
How a Single Phishing Attack Broke the Open-Source Supply Chain—and What Your Business Can Do
September 11, 2025 / Bryan Reynolds
Introduction: A Single Click, A Trillion Dependencies
On September 8, 2025, a single, seemingly innocuous click by a trusted software developer triggered a security event of unprecedented scale. Malicious code was injected into foundational software packages that are downloaded a staggering 2.6 billion times every week. This incident was not a sophisticated exploit of a zero-day vulnerability in a server; it was a supply chain hijack that began with a classic phishing email. It serves as a stark reminder that in the modern digital economy, all software is built upon a vast, interconnected supply chain of open-source components. A single compromised link in that chain—a single human error—can expose millions of downstream projects and their users to significant risk.
The fallout from this attack forced development teams globally to halt operations, audit codebases, and confront a new reality: the open-source ecosystem, the very engine of modern innovation, is a primary and increasingly targeted attack vector. For business leaders, this event elevates software supply chain security from a technical concern to a critical issue of business continuity, operational resilience, and brand reputation.
This report, prepared by the experts at Baytech Consulting, adopts the 'They Ask You Answer' approach to address the urgent questions on every executive's mind. We will dissect what exactly happened, explain why it matters profoundly to your business, and, most importantly, provide a clear, actionable framework for how you can protect your organization from becoming the next headline. We believe that building resilient software is not just about writing better code; it's about building a resilient development process from the ground up.
What Happened? Anatomy of a Supply Chain Hijack
To understand the risk, it is essential to first understand the mechanics of the attack. It was a multi-stage operation that masterfully combined social engineering, credential theft, and the weaponization of trusted software components.
The Bait: A Masterclass in Social Engineering
The entire attack hinged on the successful compromise of a single, highly respected open-source developer, Josh Junon, known in the community as "qix". The entry point was not a technical flaw but a meticulously crafted phishing email designed to exploit human psychology.
