
Outsourcing Software Development? The Executive Checklist for IP Protection
September 18, 2025 / Bryan ReynoldsThe Executive's Playbook: A Practical Checklist for Protecting Your IP When Outsourcing Software Development
The High-Stakes Balancing Act of Innovation and Risk
In today's hyper-competitive landscape, the decision to outsource software development is no longer a niche strategy but a core driver of innovation and growth. It offers a powerful trifecta of benefits: significant cost savings, immediate access to a global pool of specialized talent, and a dramatically accelerated time-to-market. However, this strategic advantage comes with a commensurate level of risk that keeps executives awake at night. The very act of opening your digital doors to an external partner exposes your most valuable assets—your intellectual property (IP)—to potential theft, misuse, and accidental leakage.
The numbers paint a stark picture. In the United States alone, the annual cost of intellectual property theft ranges from a staggering $180 billion to $540 billion. More specific to the outsourcing domain, a 2024 survey revealed that 43% of companies engaging external development partners harbor significant concerns about IP theft and data breaches. These are not hypothetical fears; they are tangible, balance-sheet-level risks that can lead to loss of competitive advantage, costly legal battles, and irreparable reputational damage.
This creates a critical paradox for modern leadership: how do you leverage the immense power of outsourcing to innovate faster, without simultaneously gambling with the crown jewels of your business? The answer lies in shifting your perspective. A proactive, multi-layered IP protection strategy is not a bureaucratic hurdle or a drag on agility; it is the fundamental prerequisite for successful, scalable innovation through outsourcing. It is an ongoing process, meticulously woven into every phase of the partnership, from initial vetting to final offboarding—not a one-time contractual event.
This playbook is designed for executives who need a clear, actionable framework for navigating this complex terrain. It provides a practical checklist to transform IP protection from a source of anxiety into a strategic advantage. For firms like Baytech Consulting, who work with enterprise clients on mission-critical software, these principles are not just best practices; they are the bedrock of their methodology. A truly strategic partner doesn't just build code; they build a fortress around your IP, turning protection from a client's burden into a shared, managed responsibility.
Phase 1: The Strategic Foundation — Before You Write a Single Line of Code
The most critical errors in IP protection are often made before a single contract is drafted. The groundwork laid during the strategic planning and partner selection phase dictates the security and success of the entire engagement. Rushing this stage is a recipe for future disputes and vulnerabilities. A proactive approach begins with a deep understanding of your own assets and a rigorous evaluation of potential partners.
Checklist Item 1: Conduct a Pre-emptive IP Audit
Before you can protect your intellectual property, you must know precisely what it is, where it is, and how valuable it is to your business. Engaging any potential partner without this internal clarity is like negotiating a treaty without a map. The first step is to conduct a comprehensive audit and create an inventory of all existing IP assets that could be involved in the project.
This audit should meticulously identify and classify the different types of IP relevant to software development:
- Copyrights: This is the most direct form of protection for software. It secures the original works of authorship fixed in a tangible medium, which includes your source code, object code, technical documentation, UI/UX designs, and website content. International agreements like the Berne Convention, reinforced by the TRIPS Agreement and the WIPO Copyright Treaty, establish that computer programs are protected as literary works, whether in source or object code form.
- Trade Secrets: This is often the most valuable and most vulnerable category of IP in an outsourcing context. Trade secrets encompass any confidential business information that provides a competitive edge. This includes your proprietary algorithms, business methods, formulas, customer lists, user data, internal processes, and strategic roadmaps. Unlike patents, trade secrets are protected without registration, but that protection is contingent on taking "reasonable steps" to keep them secret.
- Patents: Patents protect novel, useful, and nonobvious inventions and processes. In the software world, this can apply to unique algorithms, data-processing methods, or key software functionalities. The patentability of software varies significantly across jurisdictions, making it a complex but powerful form of protection for core innovations.
- Trademarks: While not protecting the code itself, trademarks are vital for protecting your brand identity, including your software's name, logos, and slogans, which are crucial for market recognition.
The audit process allows you to make strategic decisions about disclosure. By classifying your IP by sensitivity, you can adopt a strategy of "Everything but the Secret Ingredient". This involves keeping your most critical, high-value trade secrets—the core algorithm or the unique business logic—in-house. You can then safely outsource the development of surrounding components, user interfaces, or supporting modules. The in-house team can later merge the outsourced code with the proprietary core, minimizing the exposure of your most valuable assets.
Checklist Item 2: Execute Rigorous Partner Due Diligence
Selecting your outsourcing partner is arguably the single most important risk mitigation step you will take. A partner with a weak security culture or a questionable history can render even the most meticulously crafted legal agreements ineffective. Your due diligence must go far beyond a simple review of their portfolio and pricing. It must be a forensic examination of their legal, security, technical, and financial posture.
A comprehensive vendor audit should include the following sub-checklist:
- Legal & Reputational Scrutiny: Your investigation must begin with the partner's history. Have they been involved in any past IP-related legal disputes, data compromises, or litigation? A history of such issues can indicate a systemic lack of commitment to security. Demand references from previous clients, especially those whose projects involved sensitive IP, and ask them directly about the vendor's ability to meet confidentiality requirements.
- Security Posture Evaluation: This is a non-negotiable deep dive. Verify their security certifications, such as ISO 27001 for information security management and SOC 2 Type II for controls related to security, availability, and confidentiality. These are not just badges; they are proof of standardized, audited security practices. Request and meticulously review their internal security policies, incident response plans, business continuity plans, and the results of recent third-party penetration tests. Ask pointed questions about their data encryption standards for data at rest and in transit, their access control methodologies, and the frequency and content of their employee security training programs.
