Third-Party & Supply Chain Risk: A New C-Suite Imperative
October 17, 2025 / Bryan Reynolds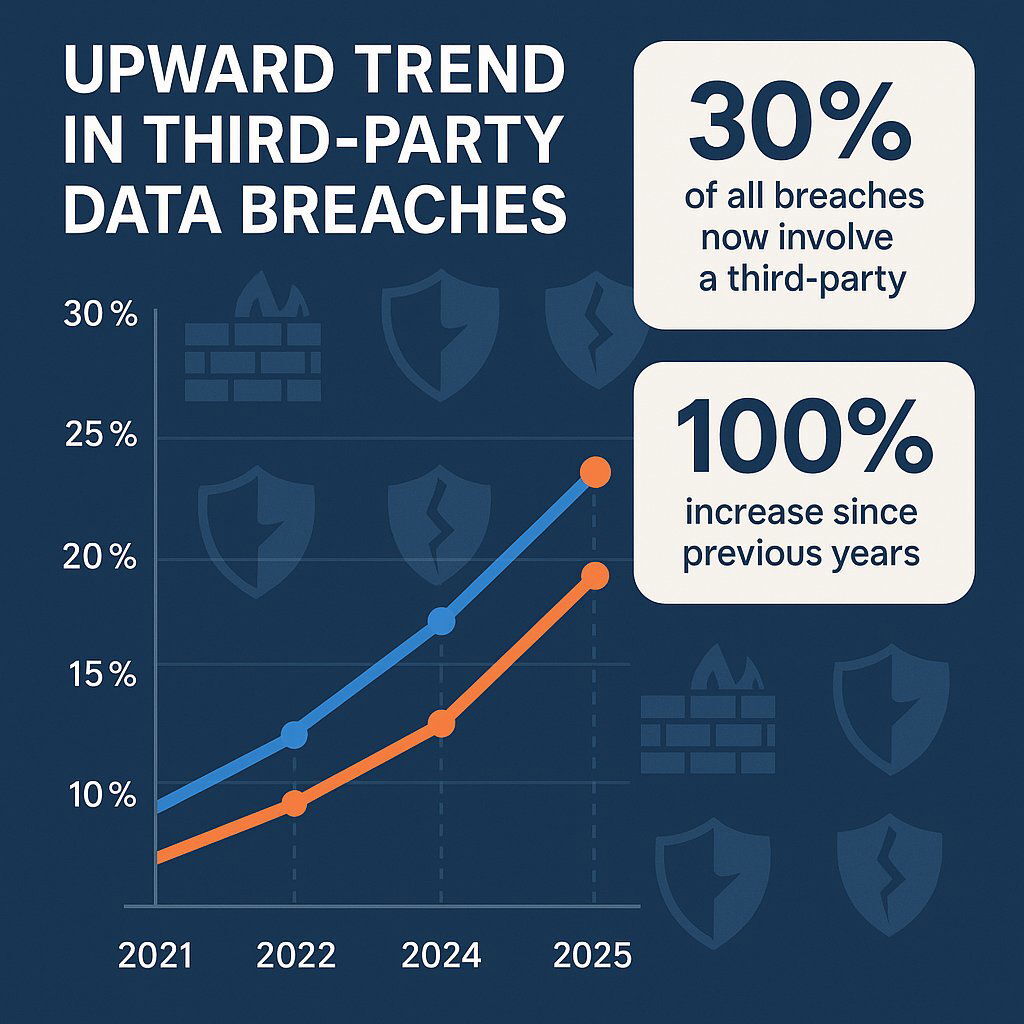
Beyond the Firewall: Managing Third-Party and Supply Chain Risk in a Digital World
The Perimeter Has Vanished
The traditional model of enterprise security, built around the concept of a defensible digital perimeter, is obsolete. For decades, organizations invested in stronger firewalls and more sophisticated intrusion detection systems, operating under the assumption that the greatest threats lay outside their walls. That assumption has been shattered. The 2025 Verizon Data Breach Investigations Report (DBIR) reveals a startling new reality: 30% of all data breaches now involve a third-party, a staggering 100% increase from previous reports. The modern enterprise is not a fortress; it is a sprawling, interconnected ecosystem. Your digital supply chain—the intricate web of vendors, partners, open-source code, and cloud services that powers your operations—is now your most vulnerable and expansive attack surface.
Managing this distributed risk is no longer a task that can be delegated solely to the IT department. It has become a core strategic imperative for the entire C-suite, demanding a new level of collaboration between technology, finance, and operations. The threats are too costly, the operational disruptions too severe, and the regulatory stakes too high for a siloed approach. This new battlefield requires a unified strategy, one that recognizes the systemic nature of supply chain risk and embeds resilience into the very fabric of the organization. This article will provide a C-suite-level briefing on the current threat landscape, outline a cross-functional mandate for managing third-party risk, present a modern framework for assessment and mitigation, and explore how a secure-by-design approach to technology can transform this critical vulnerability into a competitive advantage.
The New Battlefield: Your Supply Chain is Your Biggest Blind Spot
The shift in focus from direct assaults to supply chain infiltration is not a random evolution; it is a calculated strategy by sophisticated threat actors. They have recognized that targeting a single, often less-secure, vendor can provide a trusted pathway into the networks of hundreds or even thousands of their clients. This inversion of the attack surface—where the greatest risk now originates from within the trusted supply chain—fundamentally changes the nature of cybersecurity from perimeter defense to ecosystem-wide risk management. The financial and operational consequences of this new reality are staggering and accelerating.
