
The People Side of System Migrations: Strategies for 2025
December 22, 2025 / Bryan ReynoldsExecutive Summary: The Paradox of Digital Progress
In the high-stakes theater of enterprise technology, a silent crisis is unfolding. It is a crisis not of capability, but of adoption. We live in an era of unprecedented computational power, where cloud architectures scale infinitely, artificial intelligence approximates human reasoning, and data flows in real-time streams across the globe. Yet, for the Chief Information Officer (CIO), the VP of Engineering, and the Project Manager, the daily reality often feels less like a triumph of innovation and more like a battle for survival.
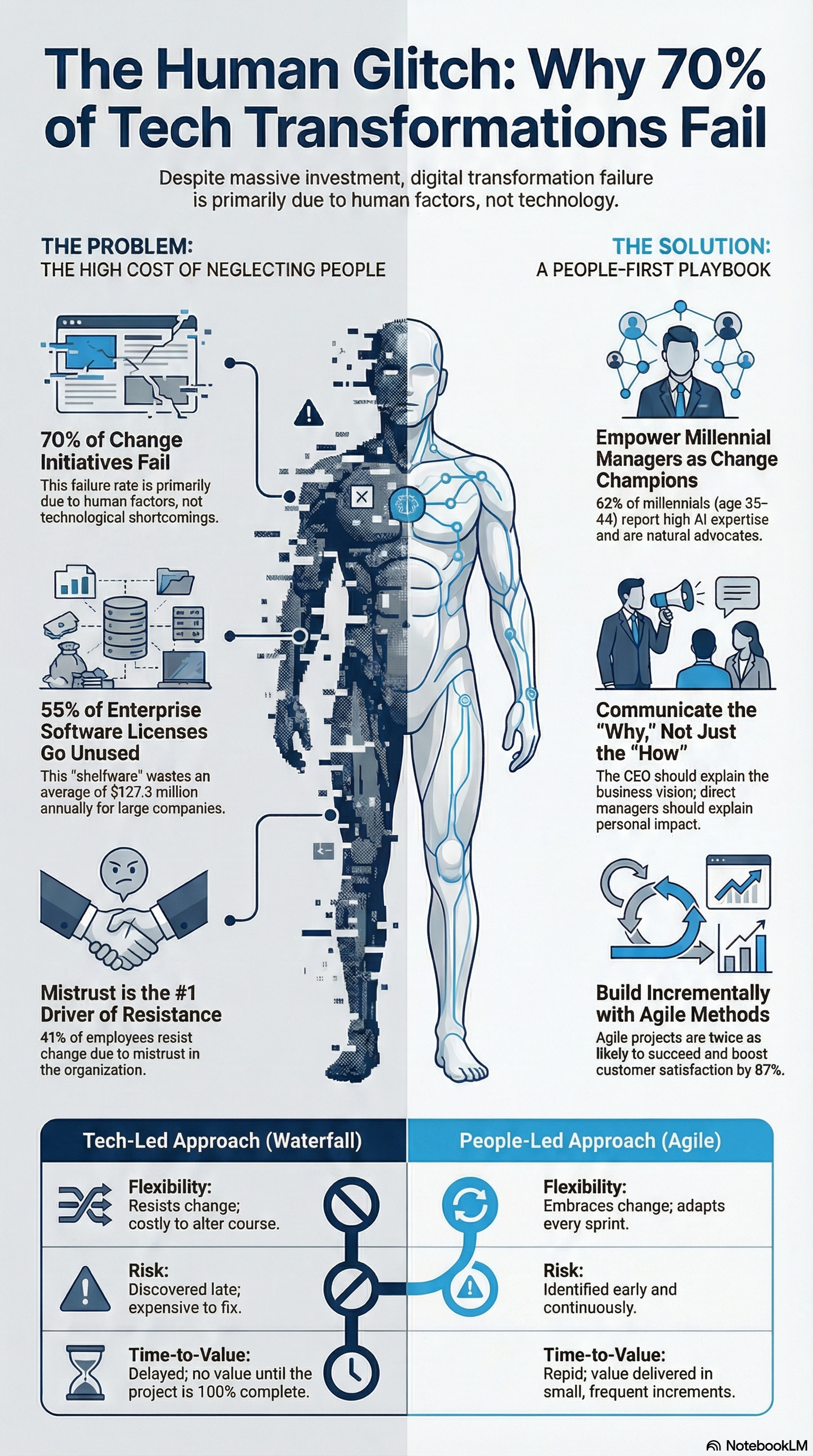
The statistics are as stubborn as they are sobering. Despite decades of methodology refinement—from Waterfall to Agile to DevOps—the failure rate of major digital transformations remains fixed at approximately 70%. 1 This figure, cited by McKinsey and echoed across the industry, suggests a systemic blind spot in how we approach technology projects. We are engineering systems with near-perfect reliability, yet we are deploying them into organizational cultures that are inherently unstable, resistant, and fearful.