The email was a study in deceptive legitimacy. It was sent from the domain support[at]npmjs[dot]help , a clever typosquat of the official npmjs.com domain used by the npm package registry. This domain was registered just three days prior to the attack, signaling a premeditated and targeted campaign. The message itself employed classic social engineering tactics, creating a sense of urgency by falsely claiming that Junon's account would be locked on September 10, 2025, if he did not update his Two-Factor Authentication (2FA) credentials, which the email alleged were over 12 months old.
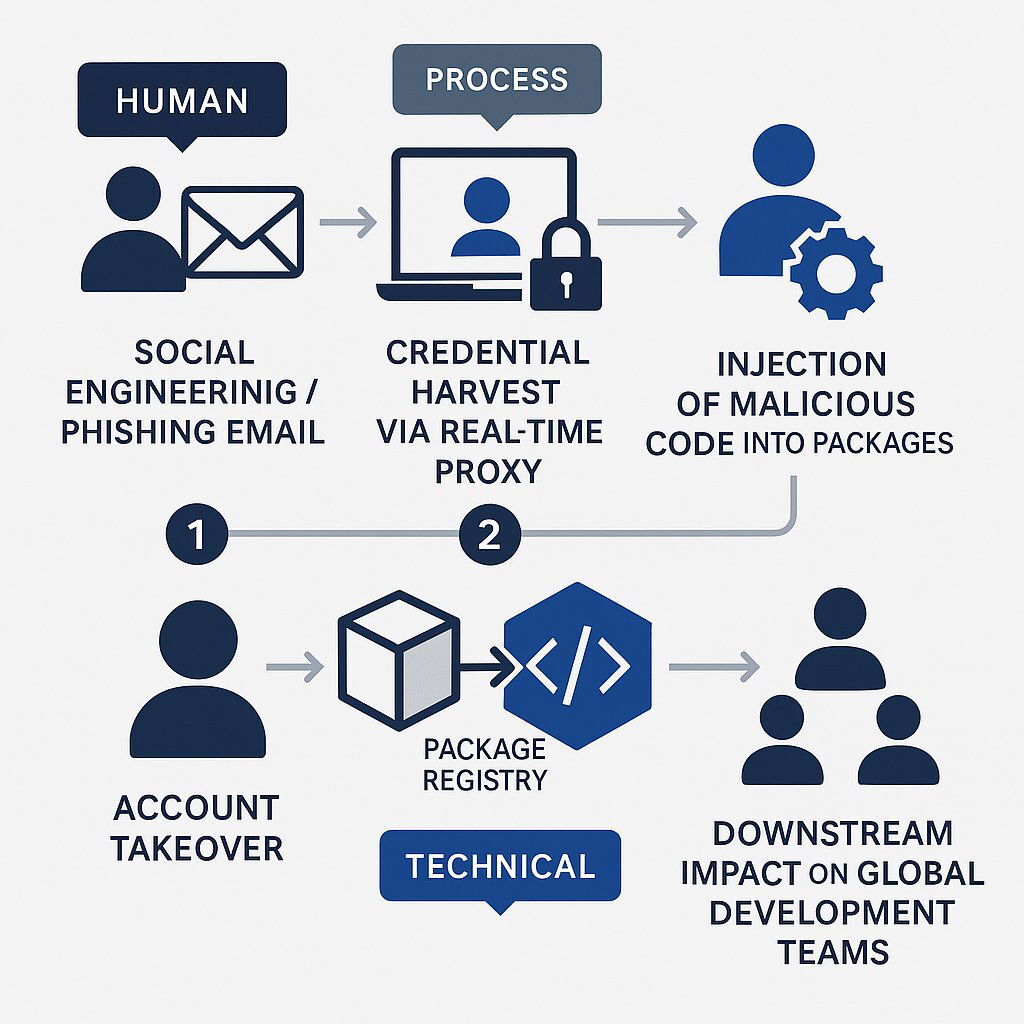
Even seasoned experts can fall victim to such sophisticated schemes. Junon himself noted that he was on his mobile device after a long and busy week and made the uncharacteristic mistake of clicking the link instead of navigating directly to the site. This single action led him to a fake login portal that was a perfect replica of the real npm site. This highlights a crucial point: technical defenses are often circumvented by targeting the human element, which remains the most unpredictable and exploitable part of any security system. Even experts, under the right conditions of stress or distraction, are vulnerable.
The attack's sophistication is further demonstrated by how it defeated 2FA, a security control many organizations consider a panacea. The phishing website was not merely a static page designed to harvest a password; it functioned as a real-time proxy. When Junon entered his username, password, and the six-digit Time-based One-Time Password (TOTP) code from his authenticator app, the phishing site immediately relayed those credentials to the legitimate npm service in the background. This captured a live, authenticated session, giving the attackers full control of his account. This proves that the mere presence of a security control like 2FA is insufficient. The human interaction with that control is a critical vulnerability point that attackers are actively exploiting. This incident underscores the need for phishing-resistant authentication methods and, more importantly, for continuous, context-aware security training that builds resilient habits, not just passive awareness.
The Switch: Weaponizing Foundational Code
Once in control of Junon's account, the attackers moved swiftly to weaponize the trust he had built over years of contributions. They published malicious new versions of 18 popular npm packages that he maintained.