The Exploding Financial and Operational Costs
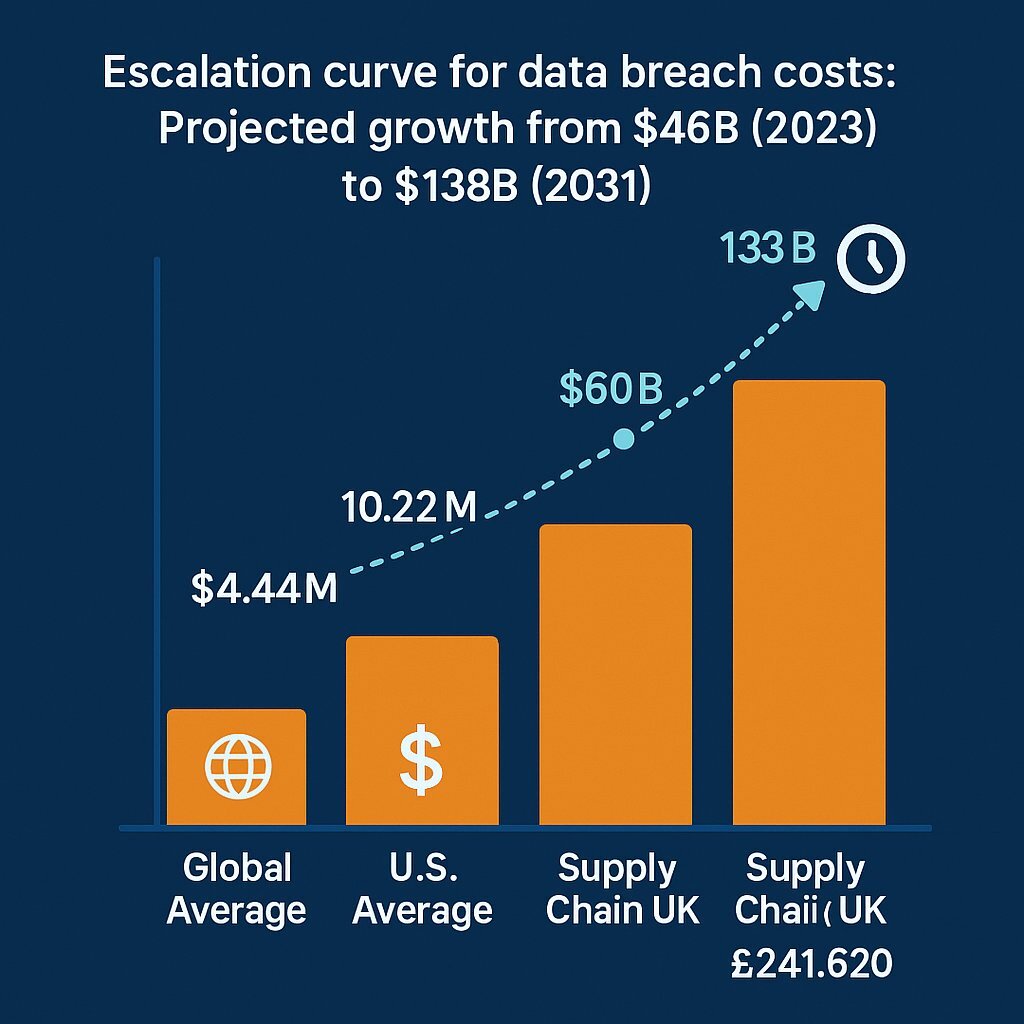
The financial stakes of a third-party breach are immense. According to the IBM Cost of a Data Breach Report 2025, the global average cost of a data breach has reached $4.44 million, a figure that skyrockets to a record $10.22 million in the United States. However, these figures mask a more alarming trend: the "supply chain cost premium." Breaches originating from a supply chain compromise are uniquely damaging. They not only cost more on average—adding an estimated £241,620 to the final bill in the UK, for example—but they also take significantly longer to resolve. The average time to identify and contain a supply chain breach is 267 days, a full week longer than malicious insider attacks, with every additional day compounding the financial and reputational damage.