This report posits a fundamental thesis: The primary vector of failure in modern technology projects is not technical debt; it is emotional debt. It is the accumulated friction, mistrust, and anxiety of the human beings expected to operate the new machinery. When a brilliant technical solution fails to gain traction, it is rarely because the database schema was inefficient or the API latency was too high. It is because the users—the biological endpoints of the digital system—rejected the transplant.
For the B2B technology leader, solving this requires a pivot in perspective. We must stop viewing "Change Management" as a "soft skill" relegated to HR or a generic communications plan tacked onto the end of a Gantt chart. We must view it as an engineering constraint, as critical and deterministic as bandwidth or storage capacity.
In this comprehensive report, we will deconstruct the mechanics of human resistance through the lens of the technologist. We will explore how strategic frameworks—specifically Baytech Consulting’s Tailored Tech Advantage and Rapid Agile Deployment —serve not just as development methodologies, but as psychological safety nets that mitigate risk. 2 We will provide a granular, four-step framework for navigating the "Valley of Despair," supported by data, case studies, and actionable strategies for the visionary executive.

Part I: The Anatomy of Failure
1.1 The Engineering Blind Spot
Technologists are trained in deterministic logic. In the world of code, an input of A plus a function of B will invariably yield C. If it does not, there is a bug, and that bug can be isolated, reproduced, and patched. The systems we build are rational, rule-based, and obedient.
Human beings, however, are non-deterministic, emotional, and fiercely protective of their status quo. When a CIO announces a migration from a legacy on-premise ERP to a cloud-based SaaS platform, they see a reduction in server maintenance costs and an increase in data agility. The Accounts Payable clerk, however, sees something entirely different. They see the obsolescence of the keyboard shortcuts they have memorized over 15 years. They see a loss of autonomy. They see a threat to their professional competence.

This disconnect creates what we call the Engineering Blind Spot. It is the assumption that utility equals adoption. The logic goes: "This new system is faster, prettier, and more powerful. Therefore, users will love it." The reality is that users do not care about power; they care about mastery. A legacy system, no matter how clunky, is a known quantity. The user has mastered it. A new system, no matter how sleek, renders them a novice again.
The Data of Disconnect
The industry data paints a stark picture of this misalignment:
- The Trust Deficit: 41% of employees cite mistrust in the organization as the primary driver of resistance to change. 3 This is not a UI/UX problem; it is a cultural problem.
- The "Why" Void: 39% of employees resist simply because they do not understand the reason for the change. 3 They perceive the migration as an arbitrary mandate from an out-of-touch executive suite.
- The Leadership Gap: While 92% of companies plan to increase AI investments, only 1% of leaders describe their organizations as "mature" in deployment. 4 This chasm between ambition and reality is filled with confused, anxious employees.
The financial consequences of this blind spot are staggering. The phenomenon of "Shelfware"—enterprise software that is purchased but never used—is a direct result of failed adoption. It is estimated that 55% of large enterprise software licenses go unused , resulting in an average of $127.3 million in wasted spend annually for large organizations. 5 This is not just a rounding error; it is a massive capital inefficiency that would be unacceptable in any other department.
1.2 The Neuroscience of Resistance (The SCARF Model)
To engineer a solution to resistance, we must understand its biological origins. Resistance is not insubordination; it is a neurological defense mechanism. When a human faces a major change, the amygdala—the brain's threat detection center—activates. This triggers a "fight or flight" response that hijacks the prefrontal cortex, the center of logic, planning, and collaboration.