- Technical & Process Maturity: Assess their software development lifecycle (SDLC). Do they formally adhere to a secure SDLC framework, integrating security at every stage? What are their mandatory processes for code reviews, quality assurance, and version control? A critical question is whether they subcontract work. If they do, how do they enforce IP protection and security standards down the supply chain? A vendor who subcontracts without a robust flow-down of contractual obligations is a significant weak link.
- Financial Stability & Operational Resilience: A partner in financial distress can cut corners on security or even go out of business mid-project, leaving your IP in limbo. Review their financial statements to ensure they are a viable, stable, long-term partner. Furthermore, evaluate their disaster recovery plans to understand how they would protect your data and maintain service continuity in the face of unexpected disruptions.
The process of conducting due diligence is as revealing as the information it uncovers. A mature, security-conscious partner will have this documentation readily available and will view your rigorous questions as a sign of a serious client. They will be transparent and forthcoming. Conversely, a vendor's reluctance to discuss their security measures, an inability to produce a documented incident response plan, or evasiveness when asked for IP-sensitive client references is a major red flag. This behavior signals a cultural misalignment on the importance of security—a deep-seated, systemic risk that no contract can fully mitigate. The goal is to find a partner for whom security is a core competency and a cultural imperative, not merely a line item in a contract.
To aid in this critical evaluation, a structured approach is essential. The following scorecard provides a framework for quantitatively comparing potential partners, transforming a subjective process into a more data-driven decision.

| Evaluation Criteria | Key Considerations & Evidence |
|---|---|
| Security & Compliance | Does the vendor hold key certifications like ISO 27001 or SOC 2 Type II? Can they provide documented security policies, incident response plans, and recent audit reports? What are their standards for data encryption at rest and in transit? |
| IP Protection Track Record | Is there any history of IP-related litigation or data breaches? Can they provide strong client references specifically for IP-sensitive projects? Do they have a formal, documented internal IP protection policy? |
| Technical & Process Maturity | Do they follow a Secure SDLC? What are their mandatory code review and QA processes? What is their policy on using open-source software and managing its licenses/vulnerabilities? Do they subcontract, and if so, how is IP protection enforced? |
| Legal & Contractual Posture | Are they willing to negotiate strong, client-favorable IP ownership clauses (Work for Hire + Assignment)? Do they agree to a clear governing law and jurisdiction? Are their liability and indemnification terms reasonable? |
| Communication & Cultural Fit | Do they have established protocols for clear and regular communication? Is there sufficient overlap in working hours? What project management methodology do they use? What are their employee retention and turnover rates? |
Phase 2: The Legal Armor — Forging Ironclad Agreements
Once a promising partner has been vetted, the next phase is to construct the legal framework that will govern the relationship. Contracts are not mere formalities; they are the strategic instruments that define ownership, establish the rules of engagement, and provide recourse in the event of a breach. A poorly drafted agreement is an open invitation to disputes over IP ownership, which can be financially ruinous and strategically crippling.
Checklist Item 3: Architect a Master Service Agreement (MSA) with IP at its Core
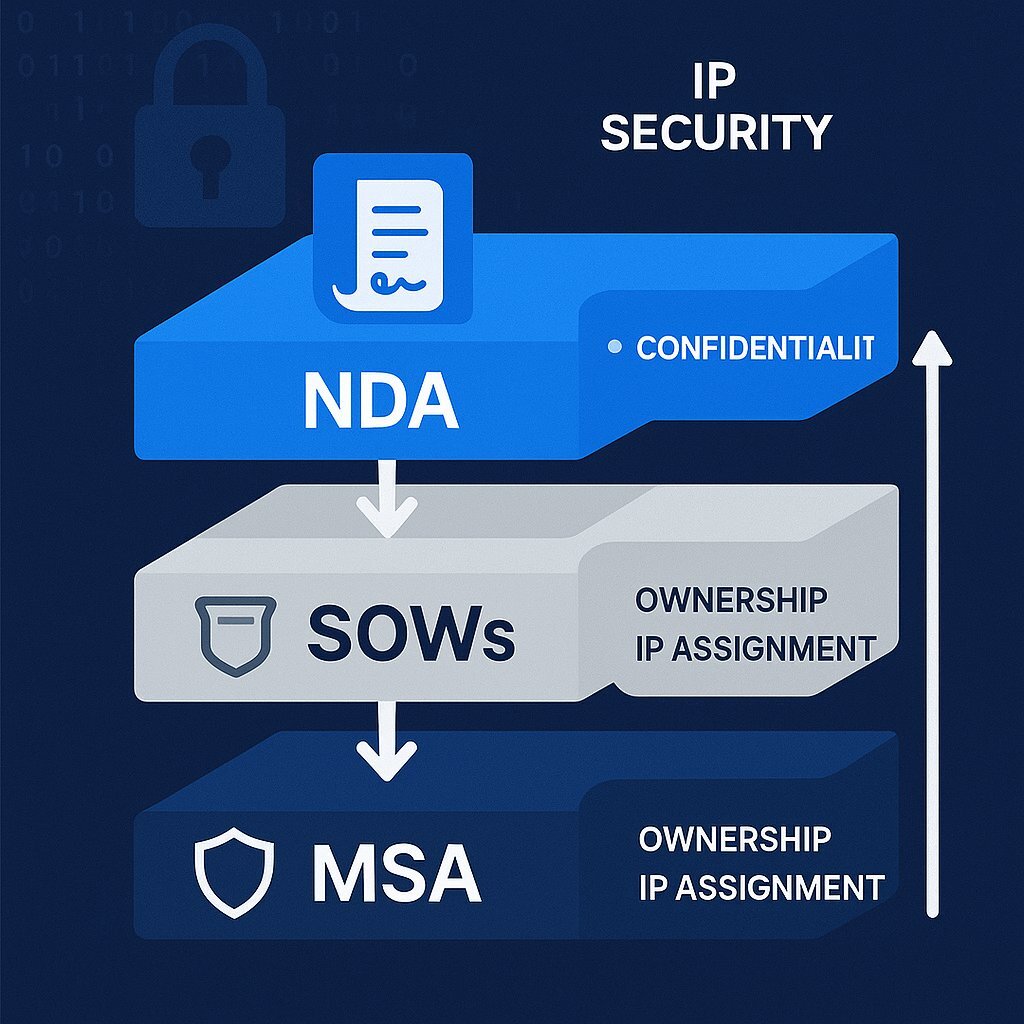
For any long-term or multi-project outsourcing relationship, the Master Service Agreement (MSA) is the foundational legal document. It establishes the overarching terms and conditions that will govern all future work. This is far more efficient than renegotiating core legal principles for every new project.
