
The Truth About Magic Links: UX, Security, and Growth Impacts for SaaS Platforms
July 22, 2025 / Bryan ReynoldsExecutive Summary
Magic links present a compelling narrative of frictionless, passwordless authentication, promising to solve the chronic "password pain" that plagues users and drives up support costs. However, a comprehensive analysis reveals that their practical effectiveness for Software-as-a-Service (SaaS) applications is fraught with significant user experience, security, and implementation challenges. This report finds that magic links do not eliminate authentication problems but rather trade the well-understood risks of passwords for a new, more complex set of vulnerabilities intrinsically tied to the reliability and security of email protocols.
The purported benefits for user adoption and conversion, while theoretically plausible, are not substantiated by rigorous, independent research. The available data largely consists of claims from authentication vendors, making it difficult to separate marketing from reality. The success of a magic link system is highly conditional, depending on flawless execution in areas outside of a developer's control, most notably email deliverability. Delays, spam filters, and email client behaviors can transform a supposedly seamless flow into a frustrating user experience.
Recent security disclosures have further tarnished the appeal of magic links, revealing systemic vulnerabilities that go beyond simple email account compromise and can lead to complete account takeover even with a secure inbox. These risks make them an unsuitable choice for high-security or regulated environments.
In the current landscape, magic links are increasingly overshadowed by superior passwordless alternatives. Social logins offer comparable convenience with more robust security managed by dedicated identity providers, albeit at the cost of user data control. More importantly, passkeys, built on the phishing-resistant WebAuthn standard, offer a fundamentally more secure and user-friendly experience that is rapidly becoming the industry benchmark.
Therefore, this report recommends that SaaS companies view magic links not as a primary, modern authentication strategy, but as a transitional technology or a niche solution for specific, low-risk use cases like temporary access or infrequent logins. The strategic priority for forward-looking SaaS products should be the adoption of passkeys. This report serves as an in-depth guide for product leaders to navigate this complex decision, providing the necessary data, frameworks, and implementation checklists to determine if, when, and how to leverage magic links within a broader, more resilient authentication strategy.
The Anatomy of a Magic Link
Understanding the effectiveness of magic links requires a foundational knowledge of their technical mechanics, the journey a user undertakes during authentication, and the specific problems they are designed to solve within the SaaS ecosystem.
Deconstructing the Technology: How Tokens, URLs, and Email Work in Concert
A magic link is a passwordless authentication method that validates a user's identity by sending a unique, single-use, and time-limited URL to a verified communication channel, which is typically the user's email address. The core principle is to prove possession of the email account, which serves as the "something you have" authentication factor, replacing the "something you know" (a password).
The "magic" component of the link is a cryptographically secure token embedded within the URL. For the system to be secure, this token must be unique for every login request and computationally difficult to predict, necessitating the use of a high-quality random number generator in its creation. When a user initiates a login, the application's server generates this token, associates it with the specific user's account and the current login attempt, and stores it (or a secure hash of it) for later validation.
The overall technical flow is a sequence of well-defined steps: a user enters their email; the application generates and stores a unique token; this token is embedded into a URL to create the magic link; the link is sent to the user's email; upon clicking the link, the application server receives the request, extracts the token from the URL, and validates it against its stored value, ensuring it is authentic and has not expired; if valid, the user is granted an authenticated session.