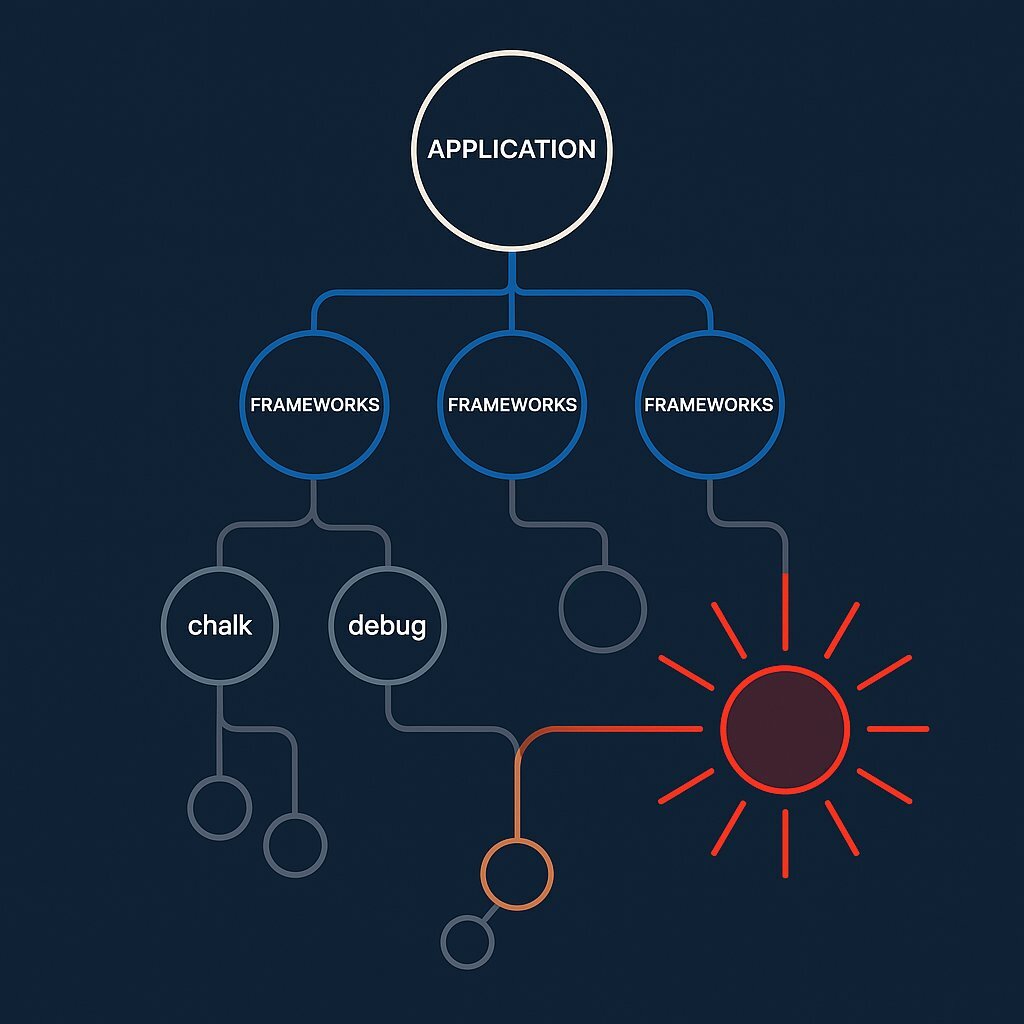
These were not obscure, niche libraries. The compromised packages included foundational utilities like debug , a core logging tool used by developers everywhere, and chalk , a ubiquitous library for styling text in terminal outputs. These components are the digital equivalent of nuts and bolts; they are used in millions of other software projects, often without the direct knowledge of the final application's developer.
The timeline of the attack reveals both the speed of the compromise and the power of the open-source community's response. The first malicious package was published at 13:16 UTC on September 8, 2025. By approximately 15:20 UTC, vigilant members of the community had spotted suspicious code and began raising alarms on GitHub. The compromised maintainer, once aware, began the cleanup process shortly thereafter. The window of exposure, during which the malicious code was live on the npm registry, was only about two hours. While this rapid response limited the damage, the sheer download volume of these packages meant that thousands of automated build systems could have pulled in the compromised versions during that brief period.
To fully grasp the potential blast radius, consider the scale of the most impacted packages.
| Package Name | Primary Function | Weekly Downloads (Approx.) |
|---|---|---|
ansi-styles | Terminal text styling (colors, etc.) | 371.4 Million |
debug | Core developer logging tool | 357.6 Million |
chalk | Popular terminal string styling library | 299.9 Million |
supports-color | Detects terminal color support | 287.1 Million |
strip-ansi | Removes ANSI escape codes from strings | 261.1 Million |
ansi-regex | Regular expression for matching ANSI codes | 243.6 Million |
color-convert | Color conversion utility | 193.5 Million |
This table illustrates why the compromise of a few "utility" packages can have such a massive impact. They are fundamental building blocks of the entire JavaScript ecosystem.