We can analyze this through the SCARF Model (Status, Certainty, Autonomy, Relatedness, Fairness), a framework from neuroleadership that explains social threats. A system migration often attacks all five domains simultaneously:
Table 1: The SCARF Threat Analysis of System Migration
| Domain | The Threat Trigger | The User's Internal Monologue | The Traditional "Tech-Led" Error |
|---|---|---|---|
| Status | Loss of expertise | "I was the go-to person for the old system. Now I know nothing. My value is zero." | Ignoring legacy power users; treating the old system as "garbage." |
| Certainty | Unknown future workflows | "Will I still have a job? Will this take twice as long to do?" | "Big Bang" launches with no previews; keeping the roadmap secret. |
| Autonomy | Forced process changes | "Some developer in Silicon Valley decided how I should do my job." | Buying rigid COTS (Commercial Off-The-Shelf) software that forces process changes. |
| Relatedness | Disruption of teams | "I won't be working with my favorite colleague anymore." | Restructuring teams based on software modules rather than human relationships. |
| Fairness | Increased workload during transition | "I have to learn this and do my day job for the same pay?" | Failing to backfill roles or reduce quotas during the migration period. |
1.3 The "Tech-Led" vs. "People-Led" Divergence

The root cause of most failed migrations is a "Tech-Led" strategy. This approach prioritizes the technology stack, vendor capabilities, and feature lists. The user is treated as a downstream consumer who must adapt to the tool.
Contrast this with a "People-Led" strategy, exemplified by companies like AutoStore, which focused on "brand advocates" and trust-building during their digital transformation. 6 In a people-led approach, the technology is treated as an enabler of human potential, not a replacement for it.
The "Tailored Tech" Solution:
This is where Baytech Consulting’s Tailored Tech Advantage becomes a strategic asset in change management.2 By opting for custom software solutions over rigid off-the-shelf products, an organization can align the technology to the user’s existing mental models. If you're seeking a broader look at how custom software product development services can transform your business, it's crucial to approach transformation through people-centric engineering, not just technology implementation.
- Cognitive Load Reduction: Custom software can be stripped of the 80% of features that COTS platforms carry but users never touch. This simplification reduces the cognitive load and the "fear factor" of the new interface.
- Workflow Respect: Tailored solutions digitize the unique workflows that make the business successful, rather than forcing the business to conform to a generic industry standard. This preserves Autonomy and Status for the users.
Part II: Step 1 - Stakeholder Engagement (The Engineering of Trust)
2.1 Moving Beyond Requirements Gathering
In traditional project management, stakeholder engagement is often reduced to a "Requirements Gathering" phase—a series of interviews at the start of the project where users list what they want, and engineers list what is possible. Once the document is signed, the users are ignored until User Acceptance Testing (UAT) months later.
This "waterfall" approach to engagement is fatal. It assumes that users know what they want (they often don't) and that their needs won't change over time (they always do). More importantly, it denies users the psychological sense of ownership.
