
DevSecOps Blueprint: How to Make Your DevOps Lifecycle Your Strongest Security Asset
October 14, 2025 / Bryan ReynoldsSecure by Design: Why Your DevOps Lifecycle Is Your Most Critical Security Asset

In the relentless drive to innovate, engineering leaders face a constant, high-stakes balancing act. The business demands speed—faster feature releases, quicker iterations, and a shorter time-to-market. Simultaneously, the security landscape has become a minefield of hyper-sophisticated, automated threats. The central question is no longer simply "How do we integrate security into our DevOps process?" but rather, "How do we transform our entire development lifecycle into our most formidable security control?" The answer lies in a fundamental paradigm shift: treating the Software Development Lifecycle (SDLC) not as a process to be secured, but as the new security perimeter itself. Security can no longer be a final checkpoint; it must be the foundation upon which every line of code is built.
The New Battlefield: Yesterday's Security Can't Defend Against Tomorrow's AI-Powered Threats
The urgency to rethink application security is driven by a stark reality: the nature of cyber threats has fundamentally and irrevocably changed. Traditional security models, built like fortresses to repel external attacks, are being systematically dismantled by adversaries who operate with the efficiency of modern tech startups and the backing of powerful new tools.
The Velocity and Volume of Modern Threats
The contemporary threat landscape is defined by its speed, scale, and sophistication. Adversaries are no longer lone actors but "enterprising" organizations that leverage automation and AI to industrialize their attacks. This has led to a tactical evolution where brute force is replaced by surgical precision, and the targets have shifted from the network edge to the heart of the development process itself.
Recent analysis reveals a startling trend: a staggering 79% of cyberattack detections are now "malware-free". Instead of trying to breach a firewall with a malicious payload, attackers are exploiting legitimate tools, stolen credentials, and social engineering to gain access. This makes legacy endpoint protection and signature-based defenses increasingly ineffective. The adversary is already "inside" the trusted environment.
Generative AI has become the adversary's "new best friend," acting as a force multiplier for these malware-free attacks. AI is now routinely used to:
- Supercharge Social Engineering: Crafting highly personalized and grammatically perfect phishing emails at a massive scale, making them nearly indistinguishable from legitimate communications.
- Automate Credential Theft: AI-powered tools can crack 51% of common passwords in under one minute, rendering weak password policies obsolete.
- Create Hyper-Realistic Deepfakes: The latter half of 2024 saw a 442% surge in vishing (voice phishing) attacks, where AI is used to clone voices for fraudulent purposes.
This technological shift means that even novice attackers can now orchestrate sophisticated campaigns that were once the exclusive domain of well-funded nation-state actors. The barrier to entry for high-impact cybercrime has effectively been eliminated.
Security as a Bottleneck: The Traditional Model is Broken
For decades, security was treated as a final quality assurance (QA) gate—a tollbooth that development teams had to pass through just before release. This model is fundamentally incompatible with the speed and iterative nature of modern DevOps and Agile. When security is an afterthought, it inevitably becomes a bottleneck, creating an adversarial relationship between developers who are incentivized for speed and security teams who are tasked with managing risk.
This friction is not just anecdotal. A 2025 survey found that 71% of Chief Information Security Officers (CISOs) report that business stakeholders still perceive security as a major impediment to faster market deployment. This perception creates immense pressure on development teams, leading to dangerous compromises. In fact, nearly half of organizations admit to consciously and knowingly deploying vulnerable code simply to meet deadlines. This is the direct, predictable outcome of a broken model: when speed and security are positioned as opposing forces, speed often wins the battle, but the business ultimately loses the war.
The Exponential Cost of Waiting
The business case for integrating security early is not just about risk reduction; it is a clear-cut financial imperative. Delaying security validation until the later stages of the SDLC introduces an exponential increase in the cost of remediation. This principle, often called the "Rule of Ten," demonstrates that the cost to fix a bug or vulnerability increases by an order of magnitude at each successive phase of development.
