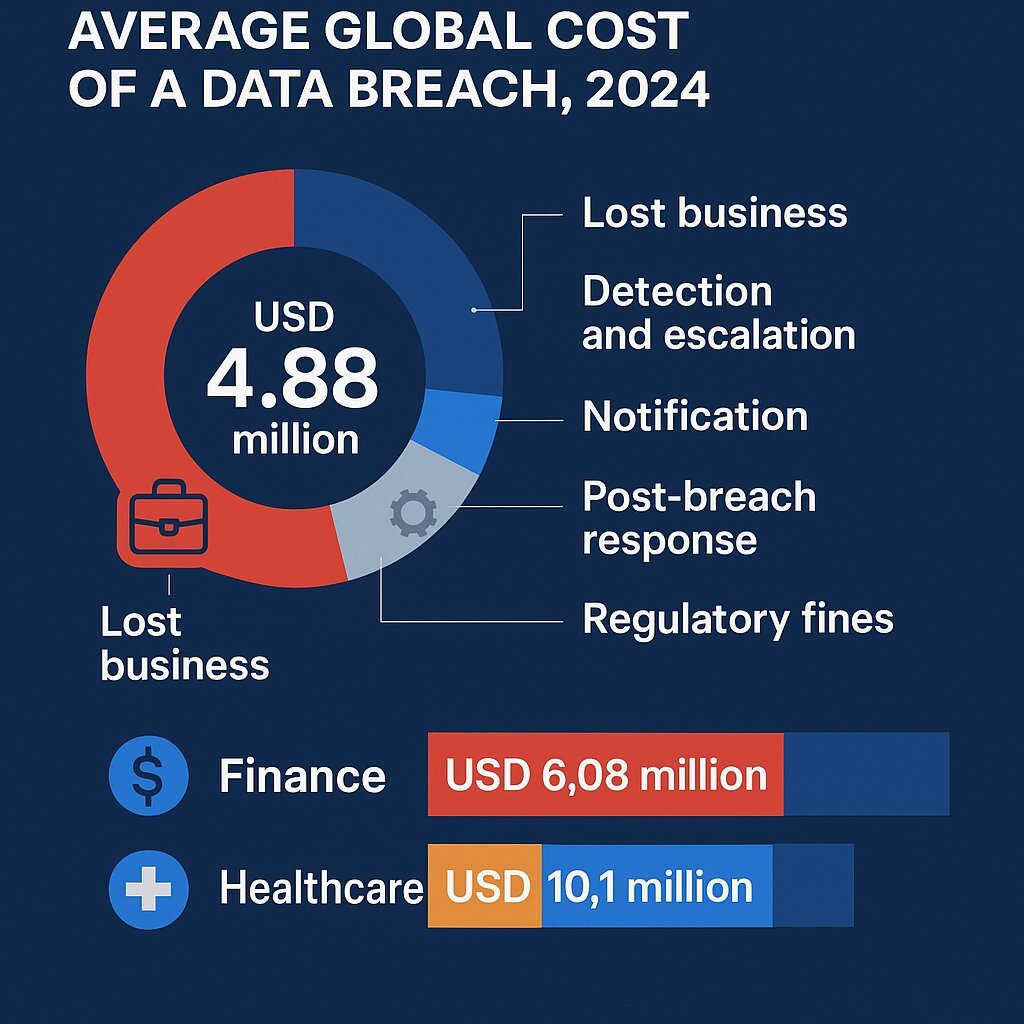
IBM's 2024 research provides a crucial anatomy of breach costs. Of the staggering USD 4.88 million average total, an overwhelming USD 2.8 million stems from lost business. This category includes revenue lost during operational downtime, customer churn following the incident, and the escalating costs of post-breach activities such as regulatory fines and increased customer support staffing. This data point is a clear signal to leadership: a cyber incident is fundamentally a business continuity event.
These costs are not uniform across industries; for highly regulated sectors, the financial stakes are significantly higher. The average breach cost for financial services firms climbs to USD 6.08 million, 22% higher than the global average. For the healthcare industry, which has been the costliest for 14 consecutive years, the average cost has reached a record USD 10.1 million. The potential for catastrophic loss is even more stark. For massive breaches involving the compromise of over 50 million records, the average cost in both the finance and healthcare sectors skyrockets to an astonishing USD 375 million, a figure that can threaten the solvency of even large enterprises.