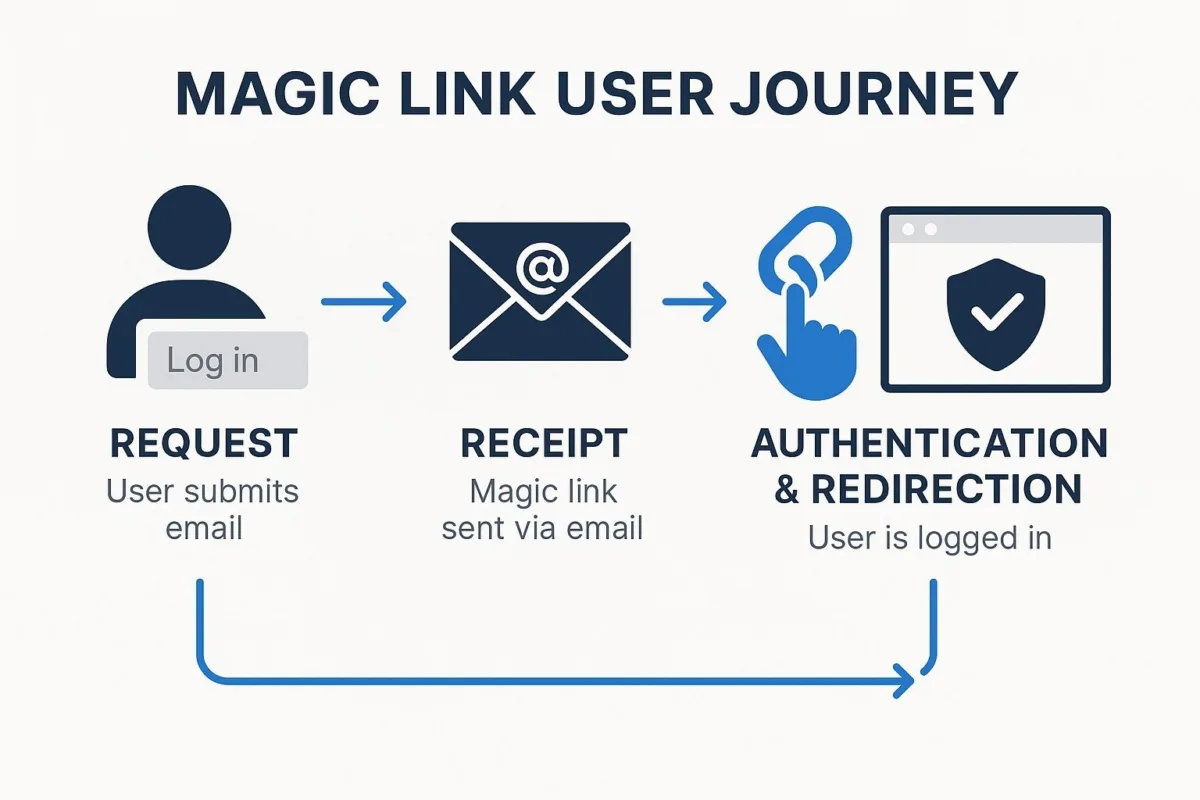
The End-User Journey: A Step-by-Step Walk-through of the Authentication Flow
From the user's perspective, the process is designed to be straightforward, unfolding in four distinct stages:
- Request: The journey begins on the application's login page, where the user enters their email address or user ID into a form. Instead of a password field, the user interface typically displays a button like "Send Magic Link" and informs the user to check their email for the next step.
- Receipt: The user must then perform a context switch, navigating away from the application to their email client. This could be on the same device or a different one, such as a mobile phone. They locate and open the email from the application.
- Action: The user clicks the prominent login link or button within the email.
- Authentication & Redirection: This action directs the user's browser back to the application. The server validates the embedded token, and upon success, establishes an authenticated session. The user is then logged in and often redirected to their intended destination, such as their dashboard or a specific piece of content they were trying to access. To prevent misuse, the magic link is immediately invalidated after its first use.
Common Use Cases in the SaaS Ecosystem: From Onboarding to Temporary Access
The versatility of this mechanism has led to its adoption across a variety of scenarios in the SaaS world:
- Primary Passwordless Login: This is the most prevalent use case, where magic links entirely replace the traditional username-password login. It is often positioned as an ideal solution for applications where users log in infrequently, as password recall is a significant friction point in such scenarios. The collaboration application Slack is a widely recognized example of this implementation.
- Seamless Onboarding & Registration: Magic links can merge the user registration and email verification steps into a single, fluid process. A new user provides their email, clicks the link they receive, and their account is simultaneously created and verified, which can significantly reduce friction during the critical sign-up phase.
- Temporary & Delegated Access: The time-limited and single-use nature of magic links makes them perfect for granting temporary access to external collaborators, consultants, or guest users without the overhead of creating and managing permanent credentials. This is also effective for sharing specific resources, like an analytics dashboard or a project document.
