
The Configuration Complexity Clock: Why Too Much Flexibility Can Hurt Your Business
September 15, 2025 / Bryan ReynoldsWhat is the Configuration Complexity Clock? (And Why It’s Costing Your Business More Than You Think)
The Slippery Slope from "Flexible" to "Fragile"
Every business leader wants software that adapts. The dream is a system so flexible that it can be tweaked on the fly to meet evolving market demands, ideally without having to call in a team of expensive developers for every minor change. It’s a noble goal, born from a desire for agility and control. Yet, this very pursuit of flexibility often leads organizations down a treacherous path, transforming a clean, manageable application into a complex, brittle, and staggeringly expensive liability.
This is the central paradox of software configuration. The journey begins with a simple, well-intentioned idea: "Let's move this value out of the code so we don't have to redeploy every time it changes." But this first step can initiate a chain reaction. Over time, more and more business logic migrates from the explicit, well-structured world of code into a nebulous, often undocumented realm of configuration files. This creates a hidden, second system—a "shadow IT" platform—that is rarely designed, tested, or version-controlled with the same rigor as the application code it's supposed to control. This shadow system is where agility goes to die.
To understand this dangerous evolution, software architect Mike Hadlow developed a powerful metaphor: the Configuration Complexity Clock . It’s a model that visualizes the lifecycle of an application as it succumbs to this creeping, configuration-driven complexity. It tells a story of how good intentions pave a road to an operational nightmare.
However, the pressure to externalize configuration is often a symptom of a deeper organizational ailment: a slow, high-friction, and high-risk deployment process. When releasing a new version of the software is a multi-week, all-hands-on-deck event fraught with peril, the business will naturally seek workarounds. The demand to make changes via "configuration" becomes a way to bypass a broken and untrustworthy delivery pipeline. In the modern era of DevOps, where deployments can be trivial, safe, and executed multiple times a day, the original sin that starts the clock ticking—the fear of redeployment—is largely a solved problem. Therefore, an organization's position on the clock is not just a measure of technical architecture; it's a stark indicator of its operational maturity.
Decoding the Clock: A Journey in 12 Steps
The Configuration Complexity Clock is a model that illustrates how a system's configuration evolves from simple, manageable data into a complex, quasi-programming language that becomes a significant source of risk and technical debt. As an application travels clockwise, the technical implementation becomes successively more elaborate, bug-prone, and difficult for new engineers to learn.
