
The Future of Software Investment: Risk Strategies for 2026
January 02, 2026 / Bryan Reynolds1. The High Stakes of Digital Evolution: Why Risk is the New Currency
In the corridors of modern enterprise, software has transcended its former role as a mere utility or back-office support function. In 2025, software is the central nervous system of business strategy, the primary engine of revenue generation, and the defining factor in competitive differentiation. For C-suite executives—whether you are a Visionary CTO architecting the future, a Strategic CFO guarding the balance sheet, or a Driven Head of Sales demanding tools to close deals—the decision to invest in software is indistinguishable from the decision to invest in the future viability of the company.
However, this landscape is fraught with peril. The digital frontier is not just a land of opportunity; it is a chaotic environment where billions of dollars are vaporized annually due to poor quality, misalignment, and catastrophic failure. The narrative of software development today is a tale of two divergent realities. On one side, we witness the transformative power of digital acceleration, where custom platforms and AI-driven integrations create unassailable competitive moats. On the other, we see a graveyard of failed initiatives—projects that burned through capital only to deliver brittle, unusable, or insecure systems.
To navigate this terrain, B2B executives must fundamentally reframe how they perceive risk. It is not about avoiding technology; it is about mastering the variables that govern success. Risk in software is not a monolith; it is a complex aggregate of financial volatility, technical debt, operational fragility, and market timing. This report serves as an exhaustive guide to dissecting these risks, moving beyond surface-level metrics of "on time and on budget" to explore the second and third-order consequences of technology decisions. We will explore the financial nuances of "Build vs. Buy," the operational hazards of Shadow IT, the legal intricacies of IP ownership, and the strategic necessity of modern infrastructure like Kubernetes and Hyperconverged Infrastructure (HCI).
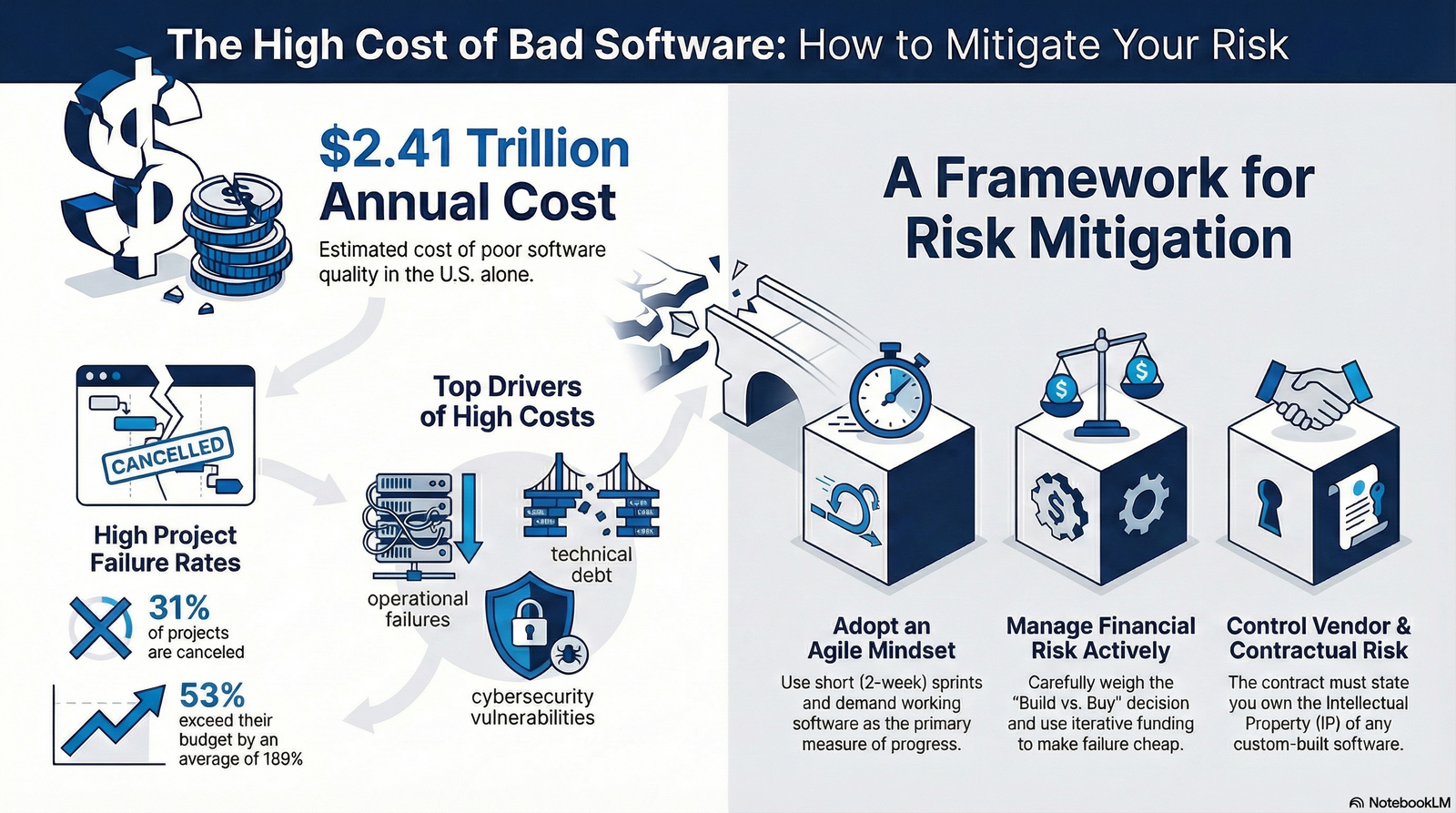
The $2.41 Trillion Wake-Up Call
The most sobering statistic in the current technology landscape comes from the Consortium for Information & Software Quality (CISQ). Their recent analysis estimates that the Cost of Poor Software Quality (CPSQ) in the United States alone has ballooned to an estimated $2.41 trillion annually. To put this figure into perspective, if "Bad Software" were a country, its GDP would rival that of Italy or Brazil.