The Payload: A Silent Crypto-Heist in the Browser
The malware itself was a highly targeted and stealthy piece of code. It was designed as a browser-only crypto-stealer, meaning it did not attempt to infect the user's operating system or file system. Instead, its malicious logic would activate only when an application containing the compromised code was run within a web browser.
The malware executed a sophisticated "man-in-the-browser" attack. It worked by "hooking" into core browser functions like fetch and XMLHttpRequest , which are used to make network requests, as well as the application programming interfaces (APIs) of popular Web3 cryptocurrency wallets like MetaMask ( window.ethereum ). By intercepting these functions, the malware could monitor and manipulate data in transit.
Its primary function was to hijack cryptocurrency transactions. When a user attempted to send funds, the malware would scan the transaction data for wallet addresses associated with various cryptocurrencies, including Bitcoin, Ethereum, Solana, Tron, Litecoin, and Bitcoin Cash. It would then silently swap the legitimate recipient's address with an address controlled by the attacker.
The true danger of this payload was its stealth. The manipulation happened in the background, just before the transaction was sent to the blockchain for signing. The user interface displayed on the screen would show the correct, intended recipient address, giving the user no visual indication that their funds were being rerouted. To make detection even more difficult, the malware employed advanced techniques, such as using a Levenshtein distance algorithm to select an attacker-controlled wallet address that was visually similar to the legitimate one, foiling even a careful manual review by the user.
Why This Matters: The Business Impact of a Broken Link in the Chain
Translating this technical event into business terms reveals profound risks to any organization that develops or uses software. The low direct financial impact of this specific attack belies the enormous systemic vulnerability it exposed.
The Transitive Trust Trap: You've Inherited Risk You Can't See
This incident is a dramatic illustration of the "transitive dependency" problem. The compromised packages, chalk and debug , are rarely dependencies that a developer explicitly chooses to install. Instead, they are dependencies of other, more complex libraries and frameworks that developers use every day. They are pulled into projects automatically, often buried several layers deep in the dependency tree.
An effective analogy is that of an automotive manufacturer. The manufacturer may have rigorous quality controls for the major components it sources, like engines and transmissions. However, it likely has no visibility into the supplier of a specific, tiny screw used deep inside the engine block by one of its Tier 3 suppliers. If that screw is made from a faulty batch of metal, it can lead to catastrophic engine failure across the entire product line, even though the manufacturer never directly purchased or vetted that individual screw.
This is the reality of modern software development. Your application's security is only as strong as the security practices of the most obscure, under-resourced, or momentarily distracted open-source maintainer in your entire software supply chain. You have inherited their risk, whether you are aware of it or not.
The New Normal: A Persistent and Growing Threat
It would be a grave mistake to view this attack as an isolated or freak event. It is, in fact, the new normal. The software supply chain has become one of the most favored targets for malicious actors, and the frequency and sophistication of these attacks are increasing at an alarming rate.