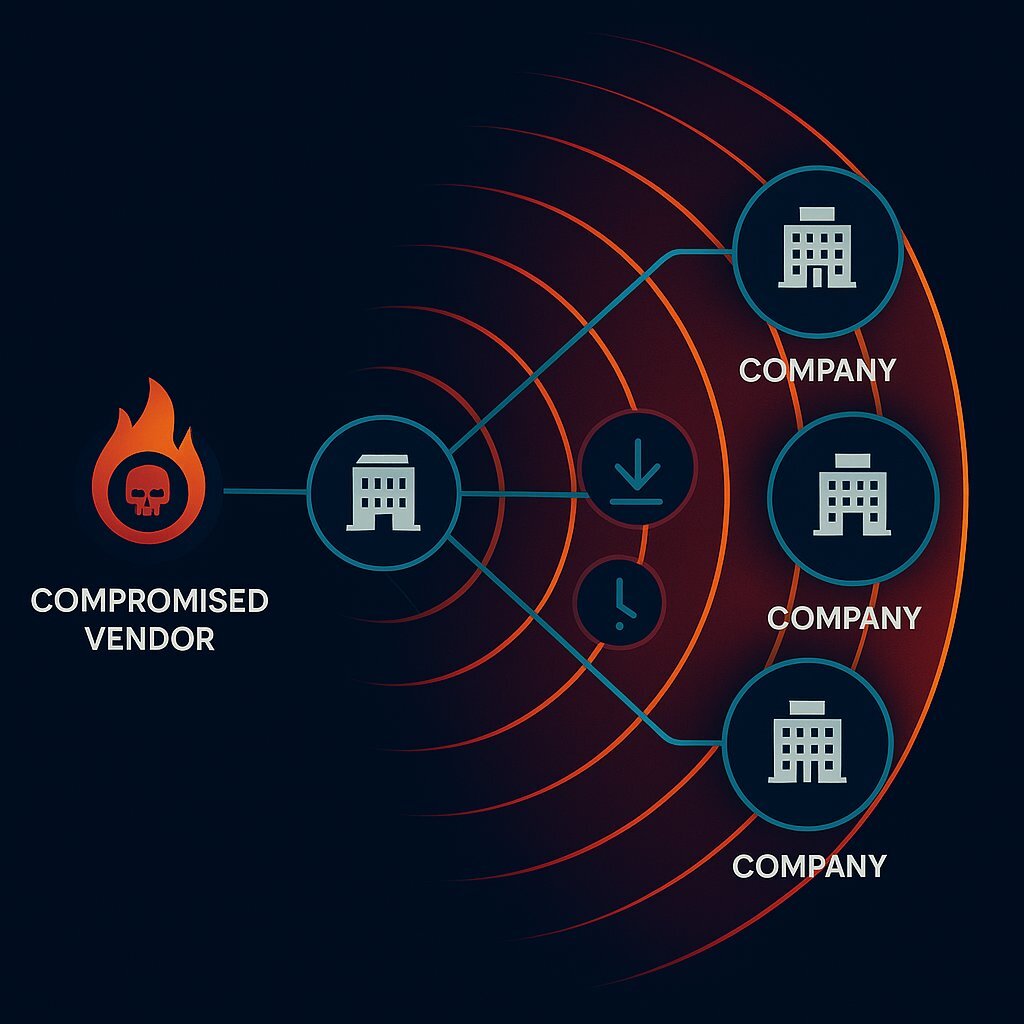
This is not a temporary spike but a rapidly escalating crisis. Cybersecurity Ventures forecasts that the global annual cost of software supply chain attacks will climb from $46 billion in 2023 to $60 billion in 2025, reaching an almost unfathomable $138 billion by 2031. This exponential growth underscores the urgency for leadership to move beyond reactive measures and implement proactive, strategic risk management.
The problem's pervasiveness means no organization is immune. A 2024 survey by BlackBerry revealed that more than 75% of organizations have experienced a software supply chain attack within the last year. This near-universal threat is fueled by the very foundation of modern software development: open-source components. The 2024 State of the Software Supply Chain report by Sonatype logged over 512,847 malicious packages in the past year alone, a 156% year-over-year increase. In parallel, a 2024 report from ReversingLabs found that malicious threats in open-source repositories grew by an astonishing 1,300% between 2020 and 2023. These are not vulnerabilities in obscure libraries; they are malicious payloads deliberately injected into the building blocks of the digital economy, waiting to be integrated into corporate applications. To see how a single phishing attack can shatter the open-source supply chain, review our deep-dive on the npm JavaScript ecosystem compromise and its business ramifications.
This risk is further amplified by trends within the enterprise itself. The rise of "Bring Your Own AI" (BYOAI), with 78% of AI users bringing their own unsanctioned tools to work, creates a massive, unmanaged extension of the third-party risk problem. Each time an employee feeds sensitive corporate data into an unauthorized generative AI platform, they are establishing a new, unvetted third-party relationship, bypassing all formal procurement and security reviews. This "shadow supply chain" has a direct financial impact; IBM reports that breaches involving shadow AI add an average of $670,000 to the total cost of an incident. Coupled with the fact that one in three data breaches involves "shadow data" stored outside of IT's control, it becomes clear that the official vendor inventory represents only a fraction of the true attack surface.
Ransomware: The Supply Chain's Apex Predator
Nowhere is the danger of supply chain compromise more evident than in the propagation of ransomware. These attacks, which average $5.08 million in recovery costs, have evolved from simple encryption-for-payment schemes into multi-faceted extortion campaigns that leverage the interconnectedness of modern business. Attackers no longer need to breach a target organization directly; they can simply hold a critical supplier hostage and let the disruption cascade downstream.
Recent real-world incidents provide a stark illustration of this tactic:
- United Natural Foods Inc. (UNFI) and Whole Foods: In June 2025, a ransomware attack on UNFI, the primary grocery supplier for Whole Foods, caused severe disruptions to deliveries across North America. The direct consequence for Whole Foods was empty shelves, frustrated customers, and a publicly stated negative impact on their quarterly income. This case perfectly demonstrates the tangible link between a vendor's cybersecurity failure and a client's operational and financial health.