This $2.41 trillion figure is not merely an abstract economic indicator; it represents a tangible drain on corporate resources. It comprises failed projects that are cancelled before delivery, the crushing weight of legacy system maintenance, the inefficiencies of technical debt, and the disastrous costs of cybercrime and operational outages.
When a project fails, the loss is not just the sunk cost of development; it is the opportunity cost of the market share that was not captured, the efficiency gains that were not realized, and the brand equity that was eroded.
The failure rates remain stubbornly high despite the proliferation of advanced project management tools. Industry reports indicate that 31.1% of software projects are canceled before they are ever completed. Furthermore, 52.7% of projects exceed their original budget by 189%, and only a meager 16.2% of projects are completed on time and within budget. These statistics reveal a systemic disconnect between executive ambition and engineering reality. The industry is facing a crisis of alignment, where the optimistic projections of the boardroom collide violently with the complex entropy of software engineering.
Table 1: The Components of Poor Software Quality Costs
| Cost Category | Description | Business Impact |
|---|---|---|
| Operational Failures | System outages, crashes, and downtime due to fragile code. | Direct revenue loss, customer churn, and severe brand damage (e.g., the CrowdStrike incident). |
| Technical Debt | The implied cost of future reworking required when choosing an easy solution now instead of a better approach. | Slower time-to-market for future features; exponentially higher maintenance costs over time. |
| Cybersecurity Vulnerabilities | Flaws in code structure that allow for data breaches and ransomware attacks. | Regulatory fines (GDPR/HIPAA), legal liability, ransom payments, and loss of intellectual property. |
| Legacy Maintenance | The cost of keeping outdated, inefficient systems alive. | Inhibits innovation; high cost of specialized labor to maintain obsolete tech stacks. |
| Failed Projects | Initiatives cancelled prior to deployment. | Total loss of invested capital; reduced morale; "change fatigue" among staff. |
The implication for the Ideal Reader—executives in industries ranging from finance and healthcare to logistics and high-tech—is clear: Risk management is the primary job of the software investor. You cannot simply write a check and hope for a return. You must actively manage the asset quality, the development process, and the underlying infrastructure.
The Blame Cycle vs. Systemic Risk
Why do these failures persist? Deep analysis suggests that software failure is rarely solely a "technology" problem. It is almost always an alignment problem. BCG research highlights that "lack of alignment" between business objectives and technology execution is a primary driver of failure.
Consider the typical "Blame Cycle." A driven Head of Sales demands a new feature to close a Q4 deal. The request is passed to the CTO, who warns that the timeline is unrealistic and will result in "spaghetti code." The CEO, focused on revenue growth, mandates the deadline. The engineering team complies, cutting corners on testing and documentation to meet the date. The feature launches but is buggy and unstable. The Sales team blames IT for the poor quality; IT blames Sales for the unrealistic requirements.
This cycle creates fragile code—software that works under "happy path" scenarios but breaks under stress. It also breeds a toxic culture where transparency is punished. This leads to the phenomenon of "Green-Shifting," where project status reports remain "Green" (on track) right up until the moment they go critical "Red," giving leadership zero time to intervene. The lack of honest reporting is a critical risk factor, often stemming from a fear of reporting bad news in a culture that does not understand the iterative nature of software development.
In the following sections, we will dismantle these risks piece by piece, providing a framework for turning software investment from a gamble into a calculated, high-yield business strategy.
2. The Psychology of Failure: Why Smart Executives Make Bad Software Decisions

To effectively manage risk, we must first understand the cognitive biases and psychological traps that lead intelligent leaders into disastrous software investments. The high failure rate of software projects is not just a matter of technical incompetence; it is often a failure of decision-making psychology.
The Optimism Bias and the Planning Fallacy
Software estimation is notoriously difficult. The "Cone of Uncertainty" describes how, at the beginning of a project, the variance in estimated effort can be as high as 400%. Yet, executives consistently fall victim to the Planning Fallacy—the tendency to underestimate the time, costs, and risks of future actions and at the same time overestimate the benefits of the same actions.