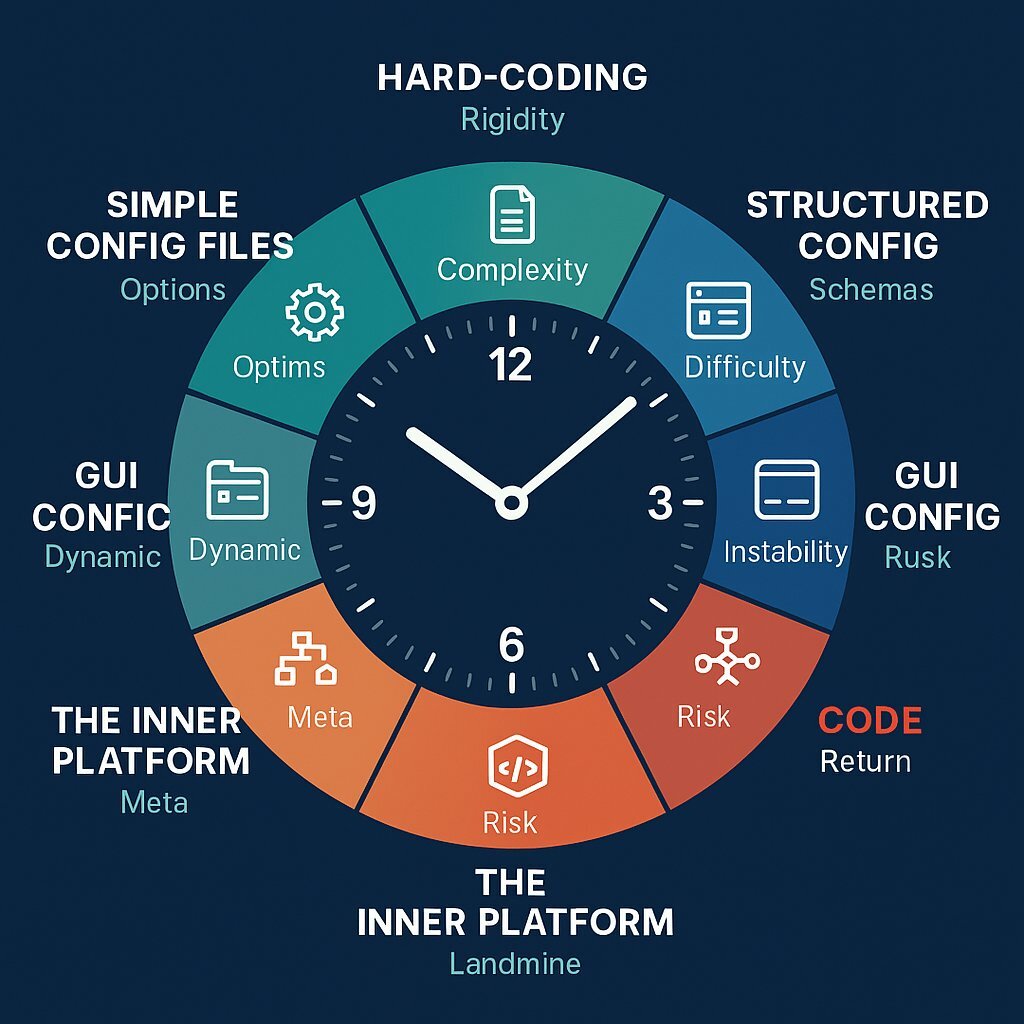
12-3 o'clock: The Honeymoon Phase (Hard-Coding to Config Files)
- 12:00 - Hard-Coding: The journey begins at midnight. A new application is built to solve an immediate business need. To get it done quickly, all values—timeouts, labels, business-specific numbers—are hard-coded directly into the application. This approach is beautifully simple, explicit, and easy for any developer to understand and reason about. The "cost" is its rigidity; every change, no matter how small, requires a modification to the source code and a full redeployment of the application.
- 2:00 - Simple Config Files: Soon, the business realizes that some values change more frequently than the code itself, or differ between development, staging, and production environments. The logical first step is to externalize these values into simple key-value configuration files (like
.envfiles orappsettings.json). This is a healthy and necessary stage for things like database connection strings, API keys, and feature flags. It's the sweet spot where most simple applications should happily reside for their entire lifecycle.
4-6 o'clock: The Point of No Return (Complex Schemas & GUIs)
- 4:00 - Structured Config (XML/YAML/JSON): As the application becomes more entrenched in the organization, its requirements grow. The business now needs to configure not just single values, but hierarchies, lists, and complex objects. The simple key-value file is no longer sufficient. The configuration moves into a structured format like XML, YAML, or JSON, which is then deserialized into a strongly-typed configuration object within the code. While this handles complexity better, it introduces new dangers. The configuration files can become deeply nested, difficult for humans to parse, and prone to subtle errors that are hard to validate.
- 6:00 - GUI-Based Configuration: This stage represents the "great false hope" of configuration. To empower non-technical users, a graphical user interface (GUI) is built on top of the structured configuration model. The dream is that a business analyst or product manager can now directly tweak the application's behavior through a friendly web interface. This dream is almost never realized. The mapping of abstract business rules into the specific parameters of the configuration model remains a highly technical task that only developers or specially trained power-users can perform. The organization has now incurred a massive new cost: it must build and maintain a second, complex application (the configuration UI) that is difficult to version control, impossible to audit effectively, and adds zero value to the end customer.