- E-commerce & Cart Abandonment Recovery: In an e-commerce context, a magic link can be sent to a user who has abandoned their shopping cart. Clicking the link can automatically log them in and direct them straight to their pre-filled cart, streamlining the path to purchase.
- Multi-Factor Authentication (MFA) & Device Verification: A magic link can serve as a possession factor ("something you have") in an MFA flow, adding a layer of security on top of a password. It can also be used to securely authorize a new device attempting to log into an existing account.
- Account Recovery: The magic link flow is functionally identical to the "forgot password" process. However, instead of leading to a form for creating a new password, the link logs the user in directly, offering a more immediate resolution. Data from providers like PropelAuth suggests that when users are given the choice between a direct magic link login and a traditional password reset, they often prefer the magic link.
The fundamental mechanism of a magic link is not a new invention but a clever repurposing of the familiar "password reset" workflow. The process—user provides email, system sends a unique link, user clicks link to gain access—is functionally identical. This familiarity makes the flow intuitive for users, but it also means that magic links inherit all the security vulnerabilities of email-based account recovery, a critical point that is often understated. A SaaS leader must recognize they are not adopting a revolutionary technology, but rather elevating the password reset mechanism to the primary authentication path. This understanding reveals that while magic links may be critically flawed as a primary login method, their utility for specific, bounded workflows—like granting one-time guest access—is a valuable tool in a comprehensive authentication strategy. The strategic question is not a binary choice, but a nuanced one: for which user journeys do magic links provide the optimal balance of security and convenience?
The User Experience Calculus: Frictionless Ideal vs. Practical Reality
The primary appeal of magic links is the promise of a superior user experience (UX) by eliminating "password pain." However, the reality of their implementation often introduces new and significant forms of friction, creating a stark contrast between the marketed ideal and the practical user journey.
The "Password Pain" Panacea: Analyzing the Appeal of Simplified Logins
The core UX benefit of magic links is the removal of the cognitive burden associated with passwords. Users are freed from the need to generate, remember, and manage unique, complex credentials for every service they use. This directly combats "password fatigue," the stress and frustration that leads to poor security practices like reusing the same password across multiple sites. In an ideal scenario, the flow is marketed as a "fast and seamless" experience: enter email, click link, get access. This simplicity is particularly attractive to non-technical users who may find password managers confusing or cumbersome.
Furthermore, the process leverages a familiar pattern. Most internet users have gone through a password reset flow before, making the magic link journey intuitive without a learning curve. As one online commentator noted, magic links essentially take the "I forgot my password" workflow and simply "stop labeling it with a confession," reframing a failure state as the standard, successful path.