- Asefa and FC Barcelona: In another June 2025 incident, a ransomware group breached Asefa, a Madrid-based insurer, and exfiltrated over 200GB of sensitive data. This data included confidential information about high-profile clients, including the football club FC Barcelona, leading to significant negative headlines and reputational damage for a brand far removed from the initial breach.
These examples highlight a critical shift: your organization's resilience is no longer solely dependent on your own security posture. It is inextricably linked to the security posture of the weakest link in your entire digital supply chain.
| Metric | Global Figure | U.S. Figure | Key Insight |
|---|---|---|---|
| Average Cost of a Data Breach | $4.44 Million | $10.22 Million | The U.S. is the most expensive region for breaches. |
| Average Cost of a Ransomware Incident | $5.08 Million | N/A | Ransomware carries a significant cost premium over typical breaches. |
| Average Time to Contain a Supply Chain Breach | 267 Days | 267 Days | 7 days longer than other malicious attacks, driving up costs. |
| Projected Annual Cost of Supply Chain Attacks (2025) | $60 Billion | N/A | The financial impact of this threat is growing at an exponential rate. |
The C-Suite's Triple Mandate: Aligning Security, Finance, and Operations
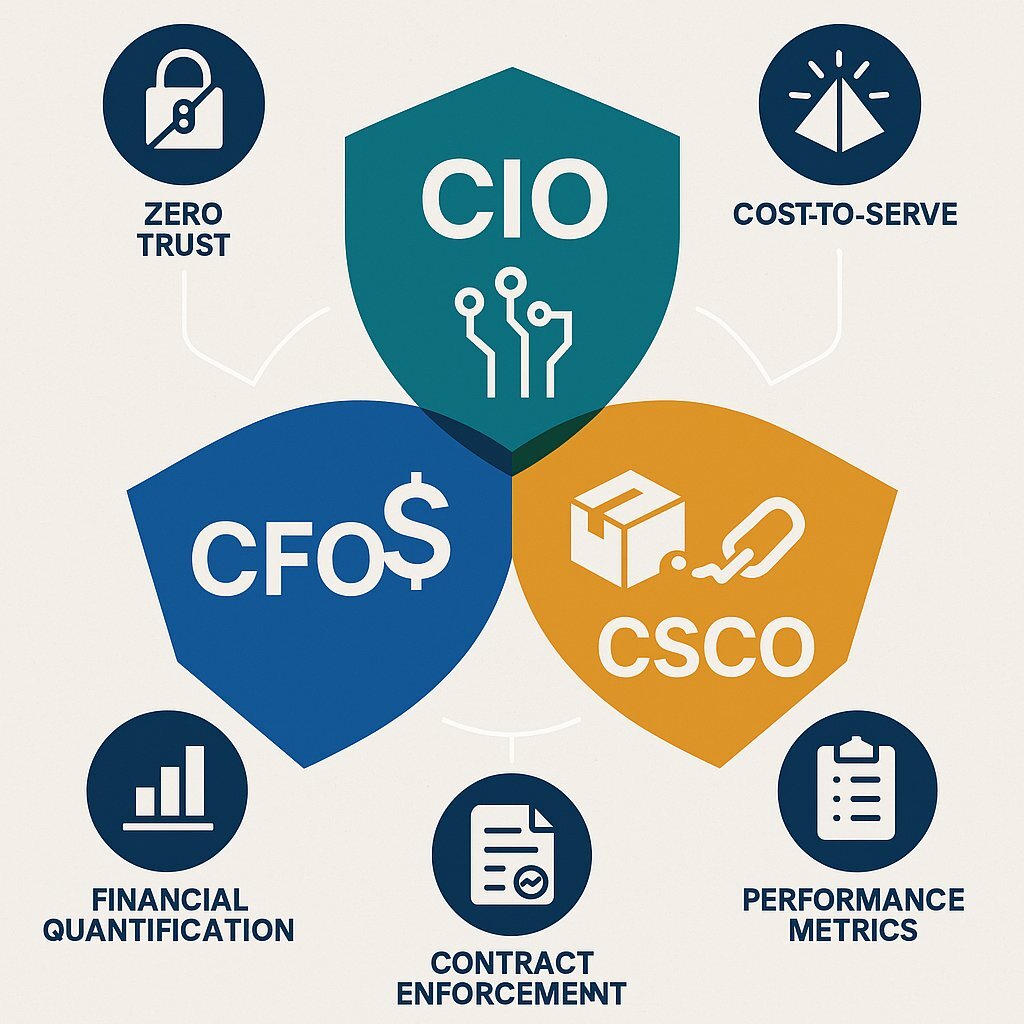
The systemic nature of supply chain risk necessitates a fundamental shift in organizational responsibility. Managing this threat can no longer be a siloed function; it requires a unified strategy championed by a "C-Suite Triad" of the Chief Information Officer, Chief Financial Officer, and Chief Supply Chain Officer. Each executive brings a critical perspective and set of responsibilities to the table. Their active, formalized collaboration is the only way to embed resilience into the culture and processes of the modern enterprise. This interdependency is not just a best practice; it is increasingly a regulatory and financial necessity.