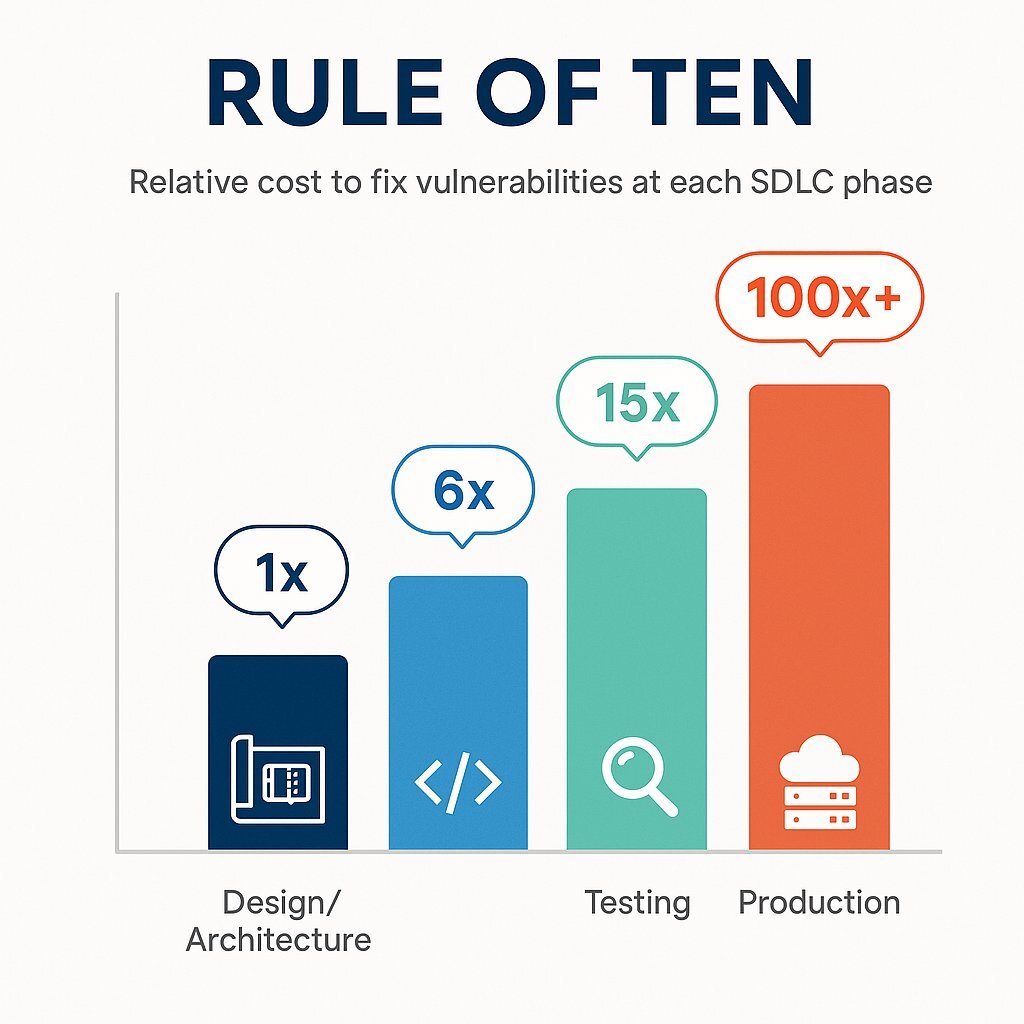
| SDLC Stage | Relative Cost to Fix a Vulnerability |
|---|---|
| Design / Architecture | 1 x |
| Implementation (Coding) | 6 x |
| System / Integration Testing | 15 x |
| Post-Release (Production) | 100 x + |
| Source: Adapted from data by the Systems Sciences Institute at IBM and the National Institute of Standards and Technology (NIST). |
The implications are profound. A security issue that might cost $100 in developer time to fix during the coding phase could cost $1,500 during system testing and a staggering $10,000 or more after release, not including the potential for reputational damage, customer churn, and regulatory fines. Waiting to address security is not a strategy; it is an accumulation of technical and financial debt that will eventually come due.