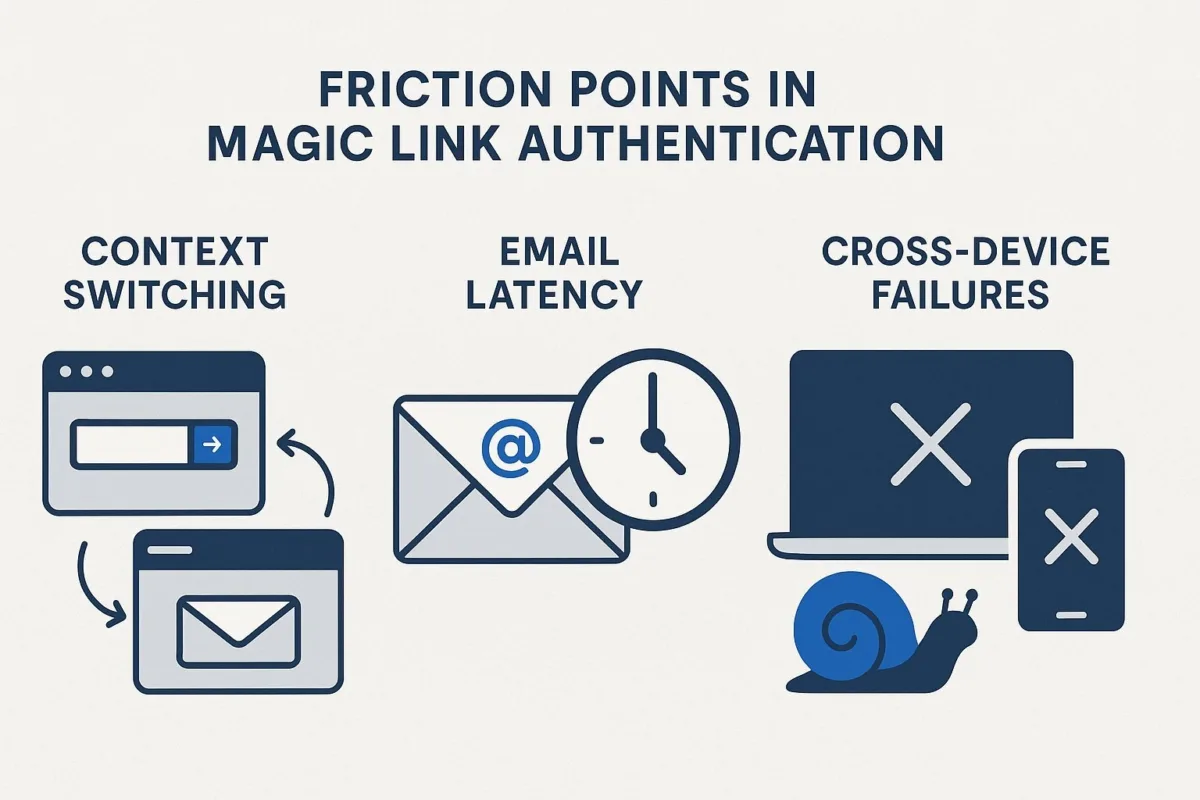
Sources of Friction: The Hidden UX Costs of Context Switching, Email Latency, and Cross-Device Failures
Despite the theoretical simplicity, the magic link workflow is riddled with potential UX pitfalls that can make it significantly more frustrating than traditional authentication.
- Context Switching: The flow inherently forces the user to disengage from the application, navigate to a separate email client, find and open the correct email, and then click a link to return. This multi-step process, especially on mobile devices, can be slow and cumbersome. One user on Hacker News vividly described the painful experience: "open website, click login... go to another app, wait for it to pull emails, look for email, open email, click link, opens in browser, maybe not the same browser..."
- Email Latency and Deliverability: The entire user experience is critically dependent on the speed and reliability of third-party email services. A delay of even a minute can leave the user waiting in a state of uncertainty and frustration. A more severe issue is when the email is incorrectly flagged as spam, forcing the user to search through their junk folder. This not only adds friction but can also lead to complete login failure and user churn.
- Cross-Device and Cross-Browser Failures: This is a major and common point of failure. A user might request a login link on their laptop but find it more convenient to check their email on their phone. Clicking the link on the phone authenticates the session in the phone's browser, leaving the original laptop session unauthenticated. This problem is exacerbated by the in-app browsers used by many social media and messaging apps, which do not share authentication cookies with the device's default browser, effectively breaking the login flow for users arriving from a shared link. To combat the security risks of this scenario, some identity providers like Okta explicitly require the link to be clicked in the same browser on the same device, otherwise the flow fails and falls back to a less convenient one-time passcode (OTP) entry.
- Email Client Link Pre-fetching: A subtle but critical technical problem arises from security features in some email clients (like Outlook) or corporate security scanners. These services often "pre-fetch" or "click" all links in an email to scan for malware. This automated action can consume the single-use magic link before the user has a chance to click it, causing their legitimate attempt to fail and forcing them to start the process over.
User Segmentation and Perception: Why Power Users and Non-Technical Users Have Divergent Experiences
The perceived value of the magic link UX is not universal; it varies dramatically depending on the user's technical proficiency.
- The Power User with a Password Manager: For users who have adopted password managers, magic links represent a significant regression in usability. Their existing workflow involves a single click or tap to autofill credentials, a process that takes seconds and occurs entirely within the context of the application. For this segment, the multi-step, context-switching nature of magic links is a slower and more frustrating experience.