Recent high-profile incidents provide stark illustrations of how digital threats manifest as devastating physical and financial business disruptions.
Mini Case Studies: Illustrating Business Impact
- Operational Paralysis - The Change Healthcare Attack: The February 2024 ransomware attack on Change Healthcare, a subsidiary of UnitedHealth Group, was not just a data breach; it was a systemic failure of the U.S. healthcare infrastructure. Because Change Healthcare is the predominant source for over 100 critical functions—including claims processing, clinical authorizations, and prescription drug fulfillment—the attack crippled the nation's healthcare system. Billions of dollars in payments to providers were halted, forcing many to seek emergency loans. Patients struggled to get timely access to care and medications, transforming a cybercrime into a "threat-to-life" event. The total cost of the response is estimated to have reached approximately USD 2.87 billion, demonstrating how a single third-party compromise can create a devastating "blast radius" that paralyzes an entire industry.
- Critical Infrastructure Disruption - Colonial Pipeline & JBS Foods: The 2021 ransomware attacks on Colonial Pipeline and JBS Foods proved that cyberattacks can have profound consequences on physical supply chains. The attack on Colonial Pipeline, which transports nearly half of the fuel consumed on the U.S. East Coast, forced a multi-day shutdown of its operations. This triggered widespread fuel shortages, panic buying, and a spike in gas prices to their highest point since 2014, compelling the President to declare a state of emergency. Just weeks later, a similar attack hit JBS, the world's largest meat processor. The attack rendered beef facilities in the U.S., Canada, and Australia inoperative, disrupting the global food supply chain, impacting wholesale meat prices, and forcing the company to pay an USD 11 million ransom to restore operations and prevent further shortages.
- Existential Financial Damage - The Merck NotPetya Attack: The 2017 NotPetya attack, a destructive wiper malware attributed to Russian state-sponsored actors, inflicted an estimated USD 1.4 billion in damages on pharmaceutical giant Merck. The malware wiped 40,000 of its computers, severely disrupting production and sales. The incident's aftermath introduced a new layer of complex financial and legal risk when Merck's insurers initially denied the claim under an "act of war" exclusion clause. While Merck eventually reached a settlement, the case highlights the evolving and ambiguous nature of cyber risk, where geopolitical events can have direct, catastrophic financial consequences for corporations, forcing boards to consider new dimensions of risk transfer and insurance coverage.
These cases reveal a fundamental shift in the nature of enterprise risk. The Verizon 2024 Data Breach Investigations Report (DBIR) found that 15% of breaches involved a third party, a 68% increase from the previous year, largely fueled by supply chain attacks like the one exploiting the MOVEit file transfer software. This is not merely a vendor management issue; it signifies that digital transformation has forged a deeply interconnected business ecosystem. An organization's risk profile is no longer defined solely by its own defenses but is inextricably linked to the security posture of its entire value chain. A vulnerability in a single software provider or a critical service processor can trigger a cascading failure across hundreds of otherwise well-defended companies. Consequently, board-level risk oversight must evolve from a narrow, internal focus to a systemic one, demanding a comprehensive assessment of the resilience of the entire value chain.

Section 2: A New Lexicon for the Boardroom - The FAIR Framework for Financial Quantification
The primary obstacle to effective cyber governance is a language barrier. CISOs often report on technical metrics—vulnerabilities patched, intrusion attempts blocked, compliance scores—that, while important operationally, fail to resonate in the boardroom. Executives and directors need to understand risk in the context of their fiduciary responsibilities, which requires a clear line of sight to financial exposure. The Factor Analysis of Information Risk (FAIR) model provides the "Rosetta Stone" to bridge this critical communication divide.
FAIR is the only international standard quantitative model for cybersecurity and operational risk. Its revolutionary power lies in its ability to move the conversation beyond subjective, color-coded heat maps (red, yellow, green) to a defensible, repeatable, and transparent methodology for quantifying risk in financial terms—the native language of the board. It provides a structured approach to answering the two fundamental questions at the heart of any risk decision.