Shifting Left: The DevSecOps Philosophy for Building Resilient Software
Addressing the failures of the traditional model requires more than new tools; it demands a new philosophy. DevSecOps represents this fundamental shift, evolving from a buzzword into a strategic imperative for any organization building software. It is a cultural, practical, and technological transformation that redefines how security is implemented throughout the entire value stream. If you want more depth on how high-performing teams thrive in this environment, our article Software Maintenance Mastery: Executive Guide to Post-Launch Success offers fresh insight on keeping security and performance in lockstep after launch.
From Gatekeeper to Partner: Redefining Security's Role
At its heart, DevSecOps is a cultural movement designed to break down the organizational silos that have historically separated Development, Security, and Operations teams. The core objective is to transform security from an isolated function into a

shared responsibility that is owned by everyone involved in the software lifecycle.
In this model, the role of the security team undergoes a profound evolution. They are no longer the gatekeepers who appear at the end of the process to audit code and deliver a list of findings. Instead, they become strategic partners and enablers. Their new mission is to empower developers by providing them with the training, tools, and automated guardrails necessary to build securely from the very beginning. This collaborative approach is essential for achieving both speed and safety. At Baytech Consulting, this principle is embedded in our Rapid Agile Deployment model, where our highly skilled engineers work in tight, collaborative loops, ensuring that security considerations are an intrinsic part of every sprint, not a hurdle at the finish line.
The Three Pillars of Modern DevSecOps
The DevSecOps philosophy is built upon three interconnected pillars that, when implemented together, create a powerful framework for building resilient and secure applications.
Secure by Design (SbD): This is the foundational principle, asserting that security cannot be bolted on as an afterthought; it must be an integral part of the application's architecture from the initial concept. SbD involves proactive practices such as
Threat Modeling , where teams brainstorm potential attack vectors during the design phase, long before any code is written. It also champions the Principle of Least Privilege (PoLP) , ensuring that every component and user only has the absolute minimum permissions necessary to function. A key tenet of SbD is establishing
secure default configurations , which makes the most secure option the easiest and most natural choice for developers, thereby reducing the risk of human error.
- Shift Left: If Secure by Design is the "what," then Shifting Left is the "how." This principle refers to the practical act of moving security testing, scanning, and validation activities as far to the left—or as early as possible—in the SDLC timeline. Instead of discovering a critical vulnerability during a pre-production penetration test a week before launch, the Shift Left approach aims to find that same vulnerability on the developer's local machine via an IDE plugin, or automatically flag it in the very first pull request. This ensures that feedback is delivered when it is most relevant and least costly to address. Explore the risks of excessive configuration and how modern DevOps streamlines security without sacrificing flexibility.
- Automate Everything: Automation is the engine that allows DevSecOps to function at the speed and scale of modern software development. Manual security reviews are slow, inconsistent, and simply cannot keep pace with CI/CD pipelines that may deploy code multiple times a day. By automating security checks and embedding them directly into the CI/CD workflow, security becomes a continuous and consistent process that provides real-time feedback without slowing developers down. Automation is what makes security an integral part of the delivery pipeline, rather than an impediment to it.