- The Non-Technical User: This segment is the primary beneficiary. For individuals who do not use password managers and frequently reuse simple passwords, the process of forgetting and resetting a password is a common and painful event. The magic link flow, which is effectively a "password reset every time," provides a consistent and simplified path to access that eliminates this major point of frustration.
- The Hybrid User: Many users exist in a middle ground, perhaps using a password manager on their desktop but not their mobile devices. Their experience with magic links is inconsistent and often subject to the cross-device failure modes described above. The promise of easy multi-device access is only realized if the platform has invested in sophisticated and often complex engineering to handle these cross-device handoffs gracefully.
The "ease of use" of magic links is a marketing narrative that masks significant and predictable UX friction points. The claim of a "frictionless" experience is only valid under a narrow set of ideal conditions: instant email delivery, a single-device session, and a user who does not rely on a password manager. The evidence clearly shows multiple failure points, from email delays to cross-device issues. Consequently, a product manager cannot assume magic links are inherently "easier" and must design, build, and budget for these failure modes.
This creates a strategic paradox: by optimizing for the least technically savvy users, a SaaS application may be actively degrading the experience for its most security-conscious and potentially most engaged users who have already adopted better tools like password managers. This trade-off is critical for a SaaS business to consider when defining its target audience and designing its user journeys. Ultimately, the magic link user experience is not fully controlled by the SaaS application itself, but by a fragile chain of third parties, including the user's email provider, their client software, and their network security tools. This represents a significant loss of control over the critical login journey, a risk that must be weighed against the benefit of offloading password storage.
Measuring the Impact on SaaS Conversion and Adoption
While the theoretical benefits of magic links on user adoption and conversion are compelling, the empirical evidence is sparse and often originates from biased sources. A thorough analysis requires synthesizing the available claims, understanding the impact beyond initial sign-ups, and establishing a rigorous framework for internal testing.
Synthesizing the Data: A Review of Claims, Case Studies, and Industry Benchmarks
The narrative surrounding magic links is rich with claims of significant performance improvements. Multiple sources suggest that passwordless authentication can dramatically boost key metrics. For instance, vendors claim it can increase sign-up completion rates by 40-60% by removing the friction of password creation. A Forrester study cited by one source found that organizations using passwordless methods see a 50% reduction in user login issues. For e-commerce, simplifying checkout with magic links is said to reduce cart abandonment and increase conversions, with one case study from MojoAuth claiming a 41% reduction in cart drop-offs.
However, there is a critical gap in the available research. The vast majority of these strong quantitative claims come directly from authentication vendors who have a commercial interest in promoting the technology. Anecdotal evidence from forums provides some context—one Reddit comment cited a B2C survey where magic links constituted 30% of all logins, significantly more than passwords (4%) but less than social logins (55%). Another B2B SaaS company reported that 70% of its logins became passwordless after it was set as the default option.
Despite these anecdotes, there is a notable absence of rigorous, independent, and detailed case studies specifically analyzing the impact of magic links on SaaS conversion and adoption. The core request for "research" is met largely with marketing assertions rather than scientific evidence, underscoring the need for any SaaS company to approach these claims with skepticism and a commitment to performing its own validation.
Beyond Sign-ups: The Effect on Reducing Support Costs and Login-Related Churn
While the impact on top-line conversion is debatable, a more tangible and consistently cited benefit is the reduction in operational overhead.
- Reduced Support Costs: A major advantage of magic links is the near-elimination of password reset requests, which are a significant and costly burden for IT and customer support teams. One study estimated that a single password reset request can cost an organization an average of $70 in lost productivity and support time. By making the "password reset" flow the standard login method, this entire category of support tickets is effectively removed, leading to direct cost savings.
- Reduced Login-Related Churn: The frustration associated with forgotten passwords and complex reset procedures is a known driver of user abandonment and churn. By offering a simpler, more direct path to regain access, magic links can improve user satisfaction and foster loyalty, thereby increasing retention.
A/B Testing Framework: How to Scientifically Validate the Effectiveness of Magic Links in Your Funnel
Given the lack of independent data and the highly contextual nature of user experience, SaaS companies should not simply implement magic links but must test their effectiveness scientifically using a structured A/B testing framework.