The MSA should be architected with IP protection as a central pillar. It sets the default rules for crucial areas such as confidentiality, data security standards, liability, indemnification, dispute resolution, and, most importantly, intellectual property ownership. Individual projects are then defined in separate Statements of Work (SOWs), which are shorter documents that detail the specific deliverables, timelines, and costs for that project. Crucially, each SOW should explicitly state that it is governed by the terms of the MSA. This two-tiered structure ensures that your core IP protections are consistently applied to all work performed by the partner.
Checklist Item 4: Secure Absolute Ownership: The "Work for Hire" and "IP Assignment" Mandate
This is the most critical clause in your entire legal framework. The default under copyright law is that the creator of a work is its owner. Without a contract that explicitly reverses this, the development firm you hire—not your company—could end up owning the very code you paid them to create. The agreement must state, in unambiguous terms, that your company is the sole and exclusive owner of all intellectual property created during the project.
Achieving this requires a two-pronged legal approach:
- Work for Hire: The first component is a "Work for Hire" clause. This legal doctrine stipulates that when work is created under specific conditions, the hiring party (your company) is considered the legal author and owner of the work from the moment of its creation. The contract should explicitly state that all deliverables and work products are to be considered "work made for hire" under the relevant copyright laws.
Explicit IP Assignment: Relying solely on a "Work for Hire" clause is a common and dangerous pitfall. The doctrine has specific limitations under U.S. Copyright Law and may not apply to all types of work created by independent contractors. Furthermore, its recognition and interpretation vary dramatically in international jurisdictions, creating significant ambiguity in cross-border outsourcing. To close this legal loophole, your contract
must include a separate, explicit IP Assignment clause . This clause acts as a crucial safety net. It states that, to the extent any work product is not legally deemed a "work made for hire," the contractor hereby irrevocably assigns, transfers, and conveys all of their rights, title, and interest in and to the intellectual property to your company. This assignment should be comprehensive, covering all drafts, notes, designs, code, and derivative works, ensuring that ownership is secured regardless of how a court might interpret the "work for hire" status.
Checklist Item 5: Engineer a Precision NDA for Software Development
A generic, boilerplate Non-Disclosure Agreement (NDA) is insufficient for the unique risks of software development. You are not just sharing business plans; you are sharing source code, algorithms, and technical secrets. The NDA must be a precision-engineered tool tailored to these specific risks.
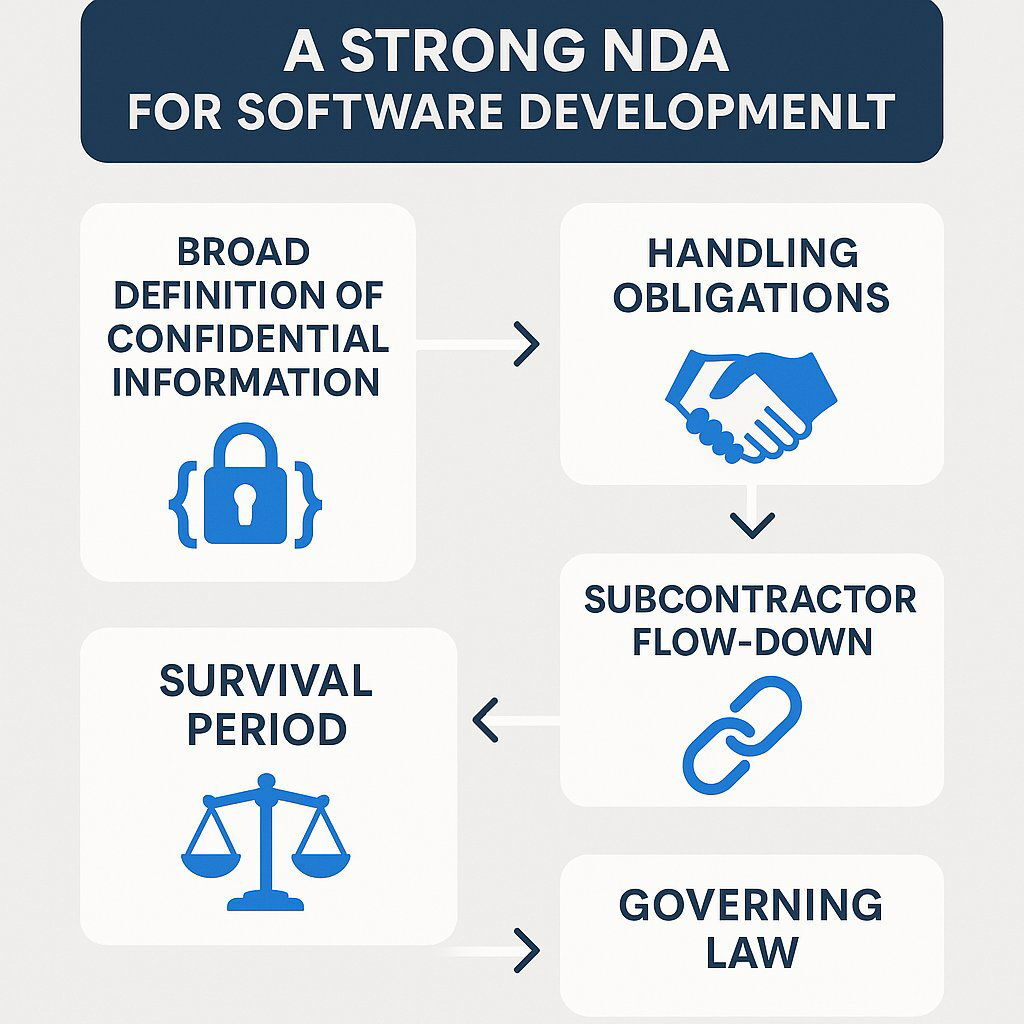
A high-assurance NDA for software development must include these non-negotiable clauses:
- Exhaustive Definition of "Confidential Information": This is the heart of the NDA. The definition must be both broad and specific, explicitly listing items such as source code, object code, proprietary algorithms, database schemas, user data, API keys, technical specifications, design documents, business strategies, and test plans. Vague terms like "proprietary information" are legally weak and should be avoided.
- Clear Obligations of the Receiving Party: The agreement must detail the recipient's responsibilities. This includes requirements for secure handling, storage on encrypted systems, and an absolute prohibition on storing confidential data on personal devices or insecure consumer cloud services. It should also mandate the secure destruction of all data upon project completion.
- Subcontractor Flow-Down Clause: If your primary vendor uses subcontractors, the chain of confidentiality is easily broken. The NDA must legally obligate your vendor to execute an equivalent NDA with any subcontractor before granting them access to your confidential information. Without this "flow-down" provision, you have no legal recourse against a leak from a third party.
- Survival Period: The value of your trade secrets does not expire when the project ends. The NDA's confidentiality obligations must "survive" the termination of the main contract for a significant and clearly defined period, typically 3 to 5 years, or even indefinitely for trade secrets.
- Governing Law and Jurisdiction: This clause is of paramount strategic importance, especially in international outsourcing. The NDA should specify that any disputes will be governed by the laws of a jurisdiction favorable to your company (e.g., your home state or country). This prevents the nightmare scenario of having to enforce your rights in a foreign court system with unfamiliar laws and procedures.
It is crucial to understand that these legal documents—the MSA, SOW, and NDA—form an interconnected system of protection. A weakness in one can cascade and undermine the others. For example, a powerful IP assignment clause in the MSA is rendered ineffective if the corresponding SOW is vague in its definition of "deliverables" or "work product," creating ambiguity about what IP is actually being assigned. Similarly, an NDA is weakened if it fails to properly define the source code being discussed as "confidential information." This interconnectedness demands a holistic legal review. The entire contractual framework must be viewed as a single, integrated IP protection mechanism, with each component reinforcing the others to eliminate any gaps or contradictions that could be exploited in a dispute.
The following chart breaks down the key components of a robust NDA, providing a clear visual guide for executives to use when reviewing these critical documents.
Phase 3: The Operational Shield — Securing the Day-to-Day Workflow
With a strong legal framework in place, the focus shifts to translating those contractual obligations into day-to-day operational reality. Legal agreements are only effective if they are supported by robust technical and procedural controls. This phase is about securing the active development process, where your IP is most frequently accessed and handled.
Checklist Item 6: Implement a Zero-Trust Access Model
The foundational principle of modern security is "never trust, always verify." This means abandoning the outdated idea of a secure network perimeter and instead assuming that threats can exist anywhere. In an outsourcing context, this translates to enforcing strict, granular controls over who can access what, and when.