The New Mandate: Engagement must be continuous, cyclical, and co-creative. It is not about asking users what features they want; it is about observing how they work and inviting them to co-architect the solution.
2.2 The Shadow Org Chart
To engage stakeholders effectively, the CIO must look beyond the official organizational chart. Every company has a "Shadow Org Chart"—a network of influence that dictates how information flows and how opinions are formed. You must identify and recruit from three specific archetypes within this shadow network 7 :
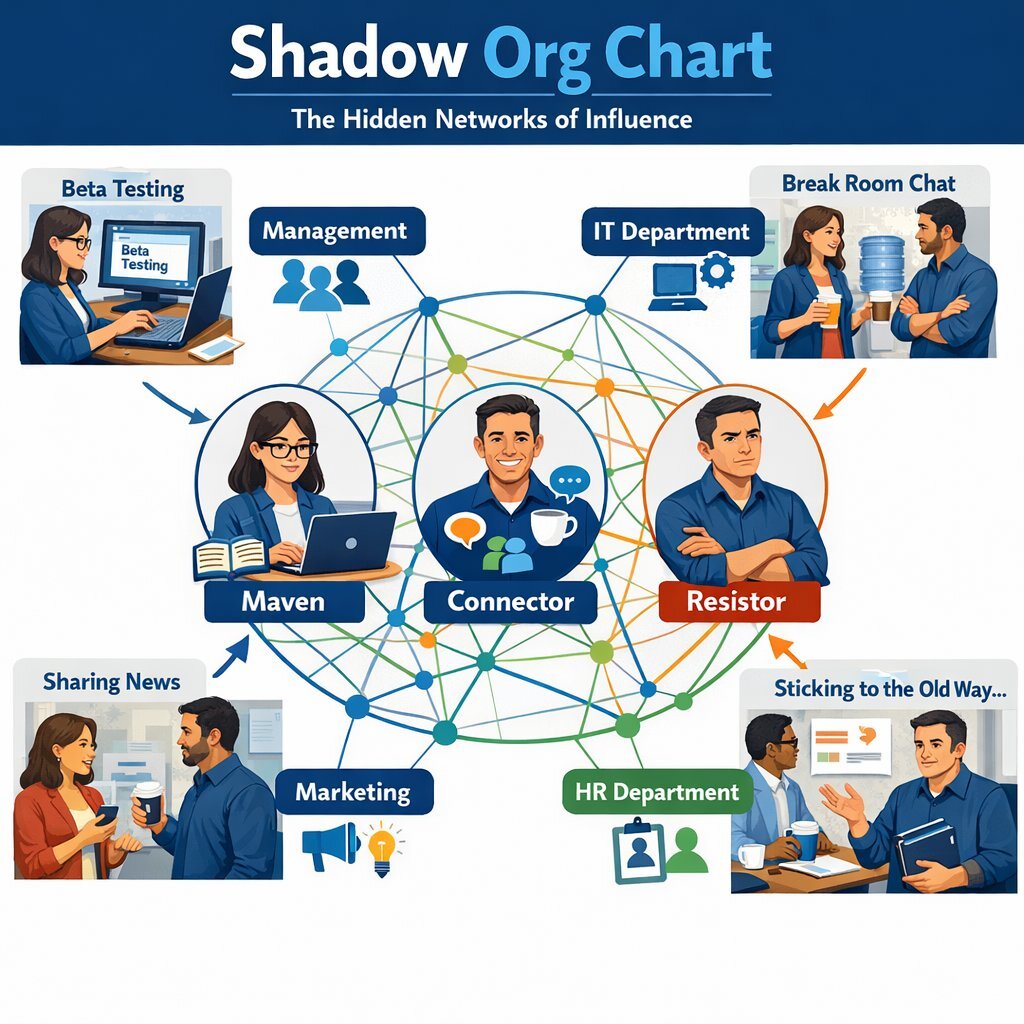
- The Mavens (Information Specialists):
- Who they are: The deep experts. The ones who know the legacy system's keyboard shortcuts and hidden menus.
- Why they matter: If they reject the new system, they will produce detailed, technical critiques that validate everyone else's resistance. If they accept it, their competence validates the tool.
- Engagement Strategy: Bring them into the "Inner Circle." Give them beta access. Ask them to try to break the system. Appeal to their pride as experts.
- The Connectors (Social Hubs):
- Who they are: The people who know everyone. They organize the office birthday parties and fantasy leagues.
- Why they matter: They control the emotional narrative. If a Connector says, "This new rollout is a disaster," that sentiment spreads virally across departments, bypassing official communication channels.
- Engagement Strategy: Focus on the "WIIFM" (What's In It For Me). If the Connector sees that the new system makes life easier for their friends, they will evangelize it.
- The Resistors (The Old Guard):
- Who they are: Often long-tenured employees who have seen previous "transformations" fail.
- Why they matter: Their cynicism is contagious. However, their resistance is often rooted in deep knowledge of edge cases that the engineers missed.
- Engagement Strategy: Do not marginalize them. Listen to them. Their grumbling often contains the blueprint for the system's most critical failure points. "The last time we tried this, the inventory sync failed during the holiday rush." That is not negativity; that is a requirement.
2.3 Co-Creation via Rapid Agile Deployment
The most powerful tool for engagement is the development methodology itself. Rapid Agile Deployment , a core strength of Baytech Consulting, is uniquely suited to mitigate resistance because it relies on frequent, transparent delivery of working software. 2
The Psychology of Agile:
- Short Feedback Loops: Instead of waiting 12 months for a "Big Bang" launch, stakeholders see a working MVP (Minimum Viable Product) in weeks. This reduces Certainty threats because the "monster" is revealed in small, manageable pieces. For a deep dive into event-driven real-time feedback, see this Kafka real-time data processing guide.
- The "I Built That" Effect: When a user suggests a tweak to a button placement in Sprint 2, and sees that tweak implemented in Sprint 3, they develop Psychological Ownership. The system is no longer "IT's tool"; it is "My tool."
- Transparency as Trust: 75% of executives say their business functions compete rather than collaborate on digital projects. 1 Agile forces collaboration through regular Sprint Reviews. There are no secrets. The limitations and bugs are visible, which paradoxically builds trust because the IT team is seen as honest.