- Formulate a Clear Hypothesis: The test must begin with a specific, measurable hypothesis. For example: "Replacing our current password-based sign-up form with a magic-link-only flow will increase our visitor-to-activated-trial conversion rate by 15% over a four-week period."
- Define Key Metrics: Success should be measured across the entire user funnel, not just at a single point.
- Acquisition: Visitor-to-signup conversion rate.
- Activation: Signup-to-activation rate (the percentage of users who complete a key first action) and the average time-to-value (TTV).
- Experience: Login success rate, average time to log in (from email request to authenticated session), and the volume of support tickets related to login failures.
- Retention: Churn rate and net dollar retention for user cohorts onboarded with magic links versus those onboarded with passwords.
- Establish a Rigorous Testing Methodology:
- Calculate Sample Size: Before launching the test, use a statistical calculator to determine the necessary sample size (e.g., number of visitors or sign-ups per variation) required to achieve a statistically significant result (typically a 95% confidence level).
- Run for Full Business Cycles: The test should run long enough to smooth out daily or weekly fluctuations in user behavior. A minimum of two full business cycles (e.g., two to four weeks) is recommended.
- Segment Results: Analyze the results for different user segments, as the impact may vary. At a minimum, segment by desktop vs. mobile traffic and new vs. returning users, as the UX of magic links differs significantly across these dimensions.
- Define Control and Variations: The baseline (Control) is the existing password flow. The challenger (Variation) is the magic link flow. Consider testing a hybrid approach as well, where magic links are offered as an alternative or as the primary "forgot password" mechanism.
Table 1: Summary of Reported Impact on Conversion & Adoption
The following table aggregates the quantitative claims found in the research regarding the impact of passwordless methods like magic links. It is crucial to note the source of each claim, as most originate from vendors, which suggests a potential for marketing bias.
| Claim | Metric | Context | Source(s) |
|---|---|---|---|
| Increase in sign-up completion | 40-60% | Passwordless authentication vs. traditional | MetaCTO |
| Improvement in auth completion | 30-50% | Magic link implementation (client results) | MetaCTO |
| Reduction in cart drop-offs | 41% | One-tap authentication vs. traditional login | MojoAuth |
| Reduction in user login issues | 50% | Organizations using passwordless methods | Forrester Study |
| Reduction in helpdesk costs | 30% | Eliminating password resets (annual savings) | MojoAuth |
| Magic Link Login Share | 30% | B2C login methods (vs. 55% social, 4% password) | Reddit Survey Anecdote |
| Passwordless Login Share | 70% | B2B SaaS with passwordless as default | Reddit User Anecdote |
The business case for magic links rests more on plausible theory and vendor marketing than on a body of independent, empirical evidence. The core value proposition—that reducing friction increases conversion—is logical. However, the glaring absence of independent, detailed case studies is a significant red flag. A strategic decision-maker must therefore treat the adoption of magic links as an experiment with a plausible but unproven hypothesis, not as the implementation of a guaranteed best practice.
The most verifiable financial benefit is not speculative revenue growth from higher conversion, but concrete cost savings from reduced support overhead. The elimination of password reset tickets is a direct and easily measurable outcome. For a large-scale SaaS platform, these operational savings could be substantial and may provide a more reliable and defensible return on investment. This shifts the business case from being purely growth-oriented to one focused on operational efficiency.
Finally, a low-risk adoption strategy is to offer magic links as the default option while retaining passwords as a secondary choice. One B2B SaaS company reported that 70% of their logins became passwordless simply by making it the default but providing a link to "sign in with a password instead." This approach caters to both non-technical users and power users, allowing user behavior to reveal preferences rather than imposing a single solution from the top down.