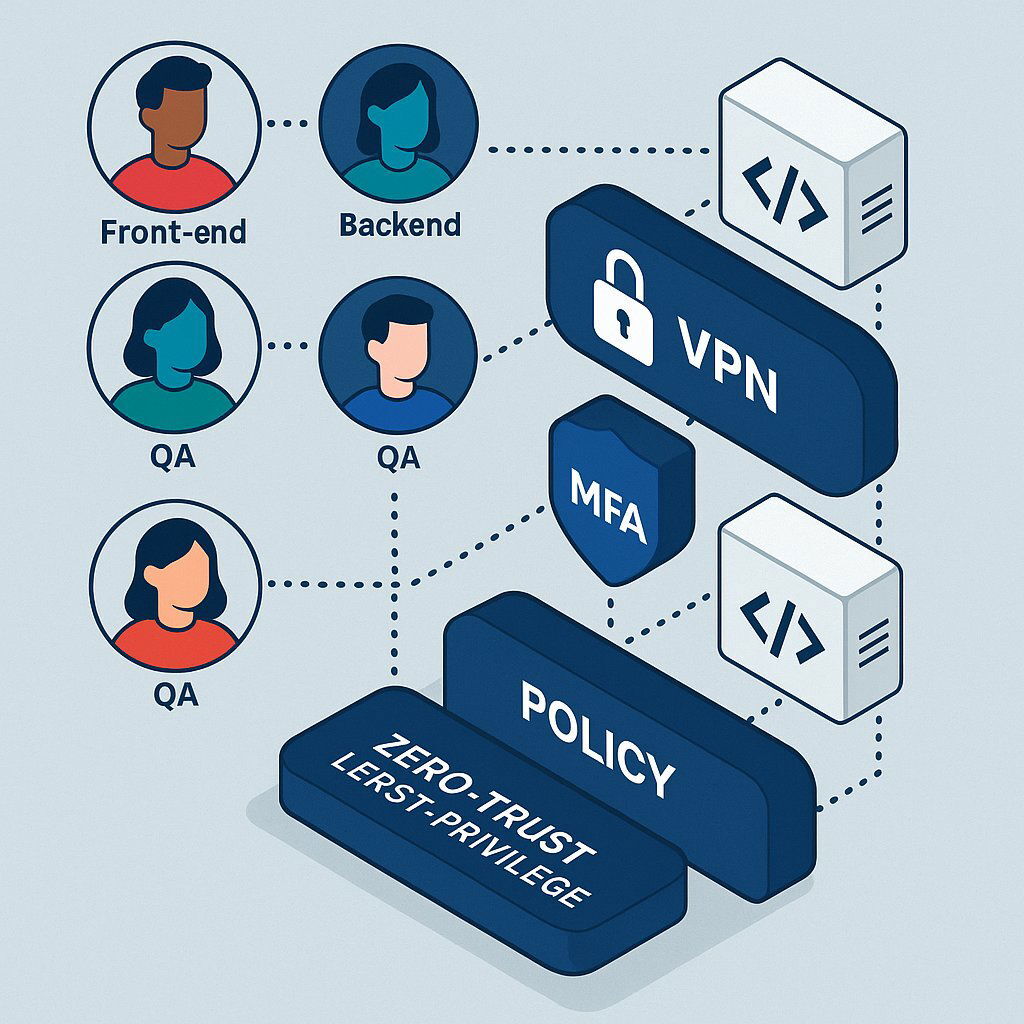
Implementing a zero-trust model involves several key practices:
- Principle of Least Privilege (PoLP): This is the golden rule of access control. Each developer, tester, and project manager should be granted the absolute minimum level of access required to perform their specific, assigned tasks—and nothing more. A developer working on the front-end UI should not have access to the back-end database schemas or the core algorithmic code.
- Role-Based Access Control (RBAC): RBAC is the system for implementing PoLP at scale. Permissions are assigned to defined roles (e.g., "Front-End Developer," "QA Tester," "Database Admin") rather than to individuals. This ensures that access rights are systematic, auditable, and tied to job function, not personal discretion.
- Technical Enforcement: These principles must be enforced with technology. Mandate the use of multi-factor authentication (MFA) for all accounts to prevent unauthorized access via stolen credentials. All network access to your systems and code repositories must be routed through a secure Virtual Private Network (VPN). Where possible, use IP allowlisting to restrict connections to only pre-approved, trusted IP addresses from the vendor's offices. Critically, all access attempts—successful or failed—must be logged and the logs should be regularly audited to detect anomalous behavior.
Checklist Item 7: Mandate a Secure Software Development Lifecycle (SDLC)
Protecting your IP is not just about preventing its theft; it is also about ensuring the integrity and security of the code being created. A vulnerability injected into your software—whether maliciously or accidentally—can be just as damaging as a data breach. Therefore, your contract must require the outsourcing partner to adhere to a formal, verifiable Secure Software Development Lifecycle (SDLC).