7-9 o'clock: The Inner Platform (Rules Engines & DSLs)
- 7:00 - Rules Engine: The business logic becomes even more sophisticated, filled with conditionals (
if X, then Y, unless Z), exceptions, and triggers. To handle this, the team introduces a "rules engine." This is the critical tipping point where configuration ceases to be data and becomes executable logic. The configuration file is now a program, but one written in a format (often complex XML or JSON) that is hostile to developers and lacks any of the safety nets of a real programming language. 9:00 - Domain-Specific Language (DSL): The team, frustrated with the clunky and verbose nature of the rules engine, decides to invent their own mini-programming language—a Domain-Specific Language (DSL)—to express the business logic more elegantly in text files. This is the zenith of configuration complexity. The development team is now saddled with the immense burden of designing, building, and maintaining a custom-built programming language, complete with its own parser and interpreter. Crucially, this new language has none of the tooling that makes modern software development productive: no IDE with code completion, no debugger, no static analysis tools, and no established community or documentation. This phenomenon is a classic example of the
Inner-Platform Effect : the tendency of complex software systems to accidentally re-implement a poorly designed, bug-ridden, and slow version of the platform they are already running on.

10-12 o'clock: The Full Circle (Back to Code)
- 11:00 - The Pain Becomes Unbearable: The DSL is a disaster. Onboarding a new developer takes months because they have to learn the company's unique, quirky, and undocumented programming language. Debugging production issues is a nightmare of trial and error. A simple "configuration" change now requires more testing, carries more risk, and takes more time than an equivalent change in the main application's codebase. The Total Cost of Ownership (TCO) of the "flexible" configuration system is revealed to be astronomical.
- 12:00 - The Return to Code: The journey comes full circle. The organization makes the painful but necessary strategic decision to scrap the DSL and the rules engine. The complex business logic is migrated back into a general-purpose programming language (like C#, Python, or Java), where it belongs. Here, it can be properly managed with professional tools, covered by automated tests, debugged effectively, and refactored safely. Hard-coding, once seen as the problem to be solved, is now correctly identified as the "least evil option" for managing complex, algorithmic business rules.
| Clock Position | Stage Description | Key Characteristics & Risks |
|---|---|---|
| 12:00 | Hard-Coded Values | Simple, explicit, versioned in Git. Risk: Inflexible for frequent or environment-specific changes. |
| 2:00 | Simple Config Files | Externalizes simple values. Good for secrets, feature flags, environment settings. Risk: Can become a messy "junk drawer" if not managed. |
| 5:00 | Structured Config (XML/YAML) | Handles hierarchical data. Risk: Becomes deeply nested, hard to validate, encourages logic-in-data. |
| 7:00 | GUI Configuration | Aims for "business user" control. Risk: Adds a complex UI, hard to version/test, rarely achieves its goal. |
| 9:00 | Rules Engine / DSL | Configuration becomes a custom programming language. Risk: Massive hidden cost, no tooling, hard to debug, high learning curve. |
| 11:00 | The Inner Platform | The configuration system is now a separate, complex product. Risk: Drains resources, slows innovation, becomes the primary source of production failures. |
The Business Impact: How Configuration Complexity Drains Your Bottom Line
The journey around the Configuration Complexity Clock is more than a technical curiosity; it's a direct and often invisible drain on a company's financial and operational health. Moving past the early, sensible stages of configuration isn't a free lunch. It's a loan taken against future productivity, and the interest payments are steep. This is the essence of technical debt: the implied cost of rework caused by choosing an easy or seemingly flexible solution now instead of a better, more sustainable approach.
This is a critical concept for any business leader to grasp because the initial appeal of complex configuration systems is that they appear to lower the upfront cost of a change by avoiding developer involvement. This, however, is a dangerously flawed calculation of Total Cost of Ownership (TCO). It myopically focuses on the initial acquisition cost of a feature while completely ignoring the massive, compounding long-term costs of maintenance, debugging, operational risk, and training. The Configuration Complexity Clock is a perfect case study in how poor TCO analysis leads to disastrous technical investments.

The Productivity Sink: When Flexibility Kills Velocity
Developer time is one of the most valuable and expensive resources in any modern company. When that time is spent deciphering a labyrinth of interacting XML files, GUI settings, and arcane DSL scripts, it's not being spent on building the revenue-generating features that drive the business forward. Leading IT executives now recognize that for true competitive advantage, development hours should center on delivering user value, not untangling unnecessary complexity.
Research has shown that complex code can require 250-500% more maintenance time than simple code of the same size. Complex configuration is arguably worse, as it lacks the mature tooling and established patterns that help manage code complexity. As a system moves further around the clock, developer productivity plummets. The cognitive load required to understand the system's behavior increases exponentially, as engineers must now hold two systems in their head: the application code and the separate, often poorly understood, configuration "program". This directly slows down time-to-market, delays feature releases, and frustrates the very talent hired to innovate.