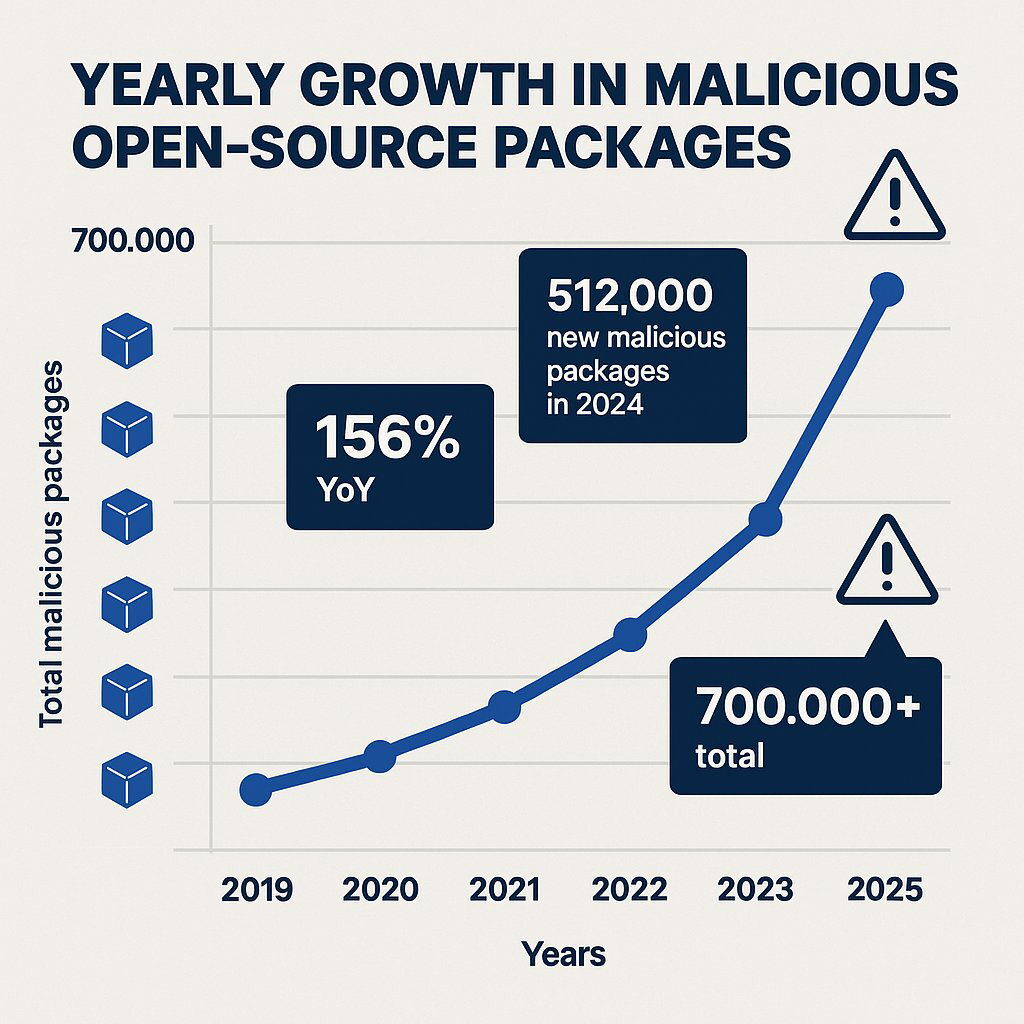
Industry data paints a clear and disturbing picture of this trend.
- The number of malicious packages discovered in open-source repositories has grown by an astonishing 156% year-over-year .
- A 2024 survey revealed that over 75% of software supply chains had experienced a cyberattack within the previous 12 months.
- In the last year alone, security researchers have logged over 512,000 new malicious packages being uploaded to public repositories.
This data confirms that the npm attack is not an anomaly but a powerful example of a systemic and escalating crisis. Relying on luck or the goodwill of the open-source community is no longer a viable security strategy. Businesses must adopt a proactive and strategic approach to managing this growing risk.
Note: This is a representative chart. Data from and indicates a sharp increase in discovered malicious packages, reaching over 700,000 cumulatively since 2019.
Beyond Financial Theft: Operational Chaos and Reputational Damage
The direct financial theft attributed to this specific attack was surprisingly low—approximately $970 was tracked to attacker-controlled wallets. This, however, was not due to a lack of potency in the malware but rather to the incredibly fast detection and response from the open-source community. The incident serves as a critical "near miss" that exposed a deep-seated vulnerability in the ecosystem. To focus on the low dollar amount is to miss the point entirely. The next attacker may deploy a far stealthier payload, such as a credential exfiltrator or a subtle data backdoor, that could remain undetected for months, causing exponentially greater damage. This attack should be treated as a warning shot, not a resolved crisis.
The true business costs of such an incident are far more significant and multifaceted:
- Operational Disruption: In the hours and days following the attack, development teams worldwide were forced to halt feature development and product releases. CI/CD pipelines failed, and engineering resources were diverted to emergency audits and remediation efforts, grinding productivity to a halt.