Engineers are inherently optimistic about their ability to solve problems. They estimate the time it takes to write the code (the "happy path") but often fail to account for the time required for integration, testing, bug fixing, and deployment. When a CTO presents a range of "6 to 9 months," the CEO often hears "6 months" and budgets accordingly. This sets the project up for failure before a single line of code is written.
The Sunk Cost Fallacy in Legacy Systems
One of the most dangerous psychological traps in B2B firms is the Sunk Cost Fallacy applied to legacy systems. An organization may have spent millions of dollars on a custom ERP system ten years ago. Today, that system is slow, insecure, and incompatible with modern mobile devices. However, because of the massive historical investment, leadership is terrified to replace it. They continue to pour money into "patching" the dying system, throwing good money after bad.
This is where the concept of Opportunity Risk becomes critical. By clinging to a legacy asset that consumes 80% of the IT budget just to "keep the lights on," the firm is unable to invest in innovation. They are effectively choosing the certainty of slow decline over the risk of transformation.
The "Green-Shifting" Phenomenon
As touched upon earlier, the culture of reporting in many organizations exacerbates risk. In a traditional "Waterfall" environment, where requirements are defined upfront and delivery happens months later, there is a long "dark period" where no working software is visible. During this time, project managers report status based on "tasks completed" rather than "value delivered."
Since no one wants to be the bearer of bad news, status reports are sanitized as they move up the chain of command. A developer might flag a major architectural flaw, but the middle manager suppresses it, hoping to fix it before anyone notices. By the time the report reaches the CFO, the project status is "Green." This illusion of progress masks the accumulation of risk until it is too late to pivot without massive cost.
Actionable Advice for Executives:
- Demand "Working Software" over "Status Reports": Adopt an Agile mindset where the primary measure of progress is working, tested software delivered every sprint (2 weeks). If you can't see the feature working, it isn't done.
- Normalize "Red" Status: Create a culture where flagging a risk or a delay is rewarded, not punished. Early detection of a delay allows for scope adjustment (Real Options) rather than a death march.
- Interrogate the Estimate: When presented with a timeline, ask for the confidence interval. "Is this a 50% confidence estimate or a 90% confidence estimate?" Force the uncertainty into the open.
3. The Financial Risk Framework: A CFO's Guide to Software Economics
For the Strategic CFO, software risk is ultimately financial risk. It is the danger of allocating capital to an asset that fails to generate a Return on Investment (ROI) or, worse, becomes a liability that drains cash flow. To manage this, CFOs must move beyond traditional CapEx budgeting models and embrace more dynamic financial frameworks.
The Build vs. Buy Financial Calculus
The decision to build custom software vs. buying an Off-the-Shelf (OTS) SaaS solution is the foundational financial risk decision. Each path carries a distinct financial risk profile that evolves over time.
The SaaS (Buy) Financial Profile
Financial Structure: Operational Expenditure (OpEx).
Risk: Uncapped Rent and Vendor Lock-In.
Buying SaaS is financially akin to renting. The upfront cost is low, making it attractive for short-term cash flow. However, the long-term cost curve is linear and perpetual.
- Vendor Pricing Power: Once your data and workflows are entrenched in a proprietary SaaS ecosystem, switching costs become prohibitively high. Vendors know this. The risk of price hikes is significant.
- Per-User Licensing: As your company grows, costs scale linearly. Adding 500 new sales reps means 500 new license fees immediately.
- The "Context" Trap: You are paying for features you don't use. Most SaaS platforms are "bloatware," packed with features to satisfy a broad market. You might only use 20% of the functionality but pay for 100% of the platform.
The Custom (Build) Financial Profile
Financial Structure: Capital Expenditure (CapEx).
Risk: Execution Variance and Maintenance.
Building custom software requires a significant upfront cash outlay ("the down payment"). However, once built, the marginal cost of adding a user is near zero.
- Asset Creation: Custom software is an owned asset. It can often be capitalized on the balance sheet, potentially offering tax advantages and improving EBITDA optics in the short term (check with your auditor).
- Equity Value: Proprietary software that creates a competitive advantage increases the enterprise value of the company. A logistics firm with a proprietary, AI-driven routing algorithm is worth more than a logistics firm that uses the same off-the-shelf software as its competitors.
- Maintenance: The hidden financial risk is maintenance. "You build it, you run it." You must budget for hosting, security patching, and server management.
Table 2: Comparative Risk Profile – SaaS vs. Custom Software
| Feature | Off-the-Shelf (SaaS) | Custom Software |
|---|---|---|
| Upfront Cost | Low (Subscription) | High (Development Capital) |
| Long-Term Cost | High (Perpetual License Fees) | Low (Maintenance & Hosting) |
| Time to Deployment | Immediate | Months (3–9 months avg.) |
| Customization | Limited / rigid | Unlimited / Tailored |
| Scalability | Vendor-dependent | Architected for specific growth |
| IP Ownership | Vendor owns IP | You own the IP |
| Primary Risk | Vendor Lock-in / Price Hikes | Project Delays / Scope Creep |
Real Options Theory: Mitigating the "Big Bet" Risk
In traditional finance, an "option" gives you the right, but not the obligation, to make a transaction in the future. In software, Real Options Theory provides a powerful framework for managing financial risk in uncertain environments.