Actionable Tactic: The "Design Partner" Program
Create a formal "Design Partner" group comprising 1-2 representatives from each key user persona (e.g., one Sales Rep, one Accountant, one Warehouse Manager).
- Commitment: They commit 2 hours a week to review builds.
- Reward: They get early access, "Power User" certification, and public recognition.
- Output: They become the "Change Champions" who will train their peers during the wider rollout.
Part III: Step 2 - Clear Communication (The Architecture of Meaning)
3.1 The "Why" Before the "How"
Most migration communication fails because it focuses on the "How" and the "When"—logins, URLs, downtime schedules—while ignoring the "Why."
Nietzsche wrote, "He who has a why to live can bear almost any how." The same applies to software. Users can bear buggy interfaces, slow load times, and confusing menus if they believe the destination is worth the journey. If they don't, every minor glitch becomes evidence of failure.
Constructing the Narrative:
The communication plan must tell a story. It should follow a dramatic arc:
- The Inciting Incident (The Problem): We must be brutally honest about why the current state is untenable. "Our legacy servers are at risk of catastrophic failure that could lose customer data." "Our current manual processes are costing us 20 hours a week that we could spend on strategy."
- The Vision (The Promise): Paint a vivid picture of the future. "Imagine closing the books in 2 days instead of 10." "Imagine having customer history available on your phone before you walk into the meeting."
- The Path (The Plan): Here is the roadmap. Here is the support. We are not throwing you into the deep end.
3.2 The Physics of the Sender
In communication theory, the credibility of the message depends entirely on the sender. Corporate communication often defaults to the "Project Manager" or "Internal Comms" alias as the sender. This is a mistake.
Research indicates a specific preference for senders based on the message type 7 :
- Strategic & Business Rationale: Must come from the CEO or President. Only they have the authority to define the business direction. If the CIO sends this, it looks like a "tech project." If the CEO sends it, it looks like a "business imperative."
- Personal Impact & Procedures: Must come from the Direct Supervisor. Employees trust their immediate boss to understand their daily reality. If the CEO explains how to log in, it feels micromanaged. If the Project Manager explains it, it feels distant. The Direct Manager can say, "I know this form is annoying, but here is the shortcut I found."
Table 2: The Communication Matrix
| Message Type | The Sender | Key Theme | Channel |
|---|---|---|---|
| The Announcement | CEO / President | "Survival & Growth" | Town Hall + Video Email |
| The Solution | CIO / VP Engineering | "Modernization & Security" | Blog Post + Demo Video |
| The Timeline | Project Manager | "Logistics & Support" | Intranet / Slack / Email |
| The "WIIFM" | Direct Manager | "Team Impact & Benefits" | Team Meeting (Face-to-Face) |
| The "How-To" | Change Champion | "Tips & Tricks" | Slack / Lunch-and-Learn |
3.3 Dealing with "Technical Debt" and "Refactoring"
A specific challenge for VPs of Engineering is communicating migrations driven by Technical Debt. These projects often have zero visible changes for the end-user (e.g., moving from on-premise servers to AWS, or refactoring a monolith to microservices).
To the business, this looks like "IT spending money to stay in the same place." This perception kills budget and patience. For a thorough understanding of why adaptive maintenance is vital for change management, it helps to see technical debt as a hidden risk to business continuity.
The Strategy: Translate technical debt into business risk. 9
- Don't Say: "We need to upgrade our Angular framework because version 1 is deprecated."
- Do Say: "Our current platform has security vulnerabilities that put client data at risk. Upgrading now prevents a potential breach and will allow us to deploy new features 40% faster next year."
- The Analogy: Use the "Home Renovation" analogy. "We are fixing the foundation. You won't see a new kitchen yet, but the house won't collapse in the next storm."
3.4 Managing the Rumor Mill
In the absence of clear communication, the "Shadow Org Chart" will fill the void with rumors. "They are automating our jobs." "The new system tracks our keystrokes."
Tactic: The "Myth-Buster" Portal
Create a visible section on the project intranet or a pinned Slack post dedicated to addressing rumors head-on.
- Rumor: "Is AI going to replace the scheduling team?"
- Response: "No. The AI tool is designed to handle the rote scheduling of standard appointments. This will free up the scheduling team to handle complex, high-value client needs that require human judgment. We expect the team size to remain stable, but the work to become less repetitive."
This level of transparency builds immense psychological safety.