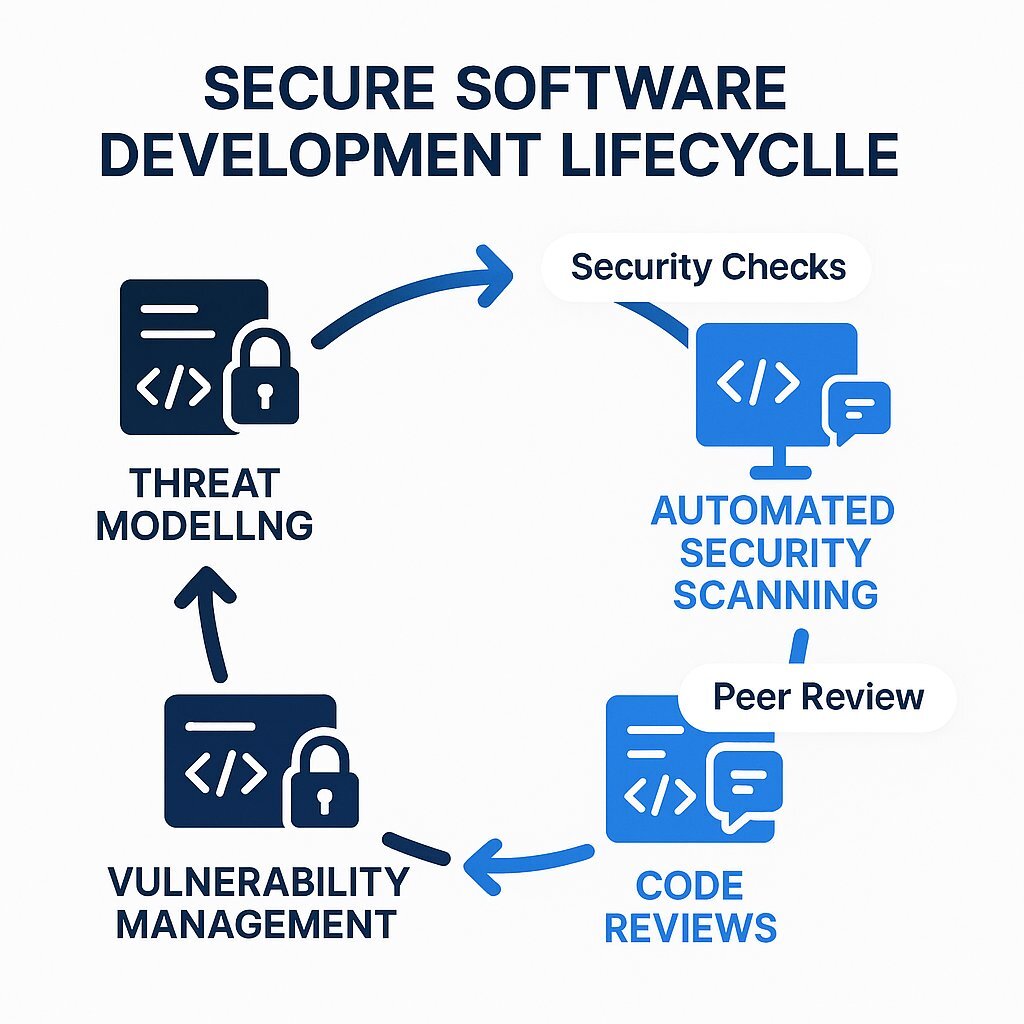
Key practices to demand and verify within the partner's SDLC include:
- Threat Modeling: Early in the design phase, the team must conduct a structured analysis to identify potential security threats and design mitigations for them. This proactive step prevents vulnerabilities from being baked into the software's architecture.
- Automated Security Scanning: Security cannot be an afterthought. The partner's Continuous Integration/Continuous Deployment (CI/CD) pipeline must integrate automated security scanning tools. This includes Static Application Security Testing (SAST), which analyzes source code for known vulnerability patterns, and Software Composition Analysis (SCA), which scans for vulnerabilities in third-party and open-source libraries.
- Mandatory Code Reviews: All code must undergo a review by at least one other developer before being merged into the main branch. These peer reviews should have a specific checklist item to evaluate the code against security best practices.
- Formal Vulnerability Management: The partner must have a documented process for tracking, prioritizing, and remediating any vulnerabilities discovered during development or testing. This ensures that security flaws are not ignored but are addressed in a timely and systematic manner.
Checklist Item 8: Fortify All Communication and Data Channels
Your intellectual property is at its most vulnerable when it is in motion—being transferred between developers, servers, and systems. A single unencrypted channel can be an open door for an attacker. It is imperative to mandate end-to-end encryption for all data and communications related to the project.