For the CIO: From Technologist to Strategic Risk Advisor
The CIO's role has evolved far beyond managing internal IT infrastructure. In an ecosystem-driven world, the CIO is the architect of enterprise-wide digital resilience. This means establishing robust governance frameworks, such as COBIT or ITIL, that can manage a distributed and dynamic technology landscape. It is the CIO's mandate to lead the technical due diligence of all vendors, moving beyond the demonstrably inadequate model of static questionnaires. With only 4% of organizations expressing high confidence in the accuracy of vendor questionnaires, the CIO must champion more rigorous, evidence-based assessment methods.
A key strategic action for the CIO is the implementation of a zero-trust architecture—a security model that assumes no user or system is inherently trustworthy, whether internal or external. This is a critical defense when any part of the supply chain could be compromised. Furthermore, the CIO must oversee the strategic deployment of security AI and automation, which the data shows can accelerate the identification and containment of breaches by nearly 100 days, drastically reducing the impact of an incident.
For the CFO: From Cost Center to Value Protection
The CFO's primary mandate to safeguard the organization's financial health now directly encompasses cybersecurity. This responsibility has been formalized by new SEC disclosure rules, which require public companies to report on their cybersecurity risk management, strategy, and governance in their annual reports. This makes the CFO directly accountable for accurately representing the company's cyber risk posture, including that of its third parties.
To fulfill this mandate, the CFO must collaborate closely with the CISO and CIO to quantify third-party risk in financial terms. This involves prioritizing the protection of "crown jewel" assets, such as payment systems and platforms related to internal control over financial reporting (ICFR), and conducting rigorous cost-benefit analyses of security investments. An effective incident response plan, for instance, can reduce breach costs by as much as 61%. The CFO must also scrutinize vendor contracts for clear liability clauses and ensure cyber insurance policies adequately cover third-party incidents, which are involved in 40% of all breach claims. This shift requires the CFO to treat Third-Party Risk Management (TPRM) not as a compliance checkbox, but as a core pillar of enterprise risk management.
For the CSCO: From Procurement to Partnership Resilience
The Chief Supply Chain Officer's traditional focus on cost optimization and just-in-time delivery must now be balanced with a new imperative: resilience. The CSCO is on the front line of managing the physical and digital flow of goods and services, and their role is central to mitigating supply chain risk. This begins with developing a comprehensive map of the entire supply chain, identifying not only direct (third-party) suppliers but also their critical dependencies (fourth-party vendors).
Cybersecurity posture must become a formal, weighted criterion in the vendor selection, vetting, and procurement process. The CSCO must work in lockstep with the CIO and CISO to develop standardized risk assessment questionnaires and define minimum security requirements for partners. These requirements must then be embedded into procurement processes and enforced through legally binding contracts. These contracts should explicitly incorporate Cyber Supply Chain Risk Management (C-SCRM) policies, including the right to audit vendor security controls and mandatory timelines for incident notification. In an era of constant disruption, fostering deep, collaborative partnerships focused on mutual security and resilience is a more sustainable strategy than a purely transactional, cost-driven approach. To avoid scope creep and protect operational integrity, especially in software-driven supply chains, alignment on deliverables and risk criteria is essential.
| Role | Primary Concern | Key Questions to Ask | Strategic Actions |
|---|---|---|---|
| CIO | Technological Resilience & Governance | Are our security frameworks (e.g., NIST, ISO) adequate for a distributed ecosystem? How can we gain real-time visibility into vendor security posture beyond static questionnaires? | Champion a zero-trust architecture. Implement security automation and AI for faster threat detection. Lead technical due diligence and continuous monitoring. |
| CFO | Financial Exposure & Regulatory Compliance | What is the potential financial impact (in dollars) of a breach at our most critical vendors? Are we compliant with new SEC disclosure rules? What is the ROI on our TPRM investments? | Quantify third-party risk in financial terms. Integrate cyber risk into financial reporting (ICFR). Scrutinize vendor contracts for liability and insurance coverage. |
| CSCO | Operational Continuity & Supplier Integrity | Have we mapped our critical digital dependencies, including fourth-party vendors? Is cybersecurity a formal criterion in our procurement and sourcing process? Do our vendor contracts enforce our security standards? | Integrate C-SCRM into the entire procurement lifecycle. Classify vendors by criticality to business operations. Foster collaborative security initiatives with key partners. |
From Reactive to Resilient: A Modern Framework for Third-Party Risk Management
To effectively manage the complexities of the modern supply chain, organizations must move beyond ad-hoc, compliance-driven activities and adopt a structured, lifecycle-based framework for Third-Party Risk Management (TPRM). A mature TPRM program is not a one-time project but a continuous, dynamic process that adapts to the evolving threat landscape and the changing nature of vendor relationships. This framework, aligned with best practices from standards bodies like NIST and ISO, can be broken down into four distinct stages that cover the entire vendor lifecycle.
Stage 1: Identification & Classification
An organization cannot manage risks it is not aware of. The foundational step of any TPRM program is to create and maintain a comprehensive, centralized inventory of all third-party vendors. This process must be exhaustive, capturing everything from major software providers to smaller, specialized service firms that may have access to sensitive data or systems.