In a Waterfall project, the CFO commits $1 million upfront for a 12-month project. This is a "Big Bet." If the market shifts in Month 6, the money is largely sunk.
In an Agile environment, the CFO can view the project as a series of "options."
- Sprint 1 (Cost: $50k): The team builds a prototype (MVP).
- Decision Point: Does the prototype show promise?
- Yes: Exercise the option to fund Sprint 2.
- No: Abandon the project. The loss is capped at 50k, saving the remaining 950k.
By funding software iteratively, the CFO transforms the investment from a rigid liability into a dynamic portfolio. This aligns perfectly with the agile philosophy of "failing fast." The goal is not to avoid failure, but to make failure cheap.
ROI and the "Total Cost of Ownership" (TCO)
Calculating ROI for software is notoriously difficult because the benefits are often intangible (e.g., "better user experience") or lagging indicators. To assess risk accurately, CFOs must look at Total Cost of Ownership (TCO) over a 5-to-7-year horizon.
- SaaS TCO: Subscription fees + Implementation costs + Training + Cost of "Workarounds" (inefficiencies caused by the software not fitting the process).
- Custom TCO: Development costs + Hosting fees + Maintenance retainer + Enhancements.
Often, the crossover point where Custom becomes cheaper than SaaS is around year 3 or 4. However, the value generated by Custom (revenue lift, efficiency) often accelerates past SaaS much earlier.
4. Technical Risk: The CTO’s Perspective on Architecture and Infrastructure
For the Visionary CTO, risk is less about dollars and cents and more about entropy. It is the risk that the system will become too complex to manage, too slow to scale, or too fragile to secure.
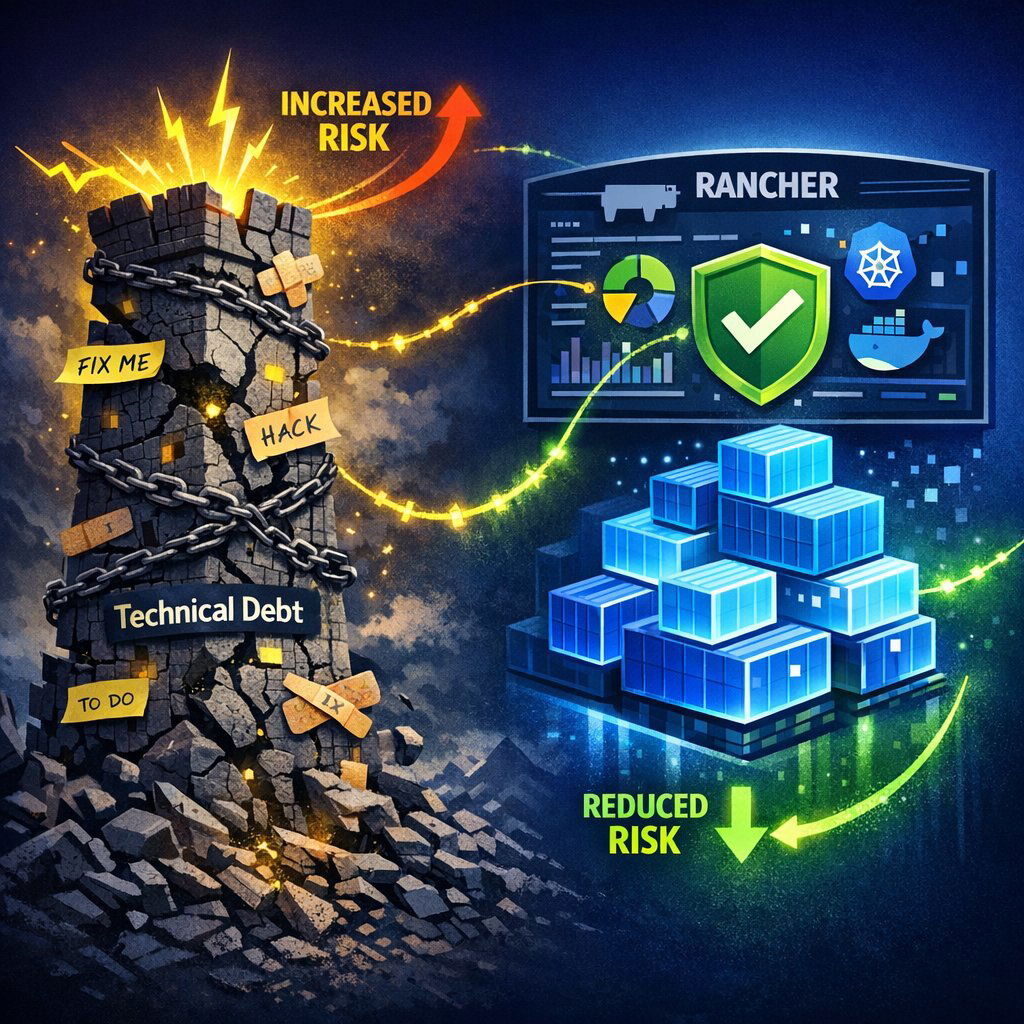
Technical Debt: The Interest on Bad Decisions
Technical Debt is a metaphor describing the implied cost of future reworking required when choosing an easy or limited solution now instead of a better approach that would take longer.