Explaining the Core Components
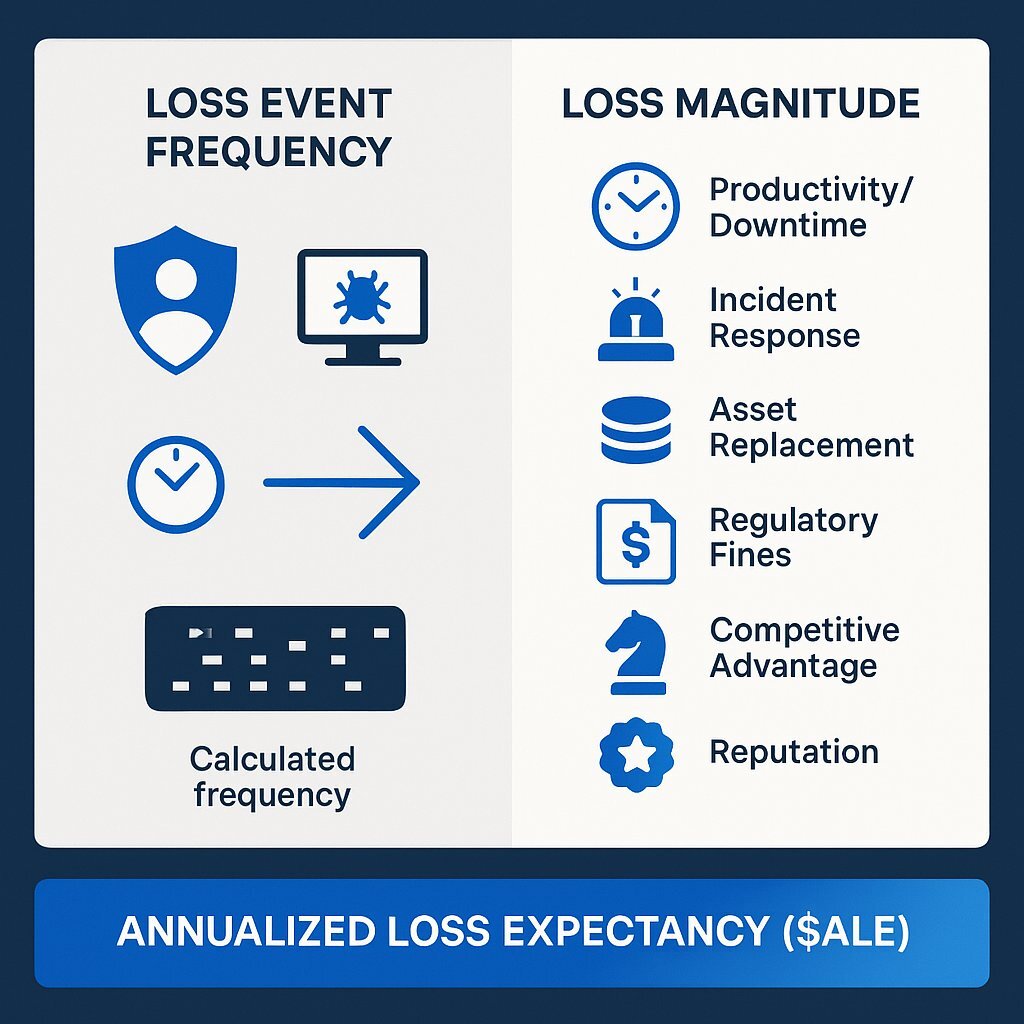
- Loss Event Frequency (LEF): This component answers the crucial question, "How often are we likely to suffer a material loss event?" The FAIR model treats this not as a guess but as a calculated probability derived from underlying factors. It considers the Threat Event Frequency (TEF) , which is how often a threat agent (e.g., a cybercriminal) comes into contact with an asset, and Vulnerability , which is the probability that the asset's controls will fail to resist the threat's action. For the board, this translates a vague threat into a concrete likelihood. Instead of hearing about "ransomware threats," the board can understand the probable frequency (e.g., once every five years) of a successful ransomware attack on a critical business system.