Once the inventory is established, the next critical action is to implement a risk-based classification system. Not all vendors pose the same level of risk. A tiered approach allows the organization to focus its most intensive due diligence and monitoring efforts on the relationships that matter most. Vendors should be categorized based on factors such as their criticality to core business operations, the volume and sensitivity of the data they access (e.g., customer PII, intellectual property), and their level of integration with internal networks. This prioritization ensures that resources are allocated efficiently and proportionally to the level of risk.
Stage 2: Assessment & Due Diligence
This stage involves a deep and thorough evaluation of a vendor's security posture before they are onboarded. This process must be rigorous and evidence-based, moving beyond the flawed model of self-attested questionnaires. A modern due diligence process incorporates multiple layers of validation:
- Alignment with Foundational Frameworks: The assessment methodology should be grounded in established, defensible industry standards. Frameworks like the NIST Cybersecurity Framework (CSF) 2.0, NIST SP 800-161 for supply chain specifics, and ISO 27001 provide a comprehensive set of controls that form a robust basis for evaluation.
- Evidence-Based Verification: Rather than simply accepting a vendor's claims, organizations must demand verifiable proof of their security controls. The most valuable form of evidence is a SOC 2 Type II report. This independent audit evaluates the operational effectiveness of a vendor's controls over an extended period (typically 6-12 months) against key criteria including Security, Availability, Processing Integrity, Confidentiality, and Privacy. Reviewing this report provides a much more reliable picture of a vendor's actual security practices.
- External Posture Assessment: To complement the vendor's internal documentation, organizations should leverage tools that provide an objective, "outside-in" view of their security posture. Security rating services and automated attack surface scanning tools can continuously monitor a vendor's public-facing assets for misconfigurations, vulnerabilities, and other indicators of risk, providing real-time intelligence that can instantly flag critical issues. This continuous verification model is essential to close the "confidence gap" left by point-in-time assessments.
Stage 3: Contracting & Onboarding
The insights and requirements identified during the due diligence phase must be translated into legally binding contractual obligations. The contract is one of the most powerful tools for mitigating third-party risk, as it formally defines security expectations and allocates liability. All vendor agreements, especially for high-risk partners, must include specific and non-negotiable security clauses. Key provisions include:
- Right to Audit: A clause granting the organization the right to audit the vendor's security controls and practices, or to review the results of independent third-party audits.
- Data Breach Notification: A strict, unambiguous requirement for the vendor to report any suspected security incident or data breach within a defined, short timeframe (e.g., 24-48 hours).
- Data Jurisdiction and Protection: Clauses that specify the geographic locations where data can be stored and processed, and mandate specific security measures such as encryption for data both at rest and in transit.
- Supply Chain Transparency: For critical software vendors, the contract should require the provision of a Software Bill of Materials (SBOM), which inventories all open-source and third-party components within their product. This provides crucial visibility into potential fourth-party risks.
- Liability and Insurance: Clear language defining the vendor's liability in the event of a breach originating from their environment and requiring them to maintain a minimum level of cybersecurity insurance coverage.
Stage 4: Continuous Monitoring & Secure Offboarding
A vendor's risk profile is not static; it changes continuously. A partner who is secure today could be compromised tomorrow by a zero-day vulnerability or an internal error. Therefore, risk management cannot end after the contract is signed. A mature TPRM program includes a robust continuous monitoring strategy. This involves ongoing tracking of the vendor's external security rating, monitoring public threat intelligence feeds for mentions of the vendor, and conducting periodic reassessments. The frequency and depth of these reviews should be dictated by the vendor's risk tier, with high-risk vendors subject to annual or even quarterly deep-dives.
Finally, the vendor lifecycle concludes with offboarding, a frequently overlooked but critical step. When a relationship ends, a formal, documented offboarding process must be executed to ensure that all vendor access to corporate systems, data, and facilities is immediately and completely revoked. This process should also confirm that all company data has been securely returned or destroyed in accordance with contractual terms, preventing the risk of "ghost access" from dormant accounts that could be exploited long after the partnership has ended. Learn more about outsourcing best practices and IP protection strategies that can accelerate secure offboarding and minimize third-party risk.
Building a Defensible Digital Core: The Role of Custom, Secure-by-Design Solutions
While a robust TPRM framework is essential for managing the risks associated with the broad ecosystem of vendors, for an organization's most critical, core business functions, a more fundamental question must be asked: Is reliance on any third-party software an acceptable risk? For processes that handle the most sensitive data, define a core competitive advantage, or represent a single point of operational failure, the most effective mitigation strategy is to take direct control. Investing in custom, secure-by-design software solutions transforms a potential liability into a defensible digital core.