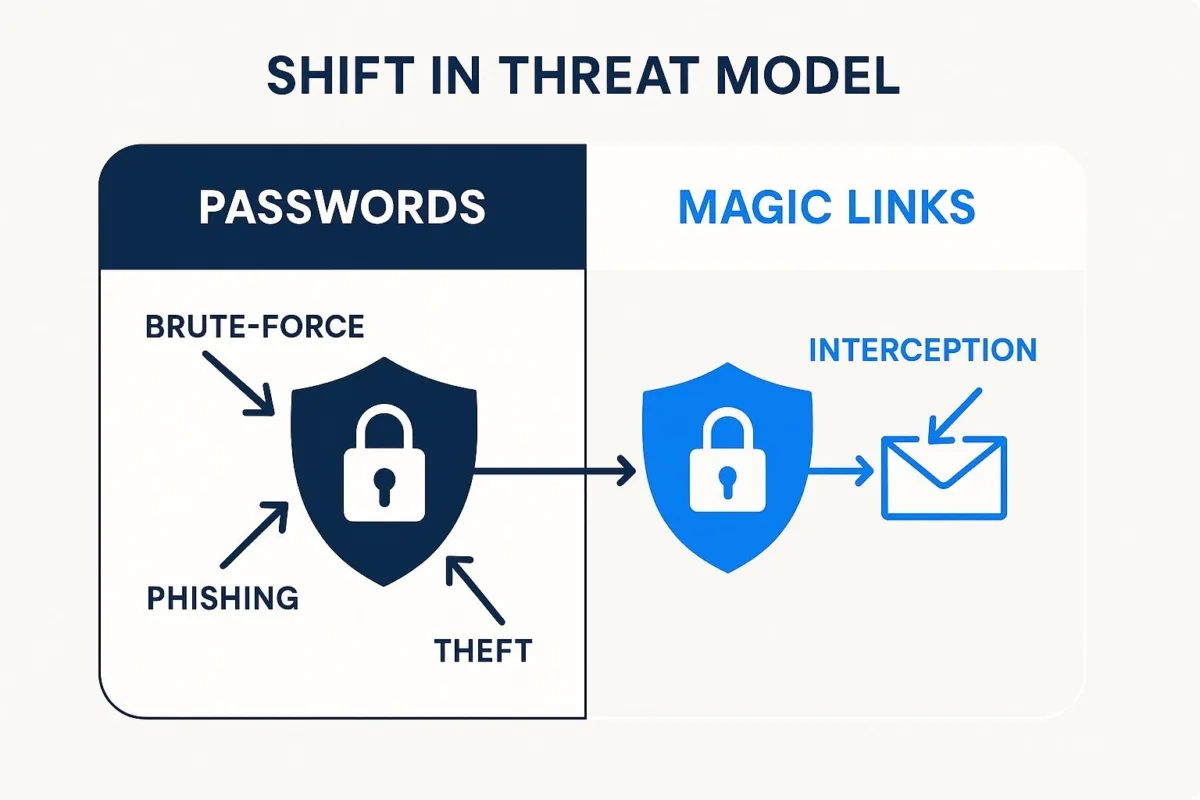
The Security Equation: Trading One Set of Risks for Another
The security of magic links is often presented as a simple improvement over passwords. In reality, it represents a fundamental shift in the threat model, eliminating well-understood password-based vulnerabilities but introducing a new set of complex and often underestimated risks.
Eliminating Password-Based Threats: A Strong Defense Against Common Attacks
The primary security benefit of magic links is the complete removal of user-managed passwords from the authentication process. This single change effectively neutralizes several of the most common attack vectors that plague traditional systems.
- Credential Stuffing and Reuse: The widespread user habit of reusing passwords across multiple services—a practice admitted by over 60% of users—is a primary cause of account takeovers. When one service is breached, attackers use the leaked credentials to attack other sites. Magic links make an application immune to this threat because there is no password to be stolen and reused.
- Weak Passwords and Brute-Force Attacks: Magic links sidestep the "human factor" of users choosing weak, easily guessable passwords. This eliminates the risk of brute-force or dictionary attacks aimed at guessing a user's password.
- Password Phishing: Traditional phishing campaigns that trick users into entering their password on a fraudulent website are rendered ineffective. Since there is no password to enter, there is no password for the attacker to steal in this manner.