Part IV: Step 3 - Comprehensive Training (The Death of the PDF)
4.1 The Forgetting Curve
The traditional training model—a 4-hour classroom session or a 100-page PDF manual—is scientifically flawed. The "Ebbinghaus Forgetting Curve" dictates that humans forget approximately 70% of new information within 24 hours if they do not apply it immediately.
When we train users on Monday for a system that goes live on Friday, we are essentially wasting time. By Friday, they will remember only that the system exists, but not how to use it. They will panic, and they will call the Help Desk.
4.2 Just-in-Time Enablement (JIT)
The solution is to move from "Just-in-Case" training (teaching everything) to "Just-in-Time" training (teaching what is needed, when it is needed). 7
Digital Adoption Platforms (DAPs):
Modern change management relies heavily on DAPs (like Whatfix, WalkMe, or Pendo). These tools overlay the application interface with interactive guidance, reducing learning friction and expediting value realization. See our deeper discussion in Harnessing Generative AI for Enterprise Success in 2025 for how these platforms work hand-in-hand with contemporary enterprise tools.
- Mechanism: Instead of reading a manual on "How to Create an Invoice," the user clicks "Create Invoice" and a bubble appears on the screen pointing to the first field: "Enter Customer Name." Once they type it, the bubble moves to the next field.
- Impact: This is "learning in the flow of work." It reduces the cognitive load to near zero. The user does not need to memorize the process; they just need to follow the breadcrumbs.
- ROI: Research shows DAPs can reduce time-to-proficiency by 50% and support tickets by 45%. 7
4.3 The Change Champion Network
Technology cannot solve everything. Sometimes, a user just needs a human to look at their screen. This is where the Change Champion Network (identified in Step 1) activates. 11

Structuring the Network:
- Ratio: Aim for 1 Champion per 15-20 users.
- Visual Identification: During Go-Live week, give Champions a physical identifier (a specific t-shirt, a balloon at their desk, a special badge icon on Slack).
- The "Floor-Walking" Strategy: In the first days of migration, Champions should not be doing their regular work. They should be "walking the floor" (virtually or physically), proactively asking, "How is it going? Can I help you with that?"
- The Feedback Loop: Champions are also the eyes and ears of the project team. They can report back: "Everyone in Accounting is struggling with the new export feature." This allows the engineering team to deploy a hotfix or a targeted guide immediately.
4.4 Gamification and "Safe Sandboxes"
Fear of breaking the system is a major inhibitor of adoption. Users are terrified they will accidentally delete a client or send a wrong invoice.
The Sandbox Strategy:
Create a replica of the production environment with anonymized data. Give users access 2 weeks before launch.
- The Scavenger Hunt: Don't just give them access; give them a mission. "Log in, find the customer 'Acme Corp', change their address to 123 Main St, and create a quote for $500."
- Prizes: The first 50 people to complete the scavenger hunt get a gift card or a half-day off.
- Psychology: This builds muscle memory in a low-stakes environment. By the time they log into the real system, the neural pathways for the core tasks are already formed.
Part V: Step 4 - Feedback Loops (The Agile Heartbeat)
5.1 Feedback as a System Metric
In a "People-Led" migration, user sentiment is a metric as critical as server latency or uptime. If the server is green but the users are red, the system is failing.
We must build telemetry for human sentiment.
- The Pulse Survey: Use tools like Slack Polly or Microsoft Forms to send one-question surveys during the rollout.
- Question: "On a scale of 1-5, how confident do you feel using the new Search feature?"
- Trigger: Send this 3 days after training, and 3 days after Go-Live.