This mandate must cover two states of data:
- Data in Transit: All communications, whether through collaboration platforms like Slack or Microsoft Teams, email, or file transfers, must be encrypted using strong, modern protocols such as Transport Layer Security (TLS) 1.2 or higher. This ensures that even if the data is intercepted, it remains unreadable.
- Data at Rest: Encryption is not just for data on the move. All project-related data stored on servers, in databases, on laptops, and in backups must be encrypted using robust, industry-standard algorithms like AES-256. This protects your source code and sensitive information even if a physical device is lost or a server is compromised.
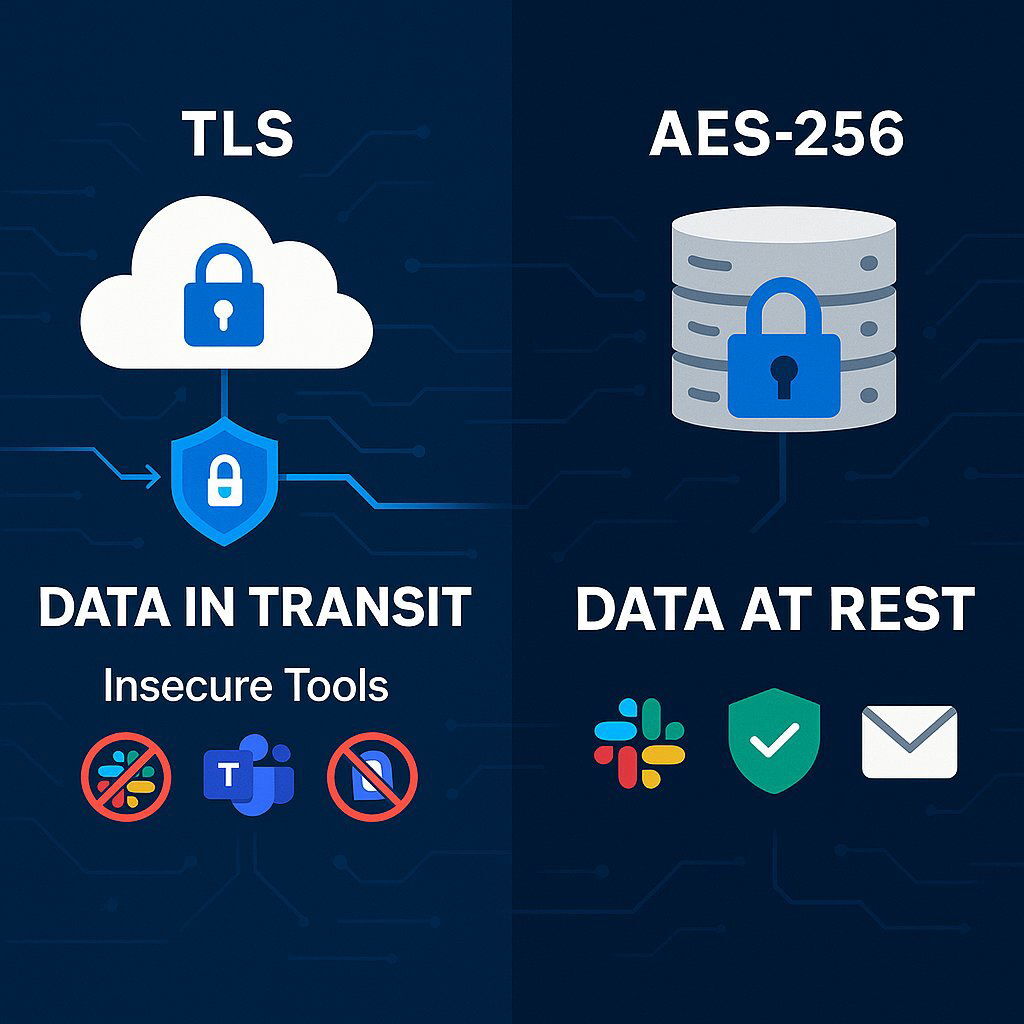
Furthermore, you must specify the tools for collaboration. The contract should mandate the use of enterprise-grade, secure platforms that you have vetted and approved. Explicitly forbid the use of insecure personal tools, such as personal email accounts, consumer-grade file-sharing services (e.g., personal Dropbox or Google Drive accounts), or unencrypted messaging apps for any project-related work.
The implementation of these operational controls serves a dual purpose. They are, first and foremost, essential security measures. However, they also function as a continuous, real-world test of your partner's security culture. The due diligence performed in Phase 1 is based on documentation and interviews—what the partner says they do. The operational phase reveals what they actually do. A partner who readily embraces strict access controls, transparently shares their secure SDLC metrics, and defaults to encrypted channels demonstrates a mature understanding of risk that