The Technical Debt Spiral: Paying Interest on Bad Decisions
Each step around the clock, from structured configuration onwards, adds a new and more burdensome layer of technical debt.
- The structured XML file is design debt , a compromise made for flexibility that complicates future changes.
- The GUI configuration tool is architectural debt , a whole new system that must be maintained and updated, often evolving without a clear plan.
- The DSL is the ultimate form of code debt , containing poor-quality "code" that is nearly impossible to understand, maintain, or extend.
The "interest payments" on this accumulated debt manifest in tangible business costs:
- Slower Development: New features take longer to implement because they have to navigate the complex interactions between code and configuration.
- More Bugs: The lack of testing and validation for the configuration system leads to more defects slipping into production.
- Lower Morale: Talented engineers become demoralized when they spend their days fighting a brittle, over-engineered system instead of solving interesting problems.
Increased Risk and Fragility: The Danger of Untestable "Data"
Application code benefits from a mature, multi-billion dollar ecosystem of quality control: unit tests, integration tests, static analysis tools, and rigorous peer review processes. Complex configuration systems, particularly rules engines and DSLs, rarely have any of these safeguards.
When your configuration becomes executable logic, a change to a "simple" config file carries the same risk as a change to the core source code. Yet, it is often treated with far less rigor, pushed to production without adequate testing or review. This is a recipe for disaster. Production outages are no longer caused by "code bugs" but by a misplaced comma in a DSL script or an unintended interaction between two rules in an engine. This directly impacts business continuity, erodes customer trust, and creates a constant state of firefighting for the operations team.
Navigating the Clock in the Age of DevOps
The Configuration Complexity Clock was first described in 2012, a lifetime ago in the tech industry. Since then, the rise of DevOps, CI/CD, and cloud-native practices has fundamentally altered the landscape of software delivery. The core assumptions that drove teams around the clock are no longer valid for high-performing organizations.
Has Modern Tooling Broken the Clock?
The central premise that "recompiling and redeploying is expensive and risky" has been systematically dismantled by modern engineering practices. For a team with a mature Continuous Integration and Continuous Deployment (CI/CD) pipeline, a code change can be automatically built, tested across multiple stages, and deployed to production in a matter of minutes, with near-zero downtime and a high degree of confidence.

In this new reality, the cost of changing a line of well-tested code is often significantly lower than the cost of changing a line in a complex, untestable DSL. The original motivation for the clock's journey has been inverted.
Furthermore, modern practices like Infrastructure as Code (IaC) and GitOps have blurred the lines between code and configuration. With modern approaches such as these, the entire environment—servers, networks, databases, and application settings—is defined in text files and stored in a Git repository alongside the application code. A change to an application's memory allocation is handled with the same process as a change to its business logic: a pull request, a peer review, and an automated deployment. This approach treats all configuration
as code , giving it the same benefits of versioning, auditing, and automated testing, thereby erasing the artificial and dangerous distinction that the clock describes.
The Baytech Approach: Strategic Configuration Management
A modern, expert approach to software development isn't about eliminating configuration entirely. It's about being deliberate, strategic, and disciplined about where complexity lives. This philosophy is central to how we at Baytech Consulting deliver lasting value to our clients.
This aligns with our Tailored Tech Advantage . We recognize that there is no one-size-fits-all answer. For a financial services application with complex, ever-evolving regulatory calculations, that logic belongs in code, where it can be rigorously unit-tested and validated. For a multi-tenant SaaS platform that needs to support different client branding and API integrations, a simple, robust, and well-documented configuration system is the correct architectural choice. The key is making a conscious, upfront decision based on the nature of the change and the total cost of ownership , not just the initial implementation effort.
This strategy is enabled by our commitment to Rapid Agile Deployment . We invest heavily in building efficient, automated CI/CD pipelines for our clients, leveraging enterprise-grade tools like Azure DevOps, Kubernetes, and Docker. By making deployments cheap, fast, and safe, we remove the primary organizational fear that forces teams down the perilous path of the Configuration Complexity Clock. We deliver genuine business agility through process excellence and mature engineering, not through complex and fragile configuration workarounds.