- In-App Feedback: Embed a "Thumbs Up / Thumbs Down" widget on key new features. If a specific page gets 80% Thumbs Down, you have an immediate heatmap of friction. 13
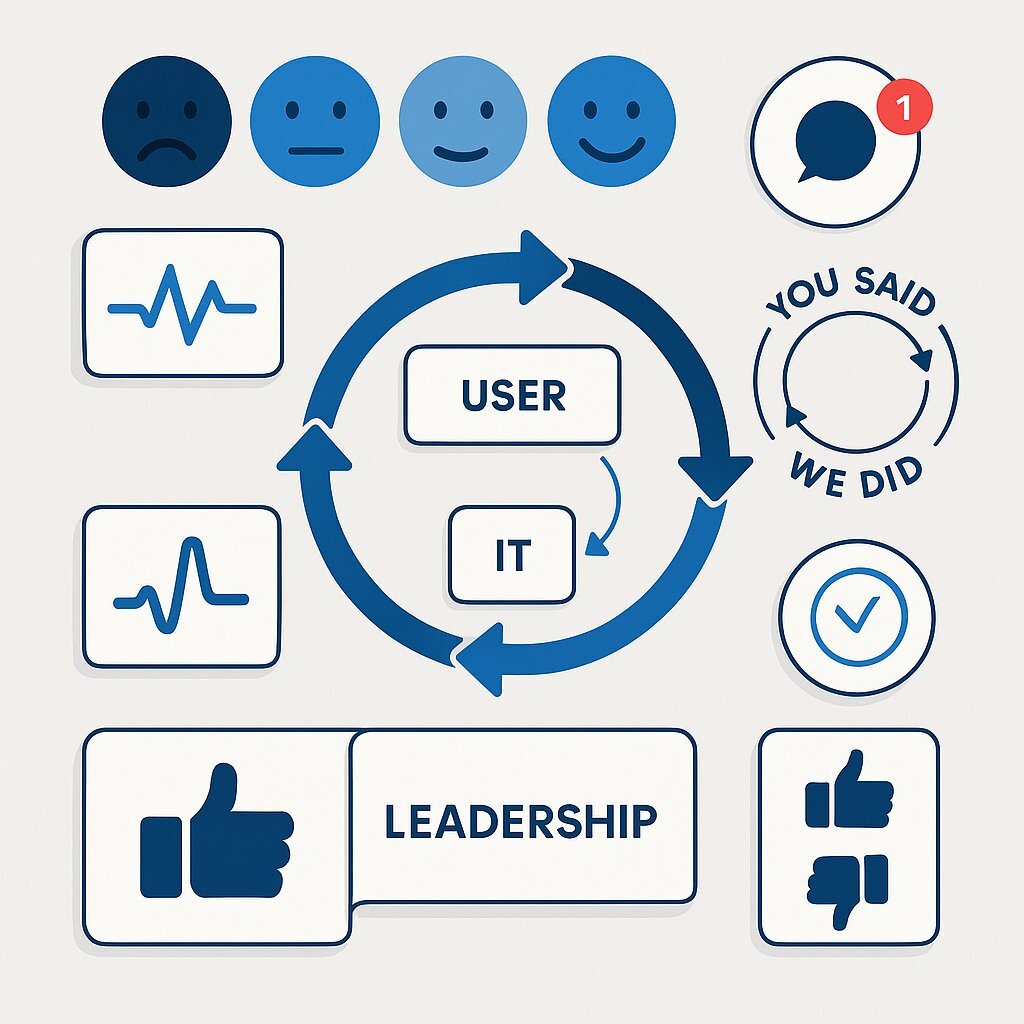
5.2 Closing the Loop: The "You Said, We Did" Campaign
Collecting feedback is dangerous if you don't act on it. "Feedback Black Holes"—where input goes in and nothing comes out—breed cynicism.
The Action Plan:
- Acknowledge: "We heard you. The font size on the mobile dashboard is too small."
- Act: Use the Rapid Agile Deployment capability to fix it in the next sprint. 14
- Announce: "You said the font was small. We fixed it. It is now live."
This cycle is the most powerful trust-builder available to a CIO. It proves that the technology serves the user, not the other way around.
5.3 Monitoring "Shadow Metrics"
Sometimes users won't tell you they hate the system; they will just stop using it. You must monitor "Shadow Metrics":
- The Excel Index: Monitor the shared drives. If the number of new Excel spreadsheets increases after you launch the new ERP, it means users are bypassing the system to do their work manually. This is a critical failure indicator.
- Support Ticket Volume: A spike at launch is normal. A sustained high volume 4 weeks later indicates a UX failure or a training gap. For an exploration of the link between tool trust and business risk, see AI trust paradox in software development.
- Login Frequency: Who hasn't logged in for 3 days? Your Change Champions should pay them a visit.
Part VI: The Financial Case for Change Management
6.1 The ROI of Empathy
For the Strategic CFO, Change Management is often viewed as a "nice to have"—an extra line item for consultants and training that can be cut when budgets get tight. This is a mathematical error.
The Cost of Shelfware:
Let’s calculate the cost of not managing change. It's a smart practice to examine proven methodology to mitigate these losses—see our guide to software outsourcing strategies for approaches that prioritise both people and process.
- Scenario: A company spends $1,000,000 annually on a Salesforce license for 1,000 users.