- Loss Magnitude (LM): This component answers the second critical question, "If a loss event occurs, how much will it cost us?" FAIR provides a comprehensive taxonomy for quantifying the financial impact, breaking it down into six primary forms of loss: productivity loss (downtime), response costs (incident management), replacement costs (assets), fines and judgments (regulatory penalties), competitive advantage loss, and reputational damage (customer churn). This detailed breakdown allows for a holistic financial picture that aligns directly with the concerns of a CFO or an audit committee, moving beyond simple IT cleanup costs to capture the full business impact.
By combining these two components, the FAIR model enables CISOs to articulate risk in terms of Annualized Loss Expectancy (ALE) , a metric that is immediately understandable and actionable for any business leader. The conversation transforms dramatically. Instead of stating, "We have a critical vulnerability in our authentication system," a CISO can now present a business case: "Based on our current controls, the risk of a data breach via compromised credentials in our customer database represents an annualized loss expectancy of USD 3 million. By investing USD 500,000 in a new Identity and Access Management (IAM) solution, we can reduce that exposure by 80%, yielding a clear return on security investment".
Implementing a quantitative framework like FAIR requires a disciplined shift in mindset and process, moving from a compliance-based to a risk-based approach. Baytech Consulting specializes in guiding organizations through this critical transition, helping leadership teams define their most critical risk scenarios, gather the necessary internal and external data, and build the analytical models needed to produce defensible, board-ready financial risk assessments.
This shift toward quantification has profound implications for corporate governance. Regulatory bodies, including the U.S. Securities and Exchange Commission (SEC), are placing greater scrutiny on board-level oversight of cybersecurity, requiring public companies to disclose their processes for identifying and managing material cyber risks. A board's fundamental fiduciary duty is to protect shareholder value by prudently managing all material risks to the enterprise. If cyber risk is a material business risk—which the escalating financial damages clearly demonstrate it is—but the board is unable to understand its potential financial impact, an argument can be made that its members are not fully equipped to fulfill their duty of care. Adopting a quantitative model like FAIR is therefore no longer just a technical best practice; it is becoming an essential tool for demonstrating due diligence and sound governance. It provides a defensible, auditable record of how the board is making risk-based decisions, moving its role from one of passive reception of technical data to one of active, informed oversight.
Section 3: The AI Double-Edged Sword: Amplifying Both Risk and Defense
Artificial Intelligence is arguably the most significant force multiplier in the cybersecurity landscape today, a powerful tool that is being wielded with increasing sophistication by both attackers and defenders. For business leaders, understanding this profound duality is critical for future-proofing the organization's security strategy, making informed technology investments, and governing a technology that presents both immense opportunity and unprecedented risk.

AI as a Weapon: The New Breed of Threats
Threat actors are rapidly weaponizing AI to enhance the scale, speed, and effectiveness of their attacks, creating a new generation of threats that can bypass traditional security controls and human intuition.
- Hyper-Realistic Social Engineering: Generative AI is being used to craft flawless, context-aware phishing emails and pretexting scenarios at scale, eliminating the tell-tale grammatical errors and awkward phrasing that once signaled a scam. This allows attackers to create highly personalized and believable lures, significantly increasing the probability of success for attacks based on credential theft and business email compromise. You can see just how impactful a single phishing attack on the software supply chain can be—with business risks that ripple throughout entire ecosystems.
- Deepfake Fraud: The rise of AI-powered audio and video deepfakes has enabled a new and alarming vector for fraud: executive impersonation. In a widely reported 2024 incident, a finance worker at a multinational firm in Hong Kong was manipulated into transferring USD 25.6 million to fraudsters. The employee initially suspected a phishing email but was convinced of its legitimacy after joining a video conference call with individuals who looked and sounded exactly like the company's UK-based CFO and other senior colleagues—all of whom were sophisticated deepfake creations.
- Autonomous Attacks: The threat is evolving beyond enhancing human-led attacks to enabling fully autonomous campaigns. Researchers at NYU Tandon have developed a proof-of-concept AI system they call "Ransomware 3.0," which was discovered on a malware analysis platform and dubbed "PromptLock". This system uses large language models to autonomously execute a complete ransomware attack. It can map a victim's network, identify and exfiltrate valuable files, encrypt systems, and write highly personalized ransom notes that reference the stolen data to increase psychological pressure—all for a cost of less than USD 1 in commercial AI API calls. This represents a paradigm shift from human-operated to machine-speed attacks that can adapt to their environment in real time.