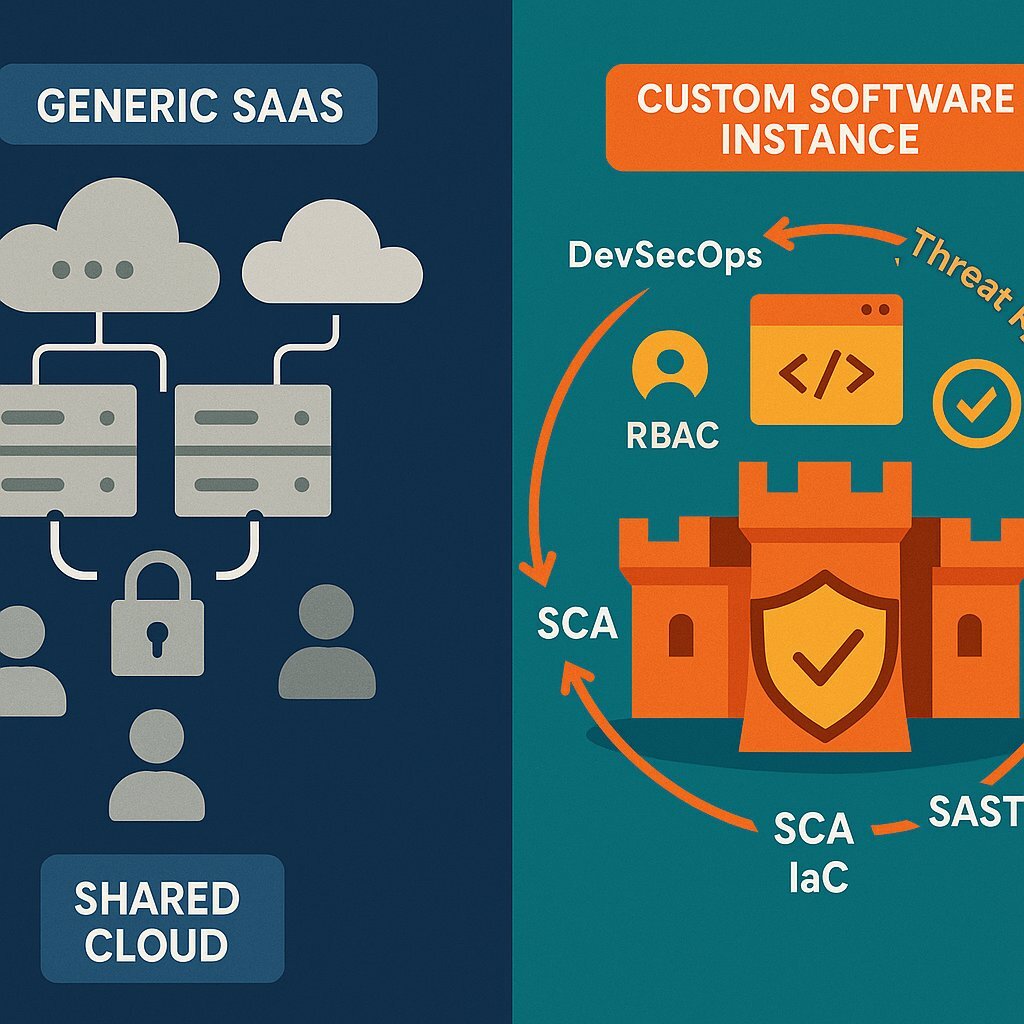
The Inherent Security Gaps of Off-the-Shelf Software
Off-the-shelf Software-as-a-Service (SaaS) platforms offer convenience and rapid deployment, but this comes at the cost of significant, often hidden, security compromises. Recent data shows that SaaS-related breaches have surged by over 300% in the last year, indicating that attackers are actively targeting the systemic weaknesses of these platforms. These weaknesses are inherent to their business model:
- Shared Infrastructure: Most SaaS platforms operate on multi-tenant environments, meaning an organization's sensitive data is stored on the same servers as data from countless other companies. While segregated, a single vulnerability or misconfiguration in the underlying infrastructure can create a catastrophic blast radius, exposing multiple clients simultaneously.
- Generic Controls: SaaS solutions are built for a mass market, offering standardized, one-size-fits-all security controls. Their predefined user roles and access permissions often cannot be tailored to an organization's unique operational workflows, increasing the risk of over-privileged users and internal threats.
- Opaque Risk and Dependency: When an organization adopts a SaaS platform, it is not just trusting that one vendor. It is implicitly trusting the vendor's employees, their security practices, and their entire fourth-party supply chain. The organization is ultimately dependent on the vendor's patching schedule, leaving critical systems exposed to known vulnerabilities until the vendor decides to act.
If your industry faces complex regulatory requirements or you demand robust control over your application's architecture, see how custom software provides a competitive edge over generic SaaS. The flexibility and security dividends can profoundly impact resilience and long-term value.
The Strategic Advantages of a Custom, Secure-by-Design Approach
Custom software development, particularly when executed by a partner with a security-first mindset, offers a fundamentally more secure alternative. Instead of treating security as a feature to be bolted on, it is embedded into the foundation of the solution.
This approach begins with DevSecOps , a methodology that integrates security practices into every phase of the software development lifecycle (SDLC). This "shift-left" philosophy ensures that security is not an afterthought but a continuous consideration:
- Secure Design: Before any code is written, a process of threat modeling is conducted to identify potential attack vectors and design mitigating controls into the application's architecture. This proactive analysis helps to build a system that is inherently resilient to anticipated threats.
- Secure Coding and Dependencies: Throughout the development process, automated tools are integrated directly into the Continuous Integration/Continuous Deployment (CI/CD) pipeline. Static Application Security Testing (SAST) tools scan proprietary code for vulnerabilities as it is written. Simultaneously, Software Composition Analysis (SCA) tools, like GitHub Advanced Security's dependency scanning, analyze all open-source libraries for known vulnerabilities, directly addressing the massive risk from the open-source ecosystem. Any secrets or credentials accidentally committed to the code repository are also automatically detected and flagged.