- Reality: Without effective change management, adoption hovers at 40%. Users use it only for basic contact lookups, ignoring the advanced analytics and automation features.
- Loss: The company is wasting $600,000 a year on unused capacity.
- The Fix: A $50,000 investment in a Change Management program to boost adoption to 80% yields a $400,000 return in utilized value. That is an 8x ROI .. 5
6.2 The Cost of Talent Drain
In the current talent market, developers and high-performing knowledge workers have options. They will not tolerate bad tooling. To make your technology a magnet for top talent, it's wise to empower your CTO as a value creator and transformation leader.
- The Metric: 1 in 5 employees have considered leaving their job due to poor change management and disruptive technology rollouts. 11
- The Cost: The cost to replace a mid-level employee is roughly 1.5x their salary. Losing your best Sales Rep because the new CRM is "unusable" is a six-figure loss.
6.3 Risk Mitigation
The history of IT is littered with companies that failed to manage the people side.
- Case Study: British Bank TSB: A rushed migration with insufficient testing and user preparation led to a meltdown where customers were locked out of accounts. The result was not just IT overtime; it was a massive fine from the Financial Conduct Authority (FCA) and a permanent stain on the brand. 16
- The Baytech Safety Net: Using Tailored Tech Advantage reduces this risk. By building software that fits the business, rather than forcing the business to fit the software, the "rejection risk" is minimized. The software feels like a natural extension of the user's hand, not a foreign object. For a case-specific look at the importance of strategic software consulting, visit our Essential Guide to Software Consultancy Services.
Part VII: Conclusion & The CIO’s Playbook
7.1 The New Definition of "Tech Leader"
The role of the CIO and VP of Engineering is evolving. It is no longer enough to be the Architect of Systems; you must be the Architect of Behavior. You are not just deploying code; you are deploying culture.
The failure of a technology project is rarely a failure of the technology itself. It is a failure of empathy. It is the result of brilliant engineers building perfect systems for imperfect humans, without consulting the humans first.
7.2 The Actionable Playbook
For the visionary leader ready to turn migration from a trauma into a triumph, here is the summary checklist:
- Map the Terrain: Don't just look at the API documentation. Look at the "Shadow Org Chart." Identify your Mavens, Connectors, and Resistors.
- Choose the Right Tool: Don't force a square peg into a round hole. Consider Tailored Tech Advantage to build software that respects your unique workflows. 2
- Engage Radically: Use Rapid Agile Deployment to bring users into the design process early. Make them co-creators. 2
- Communicate the "Why": Use the CEO for the vision and the Manager for the impact. Control the narrative.
- Enable in the Flow: Kill the PDF manual. Use Digital Adoption Platforms and Change Champions to support users in real-time.
- Measure and Iterate: Treat feedback as a system metric. Fix the friction points relentlessly.
7.3 Invitation to Engage
At Baytech Consulting, we understand that technology is only as powerful as the people who use it. We don't just build enterprise-grade software; we build adoption engines. Our Rapid Agile Deployment methodology ensures that your stakeholders are with you every step of the way, turning the "Valley of Despair" into a bridge to the future.
If you are facing a critical system migration and want to ensure that your investment yields real operational value, not just new shelfware, let’s talk. We can help you architect a solution that fits your business—and your people—perfectly.
Supporting Resources
- https://www.prosci.com/blog/the-costs-risks-of-poorly-managed-change
- https://www.mckinsey.com/capabilities/tech-and-ai/our-insights/superagency-in-the-workplace-empowering-people-to-unlock-ais-full-potential-at-work
- https://www.cio.com/article/191619/secrets-of-a-successful-cloud-erp-migration.html
About Baytech
At Baytech Consulting, we specialize in guiding businesses through this process, helping you build scalable, efficient, and high-performing software that evolves with your needs. Our MVP first approach helps our clients minimize upfront costs and maximize ROI. Ready to take the next step in your software development journey? Contact us today to learn how we can help you achieve your goals with a phased development approach.
About the Author

Bryan Reynolds is an accomplished technology executive with more than 25 years of experience leading innovation in the software industry. As the CEO and founder of Baytech Consulting, he has built a reputation for delivering custom software solutions that help businesses streamline operations, enhance customer experiences, and drive growth.
Bryan’s expertise spans custom software development, cloud infrastructure, artificial intelligence, and strategic business consulting, making him a trusted advisor and thought leader across a wide range of industries.