The Blueprint for Integration: Weaving Security into Your Azure DevOps Pipeline
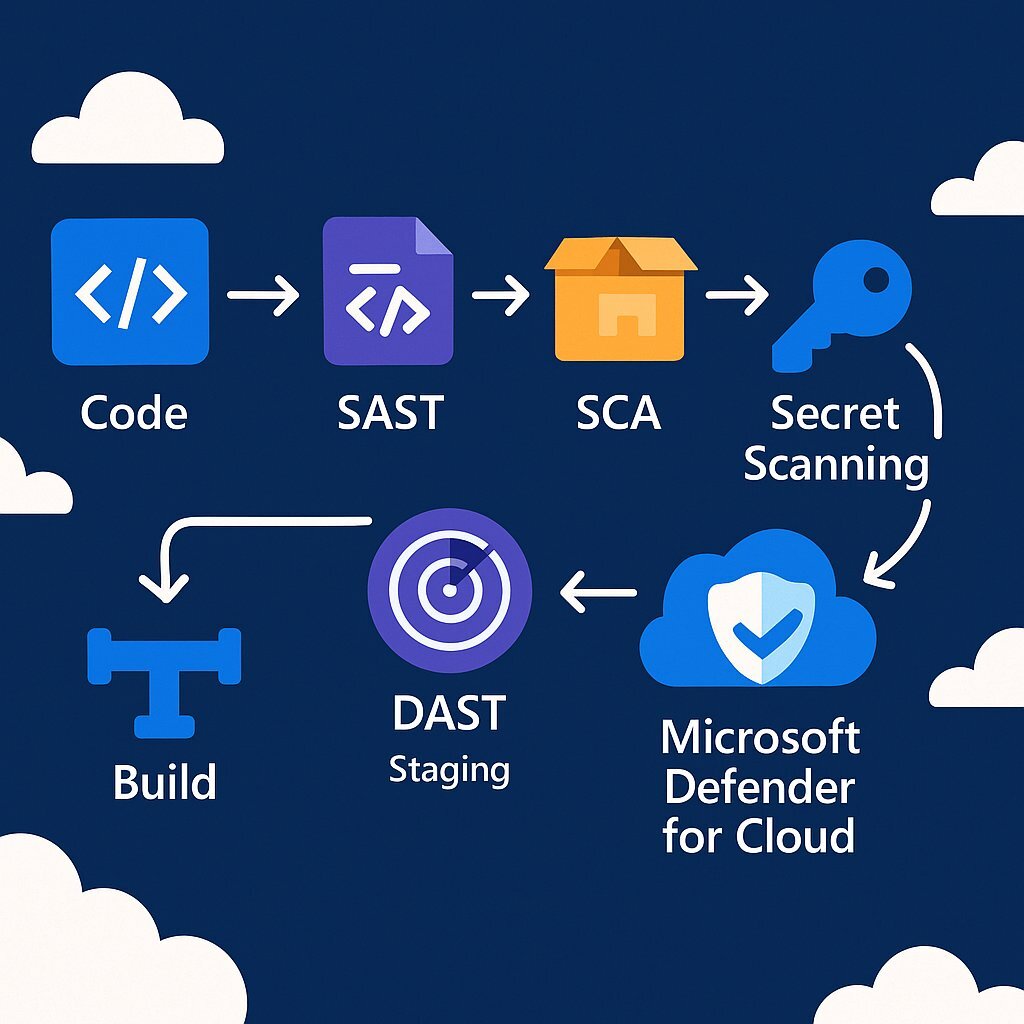
Adopting a DevSecOps philosophy requires a practical plan for integrating automated security tools into the daily workflow of developers. The goal is to create a series of automated checks and balances within the CI/CD pipeline that provide fast, actionable feedback. For organizations invested in the Microsoft ecosystem, the combination of Azure DevOps and GitHub Advanced Security offers a tightly integrated, powerful toolchain to bring this vision to life. If your focus is on DevOps efficiency and seamless integration, building the right pipeline is essential.
Your DevSecOps Toolchain: A Practical Overview
A comprehensive DevSecOps pipeline automates several distinct types of security testing, each designed to identify different kinds of vulnerabilities at various stages of the lifecycle. The primary categories include Static Application Security Testing (SAST), Software Composition Analysis (SCA), Dynamic Application Security Testing (DAST), and Secret Scanning. The following blueprint provides a step-by-step guide to integrating these capabilities into an Azure DevOps environment.
Step 1: Static Application Security Testing (SAST) – Your First Line of Defense
- What it is: SAST is a "white-box" testing methodology. It directly analyzes an application's source code, bytecode, or binary for security vulnerabilities without executing the program. Think of it as an automated, security-focused code reviewer that scans for known insecure patterns, such as those that could lead to SQL injection, buffer overflows, or cross-site scripting (XSS), as defined by standards like the OWASP Top 10.