AI as a Shield: The Defensive Dividend
While the offensive capabilities of AI are formidable, its potential as a defensive tool is equally, if not more, transformative. The business case for investing in AI-powered security is not speculative; it is backed by hard data on cost savings and operational efficiencies.
- Quantifiable Cost Savings: According to IBM's 2024 report, organizations that extensively deploy security AI and automation realize an average cost savings of USD 2.2 million per data breach compared to those that do not. This represents the single largest cost-saving factor identified in the study, providing a powerful, data-driven justification for investment.
Enhanced Defensive Capabilities: AI fundamentally revolutionizes security operations. It powers automated threat hunting , where machine learning algorithms analyze vast datasets from network traffic, endpoints, and logs to identify subtle patterns and anomalies indicative of an attack that would be invisible to human analysts. It is the engine behind
User and Entity Behavior Analytics (UEBA) , which establishes dynamic baselines of normal activity for every user and device on a network. When behavior deviates from this baseline—such as a user accessing sensitive files at an unusual time or from a new location—the system flags it as a potential insider threat or compromised account. AI also dramatically accelerates
incident response , automating the triage of alerts, correlating disparate events into a single incident, and even initiating containment actions like isolating a compromised endpoint from the network.
The Governance Challenge
The immense power of AI introduces a significant governance challenge. While it offers a clear defensive advantage, its adoption is a risk in itself if not managed properly. The same IBM report that highlights the cost savings of AI also warns that just 24% of generative AI initiatives are properly secured, potentially creating new and dangerous attack vectors for an organization. Navigating this complex landscape requires deep and specialized expertise.
Baytech Consulting helps organizations develop robust AI governance frameworks, enabling them to securely deploy AI for defensive purposes while implementing the necessary controls to protect against AI-driven attacks, data privacy violations, and internal misuse.
Section 4: An Actionable Blueprint for the C-Suite and the Board
Translating cyber risk into business risk is not a one-time project but a fundamental shift in governance and operations. It requires a coordinated effort, with new responsibilities and a new mindset for both technology leaders and the board of directors. The following blueprint provides a practical, actionable path forward for both groups.
A. For the CISO and CIO: Building the Business Case from the Ground Up