- Code Debt: Writing quick, messy code to meet a deadline.
- Architectural Debt: Building a monolithic application instead of a modular one.
- Documentation Debt: Failing to document how the system works.
Like financial debt, technical debt accumulates interest. As the codebase grows, the "interest" is paid in the form of slower development velocity. Engineers spend more time fixing bugs and deciphering old code than building new features. Eventually, a "Technically Bankrupt" system requires a complete rewrite—a massive risk event.
BCG and McKinsey emphasize that managing technical debt is a C-suite imperative. A CTO must negotiate a "debt pay-down" budget—allocating 15-20% of every sprint to refactoring and updating systems to keep the asset healthy.
Infrastructure Risk: The Ground Beneath Your Feet
The stability of your software depends entirely on the stability of the infrastructure it runs on. In 2025, the risk of "Hardware Lock-in" and "Cloud Complexity" is real.
The Shift to Containerization
Legacy applications often run on Virtual Machines (VMs). VMs are heavy, slow to boot, and carry a lot of overhead (a full OS for every app). Modern risk mitigation involves Containerization (using Docker).
- Consistency: Containers package the software with all its dependencies (libraries, settings). This guarantees that the software runs exactly the same on a developer's laptop as it does on the production server, eliminating the classic "it works on my machine" risk.
- Resilience: Containers are ephemeral. If one crashes, it can be destroyed and replaced in milliseconds.
Kubernetes (K8s) and the Management Challenge
Kubernetes is the industry standard for orchestrating containers. It handles auto-scaling, self-healing, and load balancing. However, Kubernetes is notoriously complex. A misconfigured cluster can be a security nightmare.
This is where Rancher becomes a critical risk management tool. Rancher is an enterprise management platform for Kubernetes.
- Risk Mitigation: Rancher provides a "single pane of glass" to manage multiple clusters. It centralizes security policies (RBAC), ensuring that an engineer can't accidentally open a security hole in production. It simplifies upgrades and provides observability, reducing the risk of human error.
Harvester HCI: Breaking the VMware Grip
For organizations that run on-premise or hybrid clouds, the cost and complexity of virtualization (like VMware) is a significant risk. Broadcom's acquisition of VMware has led to uncertainty and price hikes for many enterprises.
Harvester HCI (Hyperconverged Infrastructure) offers a modern, open-source alternative.
- Unified Architecture: Harvester is built on Kubernetes. It allows you to run legacy VMs side-by-side with modern containers. This provides a bridge to the future without requiring a "rip and replace" of legacy systems.
- Cost Reduction: Being open-source, Harvester significantly lowers the Total Cost of Ownership (TCO) compared to proprietary stacks, freeing up budget for innovation.
- Disaster Recovery: Harvester simplifies storage and replication, making it easier to implement robust Disaster Recovery (DR) plans.
Integration Risk: The "Data Silo" Problem
Many software projects fail not because the software itself is bad, but because it cannot talk to the rest of the ecosystem.
- Legacy ERPs: Connecting a modern React frontend to a 30-year-old AS/400 system is a high-risk activity.
- API Dependency: Relying on third-party APIs introduces "Counterparty Risk." If the API provider goes down (like the CrowdStrike incident affecting millions), your application fails.
- Mitigation: Building "Anti-Corruption Layers" in your architecture to insulate your core system from the quirks of legacy systems or third-party APIs.
5. Operational & Security Risk: The Fortress Mindset

In the interconnected digital economy, security is not a feature; it is a foundational requirement. The threat landscape has evolved from isolated hackers to industrialized cybercrime syndicates and state-sponsored actors.
The Threat Landscape: From Ransomware to Supply Chain Attacks
The CrowdStrike incident in July 2024 was a watershed moment. A faulty update from a trusted security vendor crashed 8.5 million Windows devices globally, grounding flights and halting surgeries. This highlighted the fragility of the Software Supply Chain. You are not just reliant on your own code; you are reliant on every library and tool your vendors use.
Key Cyber Risks:
- Ransomware 2.0: Attackers don't just encrypt data; they steal it and threaten to release it (Double Extortion).
- Low-Code Vulnerabilities: A misconfiguration in Microsoft Power Apps exposed 38 million records. This proves that "easy to build" often means "easy to breach."
- Shadow IT: 65% of companies report data loss risks associated with Shadow IT—employees using unsanctioned apps to do their work.
Shadow IT: The Enemy Within
Shadow IT occurs when business units (Marketing, HR) bypass IT to buy or build their own solutions because IT is "too slow."
- The Risk: These apps often lack security controls, backups, and compliance oversight. Sensitive customer data ends up in a "zombie app" that no one is monitoring.
- The Solution: You cannot ban Shadow IT; you must compete with it. By providing "Rapid Agile Deployment," IT can offer a sanctioned, secure alternative that is just as fast as the shadow solution.