- Remediation Costs: The person-hours required to scan every application, identify exposure to the malicious packages, purge them from every environment (development, testing, and production), rebuild clean versions of the software, and securely redeploy them represent a massive, unbudgeted operational expense.
- Reputational Damage: The ultimate cost is the erosion of customer trust. Shipping a product that contains crypto-stealing malware, even if done unknowingly, can be a catastrophic, brand-destroying event. In a competitive market, trust is a company's most valuable asset, and once lost, it is incredibly difficult to regain.
How Can Businesses Protect Themselves? A Framework for Supply Chain Resilience
Protecting an organization from these threats requires a multi-layered, defense-in-depth strategy. It is not about finding a single tool or solution but about building a resilient culture and process supported by the right technology. At Baytech Consulting, we recommend a three-tiered framework focusing on foundational hygiene, process fortification, and the human element.
Tier 1: Foundational Security Hygiene
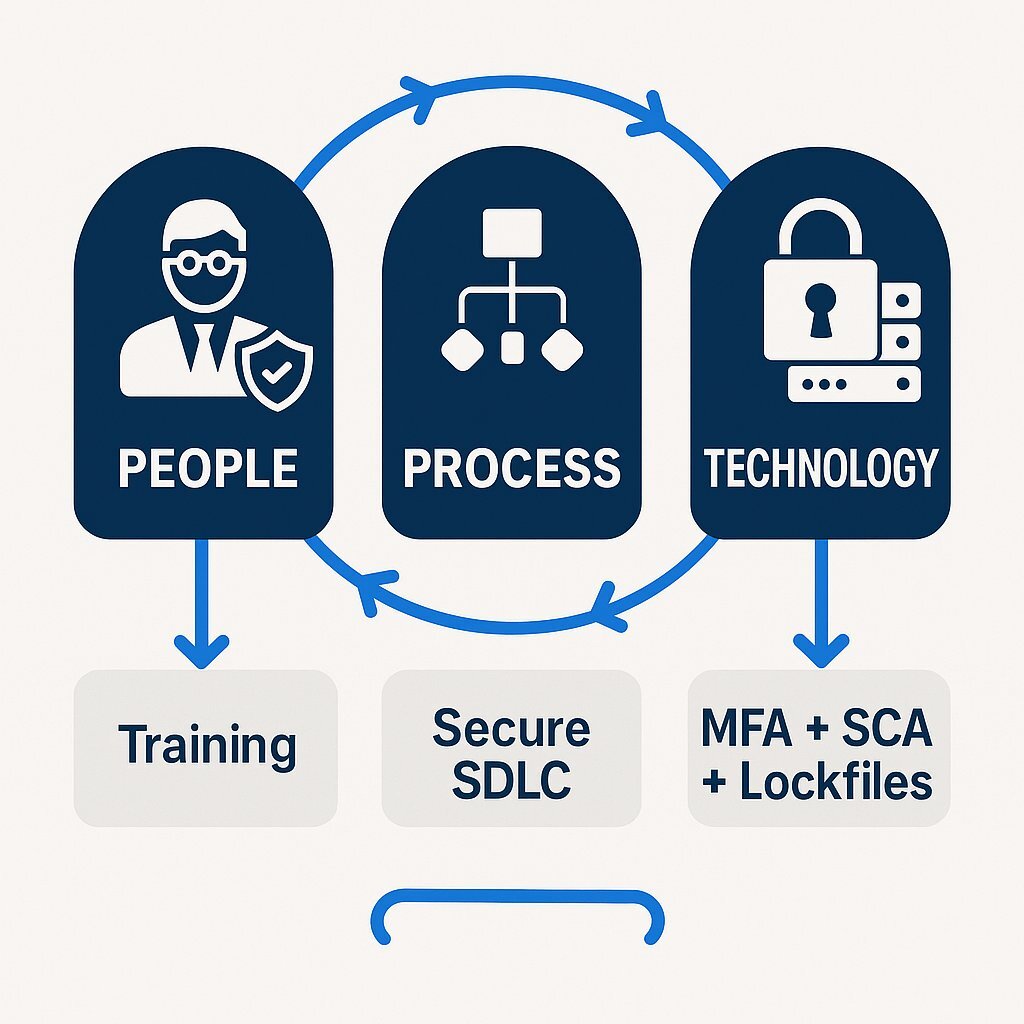
These are the immediate, tactical, and non-negotiable steps that form the bedrock of any secure development practice.