Technology leaders must evolve from being technical gatekeepers to strategic business partners. This requires a new approach to communication, measurement, and advocacy.
1. Adopt a Quantification Framework: The first and most critical step is to move beyond compliance checklists and qualitative assessments. Champion the adoption of the FAIR model to build a common, financially grounded language of risk that can be shared with the board, the CFO, and other business leaders. This provides a defensible and transparent foundation for all subsequent risk discussions and investment decisions.
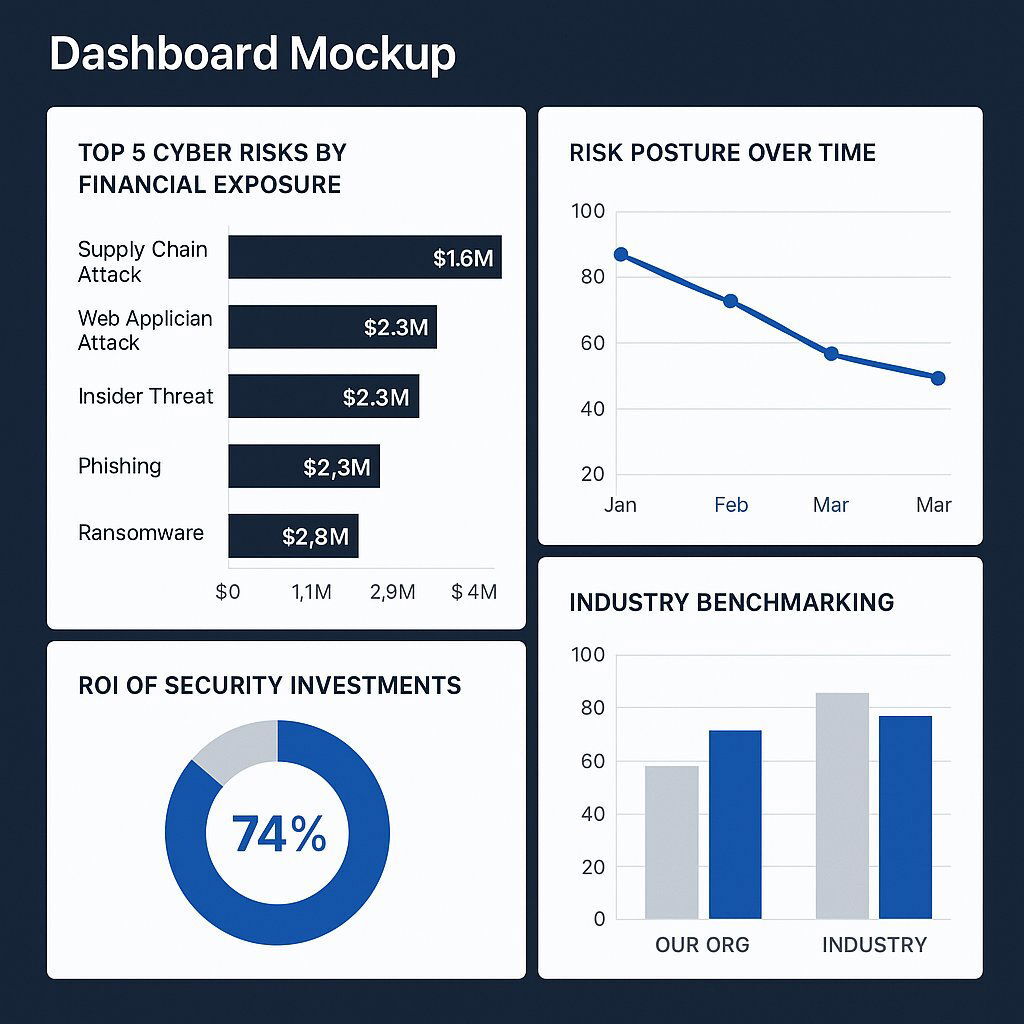
2. Redesign Your Dashboard: The metrics presented to the board must change. Replace technical, volume-based metrics (e.g., number of malware attacks blocked, vulnerabilities patched) with value-based metrics that directly answer the board's core business questions. A modern, board-ready dashboard should visualize:
- Top Cyber Risks by Financial Exposure: A ranked list of the most significant cyber risks quantified in terms of Annualized Loss Expectancy (ALE).
- Risk Posture Over Time: A trend line showing the organization's total financial risk exposure over time, demonstrating the impact of security initiatives.
- Return on Investment (ROI) on Key Security Investments: Clear calculations showing how specific investments (e.g., a new EDR tool) have reduced financial risk exposure relative to their cost.
- Industry Benchmarking: A comparison of the organization's quantified risk posture against industry peers, providing crucial context for risk appetite discussions.
3. Champion "Shift Left" Security as a Value Driver: Advocate for integrating security into the earliest stages of the software development lifecycle (a practice known as DevSecOps). This should not be framed as a cost or a development bottleneck but as a strategic investment with a proven and substantial return. Data from sources like the Verizon DBIR and Sonatype's DevSecOps Community Survey shows that mature DevSecOps practices can lead to 50% fewer security incidents and a 20% reduction in time-to-market. Forrester has quantified the ROI of specific DevSecOps platforms at over 300%. The underlying business case is simple: fixing a security vulnerability during the design phase is exponentially cheaper and faster than remediating it after a product has been deployed and a breach has occurred.
4. Frame Security Spending as Strategic Investment: Use the quantified risk data from your FAIR analysis to transform budget conversations. Instead of simply requesting funds for new tools, present security initiatives as investment opportunities with a clear, defensible ROI. The conversation should be framed as, "We are proposing an investment of $X to reduce our potential annual loss from a supply chain attack from $Y to $Z, delivering a net benefit to the organization".