aligns with their contractual promises. Conversely, a partner who pushes back on these controls, complaining that they are inconvenient or slow down development, exposes a critical cultural gap. This resistance is a clear signal that their ingrained practices do not match their stated policies, posing a significant long-term threat to your IP and validating (or invalidating) your initial assessment.
Phase 4: The Secure Disengagement — Protecting Your IP After Project Completion
The end of a software development project is a moment of high risk that is frequently overlooked. Without a formal, secure disengagement process, your intellectual property can remain on vendor systems indefinitely, creating a persistent vulnerability long after the final invoice is paid. The offboarding process must be as meticulously planned and executed as the onboarding process.
Checklist Item 9: Enforce a Strict Offboarding and Data Destruction Protocol
Your MSA must contain a detailed clause outlining the mandatory procedures for project conclusion and contract termination. This is not a handshake agreement; it is a contractual obligation with clear steps and verification requirements.
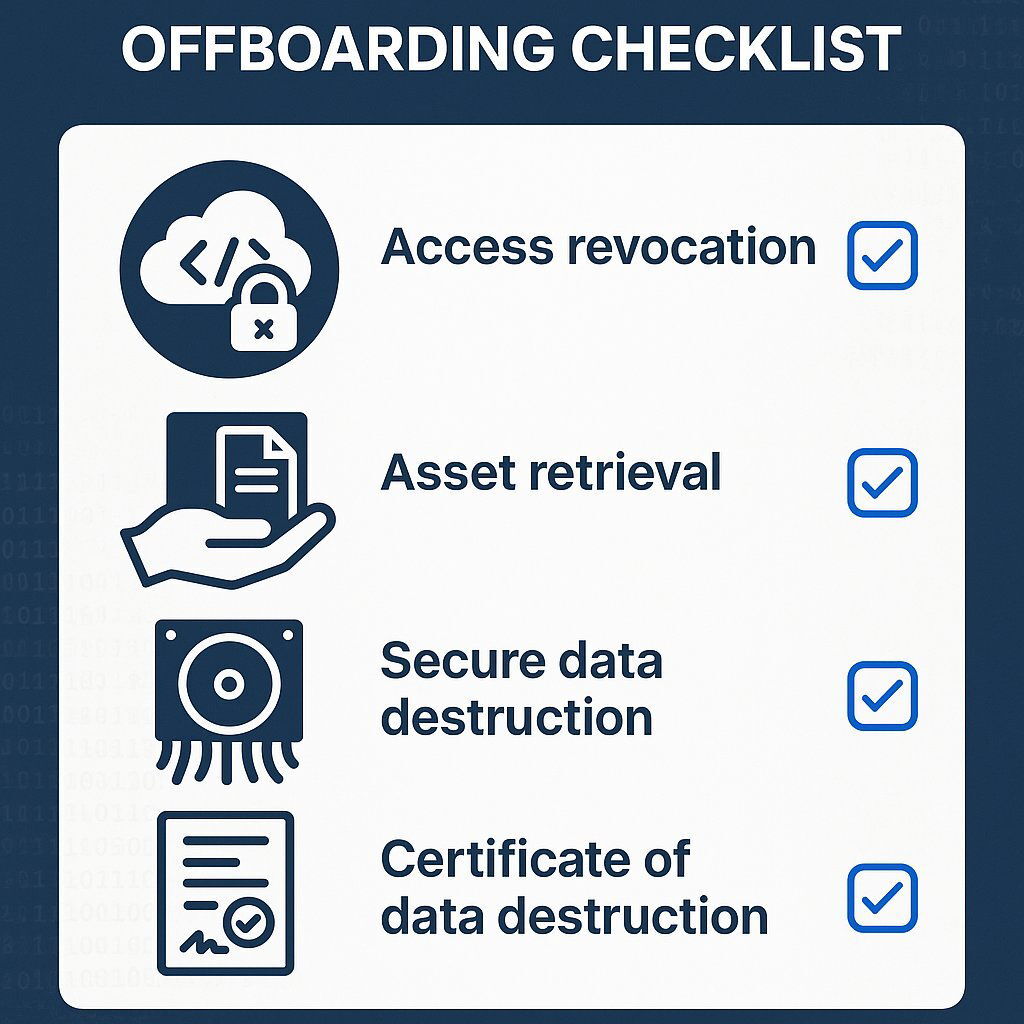
The critical offboarding steps include:
- Immediate and Universal Access Revocation: On the final day of the engagement, all access credentials for all vendor personnel must be terminated. This includes access to code repositories (e.g., GitHub, Azure DevOps), servers, cloud environments (AWS, Azure, GCP), databases, project management tools (e.g., Jira), and communication platforms (e.g., Slack, Teams). A comprehensive checklist should be used to ensure no system is overlooked.