- Enforce Strong Authentication Everywhere: The initial compromise was due to a phished password and TOTP code. Organizations must mandate the strongest possible form of multi-factor authentication for all developer accounts on critical platforms like npm, GitHub, and cloud providers. This means moving beyond SMS and app-based TOTP codes, which are susceptible to real-time proxy phishing, and enforcing the use of hardware-based security keys that support protocols like WebAuthn. These keys are inherently phishing-resistant because the authentication is bound to the physical device and the legitimate domain.
Audit Your Dependencies NOW: Every organization should treat this incident as a call to action. Security teams must immediately conduct a comprehensive audit of all project dependency lockfiles (
package-lock.json,yarn.lock, etc.) to check for the presence of any of the compromised package versions. Automated tools likenpm auditcan help identify directly and transitively vulnerable dependencies. For a step-by-step process of evaluating risks in dependencies and managing key cost drivers in the face of evolving threats such as AI, see the Custom Software Budgeting 2026 Playbook for in-depth recommendations.- Pin Your Dependencies with Lockfiles: The use of dependency lockfiles must be a mandatory policy. A lockfile records the exact version of every single dependency and sub-dependency used in a project. This ensures that every time the application is built—whether by a developer on their laptop or by an automated CI/CD server—it uses the exact same, vetted versions of the code. This simple practice prevents the build system from automatically fetching a newly published (and potentially malicious) version of a package, effectively containing the threat until the lockfile can be consciously updated.
Tier 2: Fortifying the Development Process (The Secure SDLC)
Foundational hygiene must be supported by a robust process that integrates security into the entire software development lifecycle (SDLC). This is the core principle of "Shifting Left"—addressing security concerns as early as possible in the development process, rather than treating security as an afterthought or a final gate before release.
- Security as a Design Requirement: A secure SDLC begins by treating security as a core requirement of any project, on par with functional and performance requirements. This involves conducting threat modeling during the design phase to identify potential attack vectors and designing security controls from the outset. For a deep dive into software maintenance, ongoing evolution, and risk considerations post-launch, you may find value in our Executive Guide to Post-Launch Software Maintenance.
- Automated Security in CI/CD: The CI/CD pipeline is the ideal place to enforce security policies automatically and consistently. Integrating automated security tools into the pipeline creates a powerful defense layer. Key tools include:
- Software Composition Analysis (SCA): These tools automatically scan all open-source dependencies in a project, checking them against a database of known vulnerabilities, license compliance issues, and other quality metrics. Read more about how to integrate these automated controls in our guide on DevSecOps for Growth & Security.
- Static Application Security Testing (SAST): SAST tools analyze an application's source code for security flaws and unsafe coding patterns before the code is even compiled, catching potential vulnerabilities at the earliest possible stage.
- Security Gates: The most critical step is to configure these automated tools to act as "security gates." This means the CI/CD pipeline can be configured to automatically fail a build and block a deployment if a vulnerability exceeding a certain severity threshold is detected. This prevents vulnerable code from ever reaching a production environment and helps build a resilient development process that keeps your supply chain trustworthy.
Tier 3: The Human Firewall: Investing in Developer Security Training
Technology and process alone are insufficient. This attack began with a human being tricked by a phishing email. Therefore, the final and most critical tier of defense is strengthening the "human firewall."
- Beyond Generic Awareness: Standard corporate phishing training that focuses on generic CEO gift card scams is wholly inadequate for technical staff. Developers are high-value targets who face unique and sophisticated social engineering threats. They need specialized training that addresses the attack vectors they are most likely to encounter, such as phishing attempts disguised as platform security notifications, fake code review requests from compromised colleague accounts, or malicious pull requests on GitHub.