- Why it matters: SAST provides the earliest possible feedback loop in the development process. By identifying potential flaws before the code is even merged into the main branch, it allows developers to remediate issues while the context is still fresh in their minds and the cost to fix is at its absolute lowest.
- Practical Integration: GitHub Advanced Security for Azure DevOps includes a powerful SAST engine called CodeQL. To integrate it:
- Enable the Feature: First, an administrator must enable GitHub Advanced Security for the specific Azure DevOps organization, project, or repository. This is a straightforward process within the organization or project settings.
- Configure the Pipeline: Next, modify the
azure-pipelines.ymlfile to include the CodeQL analysis tasks. The pipeline should include theAdvancedSecurity-Codeql-Inittask before the build step, followed by the custom build steps, and finally theAdvancedSecurity-Codeql-Analyzetask to complete the scan. - Review the Results: Once configured, scan results will automatically appear in the "Advanced Security" tab within Azure Repos. Crucially, findings are also posted as annotations directly on pull requests, providing developers with immediate, in-context feedback on the specific lines of code that introduced a potential vulnerability.
Step 2: Software Composition Analysis (SCA) – Securing Your Supply Chain
- What it is: Modern applications are assembled from a multitude of open-source components as much as they are written from scratch. SCA is the process of automatically scanning a project's dependencies—such as NuGet packages, npm modules, or Maven artifacts—to create an inventory, often called a Software Bill of Materials (SBOM). This inventory is then checked against public and private databases of known vulnerabilities (like the CVE database) and for compliance with open-source license policies.
Why it matters: The software supply chain has become a primary target for attackers. A single vulnerable open-source library can create a critical backdoor into an otherwise secure application. The challenge is immense; Datadog's 2025 State of DevSecOps report found that the median dependency in a typical application is
215 days behind its latest version , leaving a wide window of exposure.
- Practical Integration: Dependency Scanning is another core feature of GitHub Advanced Security for Azure DevOps.
- Automatic Enablement: This capability is automatically activated for a repository as soon as GitHub Advanced Security is turned on.
- Continuous Scanning: The tool scans dependency manifest files (e.g.,
packages.config,package.json,pom.xml) within the repository. It compares the versions of the libraries listed against the GitHub Advisory Database. - Actionable Alerts: If a vulnerable dependency is found, an alert is generated in the "Advanced Security" tab, providing details about the vulnerability and often suggesting a secure version to upgrade to. This allows teams to quickly address supply chain risks.
To learn more about notable recent attacks and the vital importance of supply chain security, see How a Single Phishing Attack Broke the Open-Source Supply Chain. Understanding supply chain risks has never been more essential.
Step 3: Dynamic Application Security Testing (DAST) – Testing in a Live Environment
- What it is: In contrast to SAST, DAST is a "black-box" testing method. It has no knowledge of the underlying source code. Instead, it interacts with a running application from the outside, just as an attacker would. It probes the application with a variety of malicious inputs and simulated attacks to identify runtime vulnerabilities, such as server misconfigurations, authentication and session management flaws, or issues that only manifest when different components interact.
- Why it matters: DAST is essential for validating that security controls are effective in a real, deployed environment. It can uncover entire classes of vulnerabilities that are invisible to static code analysis.
- Practical Integration: Because DAST requires a running application and scans can be more time-consuming, the integration strategy differs from SAST and SCA.
- Target a Staging Environment: DAST scans should be configured to run against a dedicated staging or QA environment that closely mirrors production, not on every commit to the main development branch.
- Trigger on Deployment or Schedule: A common best practice is to trigger a DAST scan as part of a CI/CD pipeline that deploys to this staging environment. Alternatively, scans can be scheduled to run on a nightly or weekly basis to provide a regular security baseline.
- Integrate with Azure Pipelines: Open-source tools like the OWASP Zed Attack Proxy (ZAP) or commercial DAST solutions can be integrated into Azure Pipelines using marketplace extensions or custom scripts to automate this testing phase.