- Asset Retrieval: A formal process must be in place to ensure the return of all company-owned assets, both physical (e.g., laptops, security tokens) and digital (e.g., software licenses, data files).
- Secure Data Destruction: The contract must require the vendor to securely and permanently delete all copies of your confidential information and project-related data from all their systems. This includes servers, employee laptops, and backup media. A simple file deletion is insufficient, as the data can often be recovered. The requirement should be for secure data erasure methods (e.g., cryptographic erasure or multi-pass overwriting) that render the data unrecoverable.
- Certificate of Destruction: For projects involving highly sensitive IP or regulated data, it is best practice to contractually require the vendor to provide a formal, signed Certificate of Data Destruction . This document serves as legal proof that they have complied with their data destruction obligations, providing a clear audit trail and an additional layer of accountability.
Conclusion: Transforming IP Protection from a Cost Center to a Competitive Advantage
The journey of outsourcing software development is fraught with IP-related risks, but these risks are manageable. The key is to move beyond a reactive, contract-only mindset and embrace a holistic strategy that integrates legal, operational, and relational safeguards. A comprehensive IP protection framework, woven through every phase of the partnership, is not an inhibitor of speed or a cost center. It is a crucial enabler of secure, sustainable innovation. It builds the trust necessary for deep, strategic partnerships, allowing your organization to fully leverage the global talent pool without compromising its most valuable assets.
For executives ready to put these principles into action, the path forward is clear.
Actionable Next Steps:
- Audit Your Current State: Review your existing outsourcing agreements and vendor relationships against the checklist provided in this playbook. Identify immediate gaps in your legal contracts and operational controls. For additional guidance on bridging the strategy-execution gap and maximizing ROI from your technology initiatives, consider our five-step alignment framework.
- Verify Your Partners: Schedule a formal security and process review with your current outsourcing partners. Use the due diligence scorecard as a guide to validate their operational controls and ensure they align with your contractual requirements. For security leaders aiming to embed protection at every stage, see our DevSecOps executive guide for practical recommendations.
- Mandate for the Future: Incorporate this checklist as a non-negotiable standard in your vendor selection and onboarding process for all future outsourcing initiatives. Make robust IP protection a prerequisite for partnership. And if you're seeking to build a culture of continuous improvement and technical maturity, review the actionable strategies in upskilling your software engineers for AI as part of your long-term resilience plan.
Navigating this landscape requires expertise and a partner who has built their entire service delivery model around these principles of security and trust. Firms like Baytech Consulting understand that protecting a client's intellectual property is as critical as writing clean, efficient code. They don't see security as an add-on; it is integral to their process. If you are ready to build your next innovative product on a foundation of security and trust, we invite you to contact Baytech Consulting for a consultation to assess and strengthen your own IP protection posture. And for an inside look at how process frameworks like Agile methodology enhance project transparency and successful collaboration, our service overview offers further insights.
Supporting Articles
- Patent Protection for Software-Implemented Inventions (World Intellectual Property Organization - WIPO)
- Secure Software Development: Best Practices, Frameworks, and Resources (Hyperproof)
- What are IP Assignment Agreements? (Wyrick Robbins Yates & Ponton LLP)
About Baytech
At Baytech Consulting, we specialize in guiding businesses through this process, helping you build scalable, efficient, and high-performing software that evolves with your needs. Our MVP first approach helps our clients minimize upfront costs and maximize ROI. Ready to take the next step in your software development journey? Contact us today to learn how we can help you achieve your goals with a phased development approach.
About the Author

Bryan Reynolds is an accomplished technology executive with more than 25 years of experience leading innovation in the software industry. As the CEO and founder of Baytech Consulting, he has built a reputation for delivering custom software solutions that help businesses streamline operations, enhance customer experiences, and drive growth.
Bryan’s expertise spans custom software development, cloud infrastructure, artificial intelligence, and strategic business consulting, making him a trusted advisor and thought leader across a wide range of industries.