B. For the Board of Directors: A New Standard for Cyber Oversight
The board's role is not to manage cybersecurity but to govern it effectively. This requires asking the right questions, demanding the right information, and ensuring that cyber risk is integrated into the fabric of corporate strategy.
1. Ask the Right Questions: The board must guide the conversation away from technical minutiae and toward strategic risk management. Evolve the line of questioning to focus on business impact.
- Instead of asking: "Are we 100% secure?" or "Are we compliant with the NIST framework?"
- Ask: "What are our top five cyber risks in terms of potential financial impact to the business?" "What is the annualized loss expectancy for each of these risks, and how does that figure compare to our board-approved risk appetite?" "What is the return on investment of our current cybersecurity program in terms of measurable risk reduction?".
2. Demand Quantified, Business-Centric Reporting: Mandate that the CISO and CIO report on cyber risk using a financial quantification framework like FAIR. Do not accept purely technical metrics or subjective heat maps without a clear and defensible translation to business impact and financial exposure. This discipline ensures that the board receives decision-useful information, not just data.
3. Govern the "Human Element": Recognize that technology alone cannot solve the cybersecurity challenge. With the Verizon DBIR consistently finding that the human element is involved in the majority of breaches (68% in the 2024 report), security must be treated as a cultural issue, not just a technology problem. The board should champion a robust security culture from the top down, ensuring that management is investing in continuous security awareness training, realistic phishing simulations, and designing business processes that are resilient to inevitable human error.
4. Integrate Cyber Risk into Corporate Strategy: Ensure that cyber risk is a key consideration in all major business initiatives. This includes M&A due diligence, digital transformation projects, the adoption of new technologies like AI, and new product launches. The board must ensure that the CISO has a seat at the table during these strategic discussions to provide critical input on the associated risks and required security investments.
To provide a clear, at-a-glance summary of the financial benefits of a proactive and strategic approach to security spending, the following table distills key findings from industry research.

Conclusion: From Technical Problem to Strategic Imperative
The era of treating cybersecurity as a siloed IT function, relegated to the back office and discussed in incomprehensible technical terms, is definitively over. The data is unequivocal: cyber risk is business risk. The financial and operational consequences of a breach—from paralyzed supply chains and halted production lines to nine-figure regulatory fines and irreparable brand damage—are now so significant that they demand the full attention and strategic oversight of the board and the entire C-suite.
The path forward lies in closing the communication gap that has long hampered effective governance. By adopting a common, quantitative language of risk through frameworks like FAIR, leaders can have meaningful, data-driven conversations about risk appetite and investment priorities. By strategically leveraging the defensive power of AI and automation, organizations can achieve a tangible return on investment, demonstrably reducing the financial impact of breaches. By demanding business-centric metrics, the board can fulfill its fiduciary duty to oversee this critical area of enterprise risk with the same rigor it applies to financial, legal, and operational risks.
This transformation turns the cybersecurity program from a reactive cost center into a proactive driver of business resilience. In a digital-first economy, a strong, quantifiable, and transparent security posture is no longer just a defensive necessity; it is a key competitive advantage that builds trust with customers, partners, and investors.
Effective cyber risk management is a journey of continuous improvement. It requires not only the right tools and frameworks but also the right strategic partners. To build a mature, quantifiable, and board-ready cybersecurity program, organizations must seek out experts who understand both the complex technical landscape and the boardroom imperative. To begin translating your cyber risk into a clear and actionable business strategy, engage with a trusted advisor like Baytech Consulting today.
About Baytech
At Baytech Consulting, we specialize in guiding businesses through this process, helping you build scalable, efficient, and high-performing software that evolves with your needs. Our MVP first approach helps our clients minimize upfront costs and maximize ROI. Ready to take the next step in your software development journey? Contact us today to learn how we can help you achieve your goals with a phased development approach.
About the Author

Bryan Reynolds is an accomplished technology executive with more than 25 years of experience leading innovation in the software industry. As the CEO and founder of Baytech Consulting, he has built a reputation for delivering custom software solutions that help businesses streamline operations, enhance customer experiences, and drive growth.
Bryan’s expertise spans custom software development, cloud infrastructure, artificial intelligence, and strategic business consulting, making him a trusted advisor and thought leader across a wide range of industries.