Step 4: Secret Scanning – Preventing Credential Leaks
- What it is: This automated process scans the entire Git history of a repository for accidentally committed secrets, such as API keys, database connection strings, private cryptographic keys, and other authentication tokens.
- Why it matters: Exposed credentials are a goldmine for attackers, providing a direct path into sensitive systems. This risk is so significant that "Secret Leakage" is ranked as the #2 most critical risk in the OWASP Top 10 for Non-Human Identities (NHI2:2025).
- Practical Integration: GitHub Advanced Security provides a comprehensive, two-pronged solution for secret scanning.
- Push Protection: This proactive control can be enabled to scan incoming pushes in real-time. If a secret is detected, the push is blocked before the secret ever enters the repository's history, preventing the leak entirely.
- Repository Scanning: For existing codebases, the tool continuously scans all branches for any secrets that may have been committed before push protection was enabled. When a secret is found, it generates an alert for immediate remediation.
Step 5: Unifying Visibility with Microsoft Defender for Cloud
- What it is: While the tools above secure the code and pipeline, Microsoft Defender for Cloud provides a higher-level Cloud Native Application Protection Platform (CNAPP). It connects the findings from the development lifecycle with the real-time security posture of the deployed cloud infrastructure.
- Why it matters: Context is king in security. A low-severity vulnerability in an internal-facing service is a low priority. That same vulnerability becomes a critical, hair-on-fire emergency if it's in a piece of code that Defender for Cloud knows is running on a publicly exposed virtual machine with elevated permissions. This "code-to-cloud" context allows security and development teams to intelligently prioritize the most critical risks.
- Practical Integration:
- Establish the Connection: An Azure DevOps organization can be connected to Defender for Cloud by creating a connector in the Defender for Cloud environment settings.
- Correlate Findings: Once connected, Defender for Cloud ingests the security alerts from your pipeline scans (SAST, SCA, secrets, and even Infrastructure as Code scans). It then correlates these findings with its own analysis of your cloud resource configurations, providing a unified view of risk that spans the entire lifecycle.
The ultimate success of a DevSecOps program is not measured by the number of tools purchased, but by the effectiveness of its feedback loops. The most powerful implementations are those that deliver security feedback directly into the developer's native workflow—the IDE, the command line, and the pull request. By providing alerts that are timely, contextual, and actionable, organizations can empower developers to become the first and most effective line of security defense.
The DevSecOps Payoff: Hardening Security While Accelerating Delivery

The adoption of a mature DevSecOps practice is not a cost center; it is a strategic investment that yields tangible returns across the business. By embedding security into the fabric of the development process, organizations can simultaneously strengthen their security posture and accelerate their ability to innovate.
Quantifying the Impact
The data from organizations that have successfully implemented DevSecOps is compelling and speaks directly to the core concerns of engineering and security leadership:
- Massively Accelerated Remediation: Mature DevSecOps organizations resolve security flaws an astonishing 11.5 times faster than their less-mature counterparts. This is the direct result of finding issues earlier when they are simpler and cheaper to fix.
- Improved Responsiveness: The ability to react quickly is a key indicator of a strong security program. Among organizations with fully integrated security practices, 45% can address new vulnerabilities within a single day. This figure plummets to just 25% for organizations with low levels of integration.
- Drastically Reduced Risk Profile: Proactive security leads to more secure products. A 2025 study revealed that applications built by companies with a mature DevSecOps approach are less than half as likely to contain vulnerabilities (22%) compared to those built without one (50%).
Beyond Security: The Business-Wide Benefits
The advantages of DevSecOps extend far beyond the security team, creating a positive ripple effect that impacts the entire organization's bottom line and competitive agility. For example, as highlighted in Scaling SaaS: Executive Strategies for 1 Million+ Users, operational maturity is crucial for sustainable growth and security alike.
- Reduced Remediation Costs: By operationalizing the "Shift Left" principle and catching flaws early, organizations avoid the exponential cost explosion of post-release fixes. This translates into significant financial savings, freeing up engineering resources from costly emergency patching cycles to focus on creating new value.