DevSecOps: Shifting Security Left
To manage security risk, modern custom software development employs DevSecOps. This philosophy integrates security into every phase of the development lifecycle, rather than treating it as an audit at the end.
- Automated Scanning: Tools like Azure DevOps and GitHub Advanced Security automatically scan code for known vulnerabilities (in dependencies) and hard-coded secrets (passwords/keys) every time a developer commits code.
- Static Application Security Testing (SAST): Analyzes source code for logic flaws.
- Dynamic Application Security Testing (DAST): Attacks the running application to find weaknesses.
- Identity Management: Using robust identity providers (like Azure Entra ID) and enforcing Multi-Factor Authentication (MFA) is the single most effective way to prevent unauthorized access.
Business Continuity and Disaster Recovery (BCDR)
What is your Recovery Time Objective (RTO)? If your data center floods, how long until you are back online?
- High Availability (HA): Using clustered infrastructure (like Harvester) ensures that if one server fails, the workloads automatically migrate to another without downtime.
- Immutable Backups: To protect against ransomware, backups must be "immutable" (read-only), so that even an admin cannot delete them. This is your last line of defense.
6. Vendor Risk Management: Choosing the Right Partner

When you engage a custom software partner (like Baytech Consulting), you are managing Vendor Risk. You are outsourcing a critical business function to a third party. The selection process must be rigorous.
The Financial Stability of the Partner
A vendor that goes bankrupt in the middle of a project is a catastrophe. You are left with half-finished code and no one who understands it.
- Due Diligence: Ask for evidence of financial health. Ask about their year-over-year growth and debt levels.
- Talent Depth: Does the vendor rely on a few "rockstar" developers? If they leave, does the project stall? You want a partner with a deep bench of talent and standardized processes, so the project is not dependent on any single individual.
Contractual Risk: The Red Flags
The Master Services Agreement (MSA) is your primary risk management tool.
- Intellectual Property (IP) Ownership: This is the most critical clause. The contract must explicitly state that you (the Client) own the code and all related IP upon payment. "Work made for hire" language is essential. Beware of vendors who try to retain ownership and only grant you a "license" to use the software. This destroys the asset value of your investment.
- Indemnification: The vendor should indemnify you if their code infringes on a third party's IP.
- Warranty: A standard warranty should cover bug fixes for a set period (e.g., 90 days) after launch at no cost. You should not pay to fix defects that should not have existed.
- Termination Clauses: Ensure you have a clear "Termination for Convenience" clause. If the project isn't working out, you need a parachute.
Source Code Escrow
For mission-critical applications, especially when dealing with smaller vendors, demand a Source Code Escrow agreement.
- Mechanism: The vendor deposits the source code, documentation, and build instructions with a neutral third-party escrow agent on a regular basis (e.g., monthly).
- Release Condition: If the vendor goes bankrupt, fails to support the software, or breaches the contract, the escrow agent releases the source code to you.
- Benefit: This ensures business continuity. You can take the code and hire a new team to maintain it.
The Fixed-Bid vs. Time & Materials Debate
CFOs often prefer Fixed Bid contracts because they offer price certainty. However, in software, Fixed Bid contracts often increase risk.
- The Adversarial Trap: Fixed Bid creates an adversarial relationship. The vendor is incentivized to do the least amount of work possible to meet the requirements. Every change becomes a fight over "scope."
- The Agile Alternative: A Time and Materials (T&M) model, often with a "Not to Exceed" cap, aligns incentives. The team works to deliver the highest value features first. If the budget runs out, you have a working product with the most important features, rather than a half-finished product that aimed for everything and delivered nothing.