A CTO's Decision Framework: When to Code, When to Configure
For technology leaders, the most important takeaway is to foster a culture that asks the right questions. Before allowing a piece of logic or a value to be moved into a configuration system, challenge your team with a simple framework. The following table provides a practical tool to guide architectural discussions and ensure that decisions are made for the right reasons.
| Factor | Favorable to External Configuration | Favorable to Code |
|---|---|---|
| Change Frequency | High (changes more often than deployments) | Low (changes with the application logic) |
| Who Changes It? | Operations, SREs (environment variables) | Software Developers (business rules) |
| Required Expertise | Low (simple value changes, API keys) | High (involves algorithms, conditionals) |
| Environment Variation | High (DB strings, hostnames vary per env) | Low (core business logic is universal) |
| Need for Validation | Simple validation (e.g., is it a number?) | Complex business rule validation & unit testing |
| Audit & Versioning | Needs a dedicated system or GitOps approach | Handled natively by Git |
| Blast Radius of Error | Low (e.g., wrong color hex code) | High (e.g., incorrect insurance calculation) |
Conclusion: Setting Your Company's Clock to the Right Time
So, what is the Configuration Complexity Clock? It is a powerful model that reveals how the noble pursuit of "flexibility" through configuration can paradoxically create a rigid, complex, and expensive system. It impacts software development and application management by being a primary driver of technical debt, slowing developer velocity to a crawl, and dramatically increasing the risk of production failures. It is a cautionary tale of good intentions leading to bad outcomes.
For business and technology leaders, understanding this dynamic is the first step toward reclaiming control. It’s a topic also at the heart of Agile methodology, where the right balance between code, configuration, and process unlocks true agility.
Your Next Steps:
- Audit Your "Flexibility": Take a critical look at your key software assets. Where do they sit on the clock? Do you have a "rules engine" that only one person on the team understands? Is there a custom DSL that has become a bottleneck for innovation? Be honest about where complexity is hiding in your organization—and consider how software development jargon and misunderstanding of terms can amplify these hidden difficulties.
- Calculate the Total Cost of Ownership (TCO) of Your Configuration: Look beyond the perceived convenience. Work with your finance and engineering leads to quantify the hidden costs: How many developer-hours per month are spent debugging configuration issues? What is the onboarding time for your custom systems? What was the business cost of the last outage caused by a "simple" config change?.
- Invest in Your Deployment Pipeline: The most effective antidote to the Configuration Complexity Clock is to make code deployment a fast, reliable, and low-stress event. Frame investment in CI/CD, automation, and practices like GitOps not as a technical cost center, but as a strategic investment in business agility. This is how you empower your teams to keep complexity where it belongs: in well-structured, testable, and maintainable code. To dig deeper on this shift, see our guide to executive software maintenance and evolution.
Managing complexity is at the heart of building software that delivers a sustainable competitive advantage. If you're concerned that your systems are ticking towards midnight on the complexity clock, let's talk. The expert engineers at Baytech Consulting can help you audit your current state and architect a solution that balances true flexibility with long-term maintainability and value.
Further Reading
- http://mikehadlow.blogspot.com/2012/05/configuration-complexity-clock.html
- https://www.devjoy.com/blog/the-challenge-today-is-overwhelming-complexity/
- https://continuousdelivery.com/foundations/configuration-management/
About Baytech
At Baytech Consulting, we specialize in guiding businesses through this process, helping you build scalable, efficient, and high-performing software that evolves with your needs. Our MVP first approach helps our clients minimize upfront costs and maximize ROI. Ready to take the next step in your software development journey? Contact us today to learn how we can help you achieve your goals with a phased development approach.
About the Author

Bryan Reynolds is an accomplished technology executive with more than 25 years of experience leading innovation in the software industry. As the CEO and founder of Baytech Consulting, he has built a reputation for delivering custom software solutions that help businesses streamline operations, enhance customer experiences, and drive growth.
Bryan’s expertise spans custom software development, cloud infrastructure, artificial intelligence, and strategic business consulting, making him a trusted advisor and thought leader across a wide range of industries.