- Secure Deployment and Operations: Security extends to the infrastructure on which the application runs. Using Infrastructure-as-Code (IaC) , secure configurations for cloud environments and services like Kubernetes can be defined, version-controlled, and consistently deployed, preventing manual configuration errors. This includes implementing best practices such as using hardened, minimal container images, enforcing strict Role-Based Access Control (RBAC) within the cluster, and using network policies to isolate workloads and limit the potential for lateral movement by an attacker.
This secure-by-design methodology is a key enabler of a true zero-trust security posture. By building transparent, controllable systems with granular access controls and verifiable security at every layer, an organization can drastically reduce its reliance on the implicit trust required by third-party black boxes. A custom application, designed from the ground up on zero-trust principles, transforms a core business system from a potential attack vector into a hardened, defensible asset.
| Security Dimension | Off-the-Shelf SaaS Solution | Baytech Custom Solution (Secure-by-Design) |
|---|---|---|
| Hosting Environment | Multi-tenant, shared infrastructure. A single breach can affect multiple customers. | Dedicated private cloud or on-premise. Eliminates "noisy neighbor" risk and provides perimeter control. |
| Access Control | Generic, predefined roles. Difficult to tailor to unique business workflows. | Granular, role-based access control (RBAC) designed specifically for your operational needs and the principle of least privilege. |
| Compliance | Broad, generic certifications (e.g., ISO 27001). May not meet specific industry needs (e.g., HIPAA, PCI-DSS). | Compliance-by-design. Built from the ground up to meet your specific regulatory requirements from day one. |
| Vulnerability Management | Dependent on vendor's patching schedule. Known vulnerabilities can remain exposed for extended periods. | Proactive and continuous. DevSecOps pipeline scans for vulnerabilities in code and dependencies in real-time, enabling rapid remediation. |
| Data Ownership & Control | Vendor controls data location, encryption, and access. You are a tenant in their system. | Full ownership and sovereignty. You control where data resides, how it is encrypted, and who can access it. |
Conclusion: Turning Risk into a Competitive Advantage
The digital supply chain is the new reality of modern business, and with it comes a new paradigm of risk. The evidence is unequivocal: the frequency, sophistication, and cost of third-party breaches are increasing at an alarming rate, making supply chain security the most pressing cybersecurity challenge for today's leadership. The traditional, perimeter-focused security model is no longer sufficient. Resilience in this interconnected era demands a strategic, cross-functional commitment from the entire C-suite. The CIO, CFO, and CSCO must forge a unified front, integrating technology, finance, and operations into a cohesive risk management strategy.

This strategy must be built on a modern, lifecycle-based framework that moves beyond outdated, compliance-driven checkbox exercises. It requires a shift toward continuous, evidence-based verification of vendor security, the codification of security requirements into ironclad contracts, and an understanding that risk management is an ongoing, dynamic process. If you're scaling your applications and looking to handle third-party risks for one million or more users, don't miss our guidance on scalable architecture for hyper-growth scenarios.
For the most critical aspects of the business, however, mitigation is not enough. The ultimate strategy for resilience is control. By investing in custom, secure-by-design software solutions, organizations can reclaim ownership of their digital core. A DevSecOps approach, which embeds security into every stage of the development lifecycle, transforms core applications from potential liabilities into hardened, defensible assets.
Ultimately, proactive and comprehensive supply chain risk management is not a cost center; it is a powerful source of competitive advantage. In an era defined by digital disruption and systemic risk, the organizations that can demonstrably protect customer data, ensure operational continuity, and build resilient digital foundations will be the ones that win customer trust, attract investment, and dominate their markets. The challenge for the C-suite is to move beyond a reactive, compliance-focused mindset and to champion the strategic investments needed to build the secure, resilient, and custom-tailored digital core required to thrive in this new reality. For critical systems maintenance and lifecycle management, see our executive guide to post-launch software success for additional strategies.
Supporting Resources & Further Reading
- NIST SP 800-161, Rev. 1: Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations
- This publication from the National Institute of Standards and Technology provides the foundational U.S. government framework for establishing a comprehensive C-SCRM program.
- The 2025 Verizon Data Breach Investigations Report (DBIR)
- An essential annual report that provides deep, data-driven analysis of the global threat landscape, including detailed statistics on the prevalence and nature of third-party breaches.
- PwC's 2025 Global Digital Trust Insights
- This report offers a C-suite perspective on cybersecurity priorities, highlighting the growing concern around third-party risk and the need to align cyber investments with business strategy.
About Baytech
At Baytech Consulting, we specialize in guiding businesses through this process, helping you build scalable, efficient, and high-performing software that evolves with your needs. Our MVP first approach helps our clients minimize upfront costs and maximize ROI. Ready to take the next step in your software development journey? Contact us today to learn how we can help you achieve your goals with a phased development approach.
About the Author

Bryan Reynolds is an accomplished technology executive with more than 25 years of experience leading innovation in the software industry. As the CEO and founder of Baytech Consulting, he has built a reputation for delivering custom software solutions that help businesses streamline operations, enhance customer experiences, and drive growth.
Bryan’s expertise spans custom software development, cloud infrastructure, artificial intelligence, and strategic business consulting, making him a trusted advisor and thought leader across a wide range of industries.