7. The Agile Antidote: Methodology as Risk Control
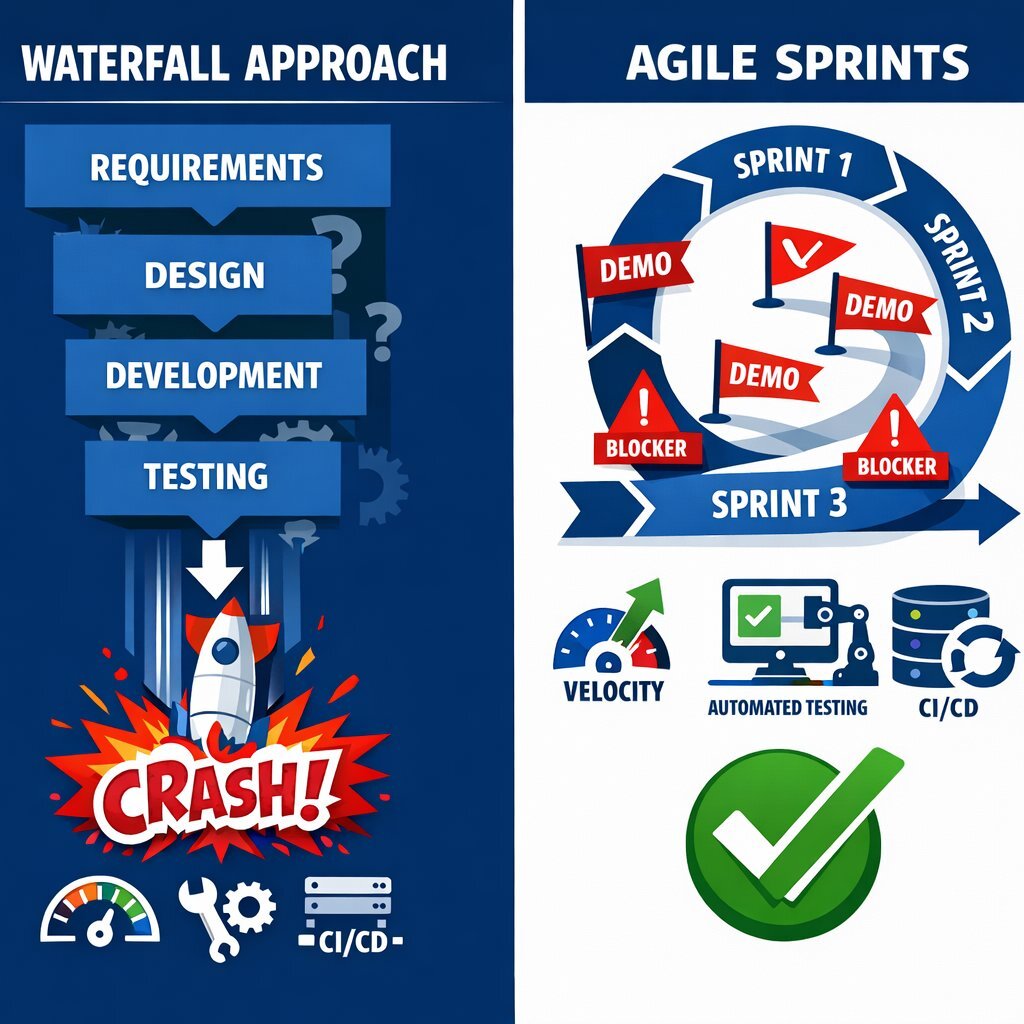
How do we take all these risks—financial, technical, operational—and manage them effectively? The industry consensus, supported by decades of data, points to Agile Methodology as the superior risk management framework.
Why Waterfall Increases Risk
Traditional "Waterfall" management hides risk until the end. You spend millions over 12 months on design and coding, and only at the very end (User Acceptance Testing) do you see if it works. This is a "Big Bang" deployment. If the market has changed, or the requirements were misunderstood, the failure is total.
How Agile Reduces Risk
Agile is built on transparency and feedback loops.
- Short Sprints: Work is broken into 2-week cycles. At the end of every sprint, there is a demo of working software. You cannot hide a failing project in Agile. If the team delivers nothing in Sprint 1, you know immediately.
- Velocity Tracking: Agile measures "velocity"—how many points of work the team completes per sprint. This provides a data-driven forecast for completion. If velocity drops, it is an early warning signal of technical debt or blockers.
- Prioritization: Agile forces you to prioritize by business value. You build the "Must Haves" first. If the project runs out of budget, the essential features are already live and generating value.
DevOps and Automated Quality
Agile manages process risk; DevOps manages deployment risk.
- Continuous Integration/Continuous Deployment (CI/CD): By automating the build and deployment process, you remove human error.
- Automated Testing: Every time a developer saves code, a suite of thousands of automated tests runs to ensure they haven't broken existing functionality. This creates a "safety net" that allows teams to move fast without breaking things.
8. Sector-Specific Risk Profiles: Case Studies in Success and Failure
Different industries face unique risk profiles. Understanding these nuances is key to a tailored strategy.
8.1 Healthcare: Patient Safety and Compliance
Risk: HIPAA compliance, patient data privacy, and the literal life-and-death consequences of system failure.
Case Study: Henry County Hospital & MEDITECH
- Context: A rural hospital needing to modernize its Electronic Health Record (EHR) system to improve physician efficiency and patient care.
- Strategy: They chose a cloud-based "MEDITECH as a Service" (MaaS) model. This shifted the infrastructure risk to the vendor (Google Cloud/MEDITECH) who has world-class security.
- Risk Management: They focused heavily on Change Management. They understood that the biggest risk was not the software, but the doctors refusing to use it. By involving physicians in the selection and design process, they achieved high buy-in.
- Outcome: Physician satisfaction scores in the 95th percentile and a seamless transition that improved care coordination.
8.2 Logistics: Operational Uptime and Efficiency
Risk: Thin margins mean that efficiency is everything. Downtime halts the physical movement of goods.
Case Study: Goodaymart Logistics
- Context: A logistics provider struggling with manual processes and lack of visibility in the supply chain.
- Strategy: Digital transformation using a custom platform integrating IoT and AI for real-time tracking.
- Risk Mitigation: They avoided the trap of buying a generic Transportation Management System (TMS) that wouldn't fit their unique model. They built a "scenario-based" solution.
- Outcome: Full-process intelligent management, reduced operational costs, and the ability to scale rapidly. The custom software became a competitive asset that generic competitors could not replicate.