- Continuous Simulation and Reinforcement: The most effective way to build resilience is through practice. Organizations should implement continuous, realistic phishing simulation programs that are specifically designed for developers. These simulations mimic real-world attacks, test their responses in a safe environment, and provide immediate, just-in-time training to reinforce learning. This approach moves beyond passive knowledge and builds active, defensive "muscle memory". See our insights on protecting intellectual property and teams when outsourcing development.
- Cultivating a Security Culture: Ultimately, the goal is to create a culture where security is a shared responsibility, not just the job of the security team. This involves empowering developers with the knowledge, tools, and autonomy to make secure decisions. It means fostering an environment where raising a security concern is encouraged and rewarded, and where security is seen as an enabler of high-quality, resilient software, not a blocker to innovation. For actionable advice on organizational change and user adoption, see our guide to overcoming software resistance in technical teams.
The following table summarizes this three-tiered approach into a strategic framework.
| Pillar | Key Actions | Business Outcome |
|---|---|---|
| People | - Specialized developer phishing simulation & training. - Secure coding standards and education. - Foster a culture of shared security responsibility. | Reduces the risk of initial compromise via social engineering, the most common attack vector. |
| Process | - Implement a formal Secure SDLC. - Establish an incident response plan for supply chain attacks. - Create strict policies for vetting and using third-party code. | Integrates security into the DNA of development, making it proactive rather than reactive. |
| Technology | - Mandate phishing-resistant MFA (e.g., security keys). - Use lockfiles to pin all dependency versions. - Automate SCA and SAST scanning in CI/CD pipelines with security gates. | Provides automated, consistent enforcement of security policies and detects vulnerabilities before they reach production. |
Conclusion: Building a More Secure Future, Together
The compromise of npm packages with 2.6 billion weekly downloads was a watershed moment for the software industry. It laid bare the inherent fragility of the open-source supply chain and demonstrated with chilling clarity how a single point of human error can cascade into a global security incident. The key lessons are undeniable: the software supply chain is now a primary battleground for cyber attacks; trust in this ecosystem is fragile; and security cannot be a one-time checklist item but must be a continuous, strategic imperative.
Addressing this challenge requires a holistic approach that integrates people, process, and technology. It demands that we move beyond reactive patching and embrace a proactive culture of security that begins at the earliest stages of development. For business leaders, this is no longer just an IT issue; it is a fundamental aspect of risk management and corporate governance. See how a cloud-native approach can enhance resilience and business agility in our guide to cloud-native architecture.
In this new landscape, building a secure and resilient development process is not a burden—it is a powerful competitive advantage. Organizations that can demonstrate the integrity of their software supply chain will earn greater trust from customers, partners, and regulators. They will innovate faster and more confidently, knowing their work is built on a solid foundation. In today's interconnected world, you don't just ship code; you ship trust. At Baytech Consulting, we partner with businesses to build that trust into every line of code, ensuring your innovation is built on a foundation of resilience.
Supporting Links
- NIST Secure Software Development Framework (SSDF): https://csrc.nist.gov/Projects/ssdf
- The Open Source Security Foundation (OpenSSF): https://openssf.org/
- SANS Security Awareness Training: https://www.sans.org/for-organizations/workforce/security-awareness-training/phishing
About Baytech
At Baytech Consulting, we specialize in guiding businesses through this process, helping you build scalable, efficient, and high-performing software that evolves with your needs. Our MVP first approach helps our clients minimize upfront costs and maximize ROI. Ready to take the next step in your software development journey? Contact us today to learn how we can help you achieve your goals with a phased development approach.
About the Author

Bryan Reynolds is an accomplished technology executive with more than 25 years of experience leading innovation in the software industry. As the CEO and founder of Baytech Consulting, he has built a reputation for delivering custom software solutions that help businesses streamline operations, enhance customer experiences, and drive growth.
Bryan’s expertise spans custom software development, cloud infrastructure, artificial intelligence, and strategic business consulting, making him a trusted advisor and thought leader across a wide range of industries.