- Faster Time-to-Market: One of the most counterintuitive but powerful benefits of DevSecOps is its ability to accelerate delivery. By replacing slow, manual security review gates with fast, automated checks within the CI/CD pipeline, organizations remove critical bottlenecks. One case study documented a 50% improvement in release cadence after implementing an automated, secure pipeline. This allows the business to respond more quickly to market demands and outmaneuver competitors.
- Enhanced Compliance and Trust: In a world of increasing regulation (GDPR, HIPAA, PCI DSS), proving compliance is a major challenge. A DevSecOps pipeline with automated security and policy checks creates a continuous, auditable trail of evidence. This simplifies audits and demonstrates a commitment to security that builds invaluable trust with customers and partners.
This holistic approach is central to how we operate at Baytech Consulting. Our ability to deliver a Tailored Tech Advantage —crafting bespoke solutions with cutting-edge technology—is built upon a deep-seated foundation of these secure-by-design principles. For our highly skilled engineers, security is not an added feature or a final checklist item. It is an integral part of our agile development process, ensuring the enterprise-grade quality, on-time delivery, and robust security that our clients in demanding industries like finance, healthcare, and high-tech have come to expect. For organizations navigating compliance-heavy sectors, tools described in AI Governance and Asset Management: The Strategic Framework for the Modern Enterprise provide a blueprint for scalable and compliant DevSecOps.
Your Next Move: From Theory to Action
Integrating security deeply into the DevOps lifecycle is a journey, not a destination. It requires a strategic commitment to cultural change, process refinement, and the intelligent application of technology.
A Concise Answer
To effectively integrate security into a modern DevOps lifecycle, an organization must:
- Adopt a Secure-by-Design Culture: Make security a shared responsibility, championed by leadership and owned by every member of the engineering team.
- Shift Security Left: Move security activities to the earliest possible stages of development through widespread automation.
- Automate and Integrate: Implement a toolchain for automated SAST, SCA, DAST, and Secret Scanning directly within the CI/CD pipeline.
- Empower Developers: Provide fast, contextual, and actionable security feedback directly within the tools and workflows developers use every day, such as pull requests.
Actionable Next Steps
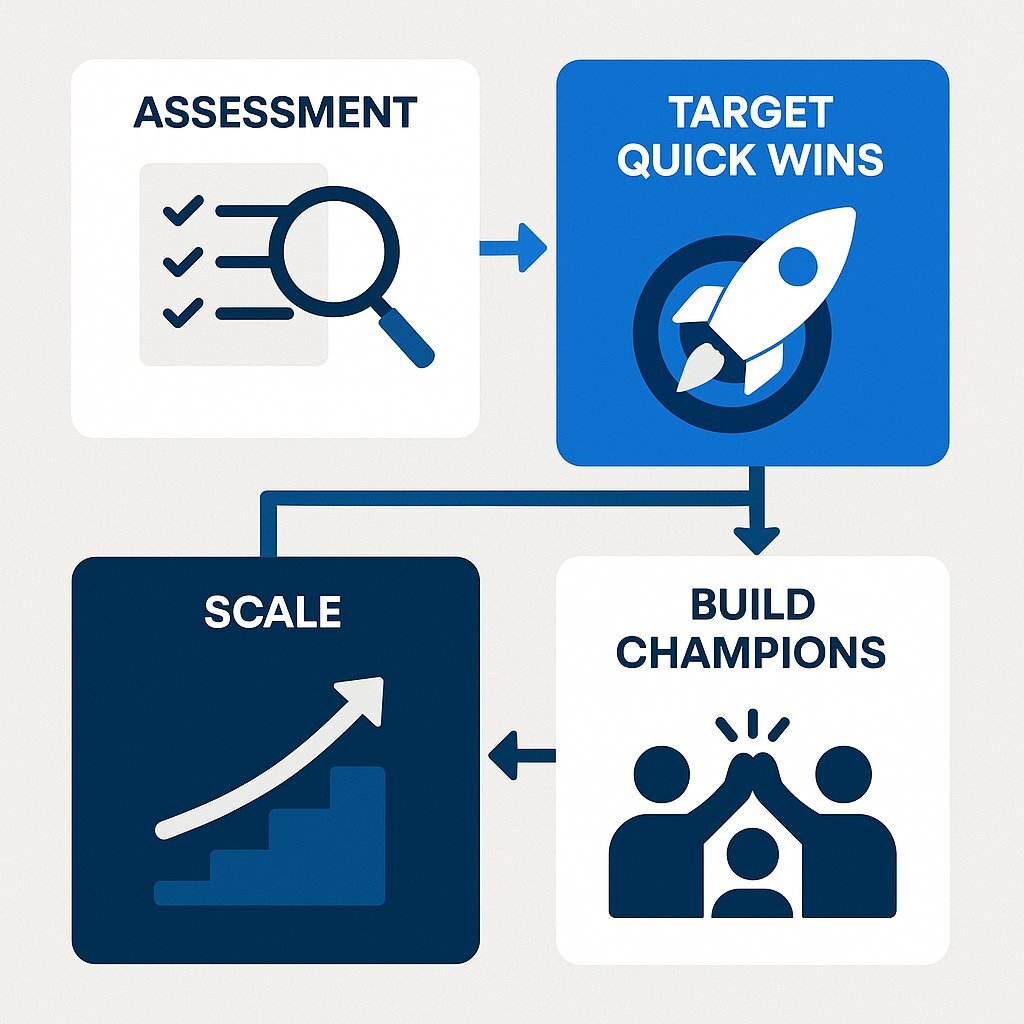
For a VP of Engineering or CSO looking to begin this transformation, a pragmatic, phased approach is most effective:
- Start with an Assessment: Before implementing any new tools, gain a clear understanding of the current state. Conduct a security maturity assessment to identify the most significant risks, process bottlenecks, and cultural challenges within the current SDLC. If you're adjusting your budget to account for these changes, see the financial playbook in How to Budget for Custom Software in 2026: Cost Drivers, Risk, and ROI Revealed.
- Target Low-Hanging Fruit: Avoid a "big bang" approach. Select a single, high-impact, low-effort initiative to build momentum. Enabling Secret Scanning on the organization's most critical source code repositories is an excellent starting point. It is relatively simple to configure and provides immediate, high-value risk reduction.
- Build Champions and Scale: Use the success of the initial project to secure buy-in for subsequent steps, such as rolling out SAST. Identify enthusiastic developers and security professionals to form a cross-functional team of "security champions." This group will be instrumental in driving the necessary cultural change, providing training, and advocating for the new processes across the organization. And for those looking to drive larger transformation, explore key Agile and business leadership strategies that smooth the cultural path for DevSecOps.
Implementing a true DevSecOps culture requires more than just tools; it requires deep expertise in process, culture, and technology. If you're looking to accelerate your journey to secure-by-design development, contact Baytech Consulting. Our experts in custom software development and application management can help you build a strategy that hardens your security posture while enabling your teams to innovate faster.
Further Reading
- https://www.functionize.com/blog/the-cost-of-finding-bugs-later-in-the-sdlc
- https://www.crowdstrike.com/en-us/global-threat-report/
- https://www.datadoghq.com/state-of-devsecops/
About Baytech
At Baytech Consulting, we specialize in guiding businesses through this process, helping you build scalable, efficient, and high-performing software that evolves with your needs. Our MVP first approach helps our clients minimize upfront costs and maximize ROI. Ready to take the next step in your software development journey? Contact us today to learn how we can help you achieve your goals with a phased development approach.
About the Author

Bryan Reynolds is an accomplished technology executive with more than 25 years of experience leading innovation in the software industry. As the CEO and founder of Baytech Consulting, he has built a reputation for delivering custom software solutions that help businesses streamline operations, enhance customer experiences, and drive growth.
Bryan’s expertise spans custom software development, cloud infrastructure, artificial intelligence, and strategic business consulting, making him a trusted advisor and thought leader across a wide range of industries.