8.3 Fintech: Regulatory and Transaction Risk
Risk: Handling money requires zero-tolerance for error. Regulatory compliance (SEC, banking laws) is paramount.
Case Study: Swoop & Sage Partnership
- Context: Helping SMEs access funding through embedded finance.
- Strategy: Integration. Rather than building a bank from scratch, Swoop integrated with Sage’s accounting software.
- Risk Mitigation: Leveraging existing trusted platforms (Sage) reduced the trust barrier for customers.
- Outcome: Seamless access to loans and grants for business owners, creating a new revenue stream for both partners without the massive CapEx of building new banking infrastructure.
9. Conclusion: The Portfolio Approach to Software
Thinking about risk in software investments requires a paradigm shift. You must stop viewing software projects as "construction projects" (where you pay a fee and get a building) and start viewing them as financial portfolios.
- Diversify your risk: Mix low-risk SaaS for non-critical functions (payroll, email) with high-reward Custom Software for core differentiators (customer portal, proprietary analytics).
- Demand Ownership: For custom investments, ensure you own the IP. It is an asset on your balance sheet that builds enterprise value.
- Embrace Agility: Use Agile not just for speed, but for risk control. Buying "options" to pivot saves money and prevents the Sunk Cost Fallacy.
- Harden the Infrastructure: Invest in modern, resilient platforms like Harvester and Rancher to ensure your asset remains available, secure, and cost-effective.
- Vet Your Partners: Your software vendor is your co-pilot. Audit their financials, their security practices, and their contracts.
At Baytech Consulting, we do not just write code; we manage investment risk. Our "Tailored Tech Advantage" ensures that the solution fits your specific business context, avoiding the "square peg in a round hole" risk of off-the-shelf software. Our "Rapid Agile Deployment" methodology is designed specifically to mitigate the execution risks outlined in this report—providing transparency, adaptability, and frequent value delivery.
Investing in software is investing in risk. But with the right partner, the right process, and the right mindset, it is the best investment a modern business can make.
Frequently Asked Question
Q: "How do I ensure I own the Intellectual Property (IP) of my custom software?"
Answer:
Ensuring IP ownership is the single most critical legal step in a custom software project. If you are paying for the development, you must own the resulting asset. If you do not own the code, you cannot capitalize it, you cannot value it for an acquisition, and you may be legally prevented from modifying it or taking it to a new vendor in the future.
To ensure you are protected, you must adhere to the following checklist:
- "Work Made for Hire" Clause: Your Master Services Agreement (MSA) must explicitly state that all deliverables are "Works Made for Hire" under U.S. copyright law. It should further state that if for any reason they do not qualify as such, the vendor irrevocably assigns all rights, title, and interest in the software to the Client immediately upon creation or payment.
- Avoid "Licensing" Language for Custom Work: Be extremely wary of contracts that grant you a "perpetual, non-exclusive license" to the custom code. This implies the vendor still owns it and could legally resell the feature you paid for to your direct competitor.
- Source Code Delivery: Ownership is theoretical without possession. Ensure the contract requires the vendor to deliver the actual source code (not just the compiled executable) to a repository you control (e.g., your own GitHub, Azure DevOps, or GitLab account) on a regular basis (e.g., at the end of every Sprint). Do not wait until the end of the project.
- Distinguish Background vs. Foreground IP: It is standard for vendors to leverage their own pre-existing libraries (Background IP) to speed up development (e.g., a standard login module). The contract should distinguish between "Background Technology" (vendor-owned, licensed to you perpetually and royalty-free) and "Foreground Technology" (custom-built for you, owned by you).
- Escrow for Safety: For added protection, particularly with smaller vendors, consider a Source Code Escrow agreement. This ensures that if the vendor goes out of business, a third party releases the code to you.
At Baytech Consulting, we believe that if you pay for it, you own it. Our standard contracts are designed with client ownership in mind, because we want to retain clients through the quality of our work, not through legal handcuffs.
Three Key Resources for Further Reading
- https://www.baytechconsulting.com/blog/custom-vs-off-the-shelf
- https://www.pmi.org/learning/library/going-agile-how-reduce-risk-failure-9531
- https://www.it-cisq.org/the-cost-of-poor-quality-software-in-the-us-a-2022-report
About Baytech
At Baytech Consulting, we specialize in guiding businesses through this process, helping you build scalable, efficient, and high-performing software that evolves with your needs. Our MVP first approach helps our clients minimize upfront costs and maximize ROI. Ready to take the next step in your software development journey? Contact us today to learn how we can help you achieve your goals with a phased development approach.
About the Author

Bryan Reynolds is an accomplished technology executive with more than 25 years of experience leading innovation in the software industry. As the CEO and founder of Baytech Consulting, he has built a reputation for delivering custom software solutions that help businesses streamline operations, enhance customer experiences, and drive growth.
Bryan’s expertise spans custom software development, cloud infrastructure, artificial intelligence, and strategic business consulting, making him a trusted advisor and thought leader across a wide range of industries.