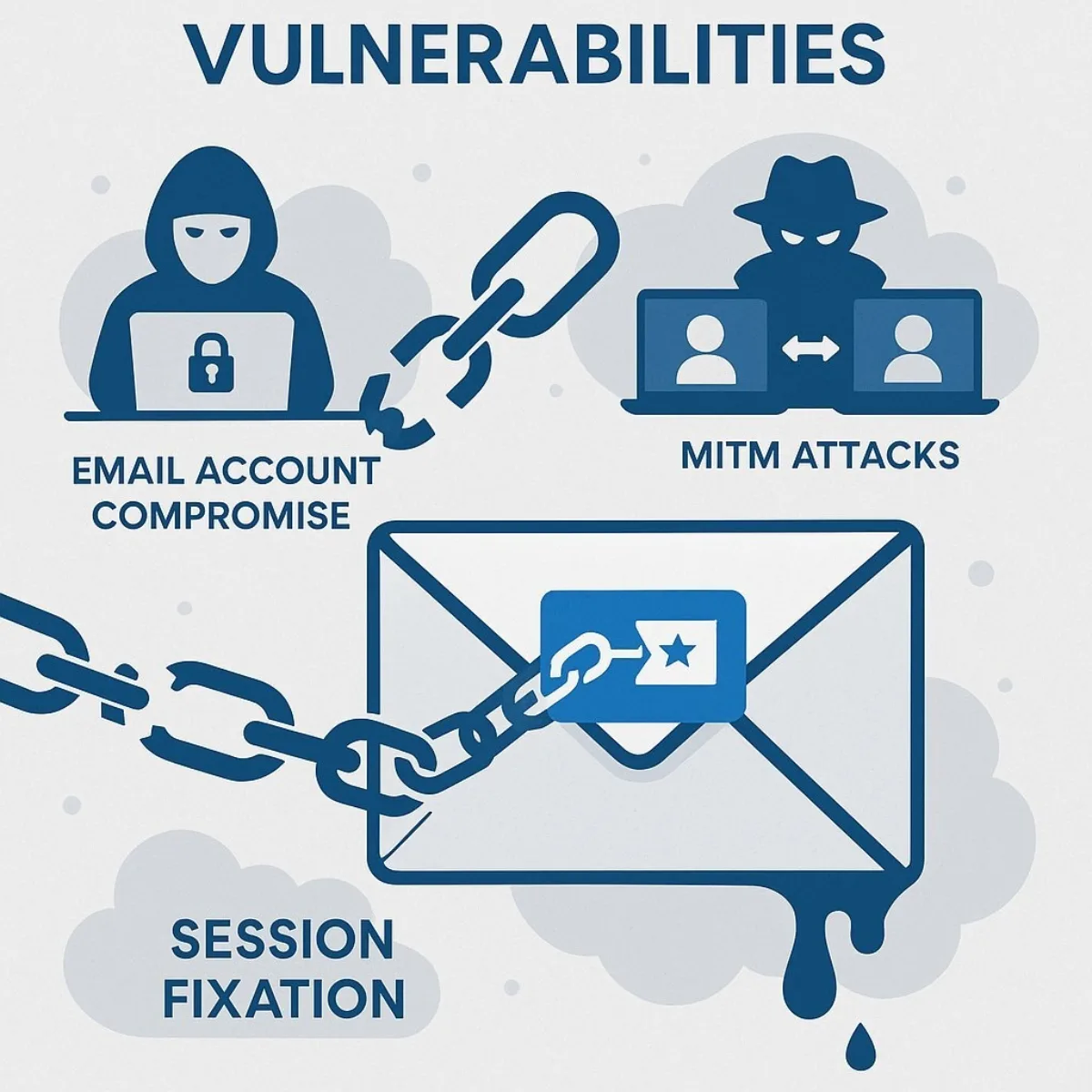
Critical Vulnerabilities: The New Attack Surface
While magic links solve old problems, they create a new and challenging attack surface centered on email and the link-handling protocol itself.
- Email Account Compromise (The Primary Risk): The security of the entire magic link system is fundamentally delegated to the security of the user's email account. If an attacker gains access to a user's inbox—through phishing, malware, or a compromised email password—they can request and intercept magic links to take over any connected application accounts. This effectively shifts the security burden from the SaaS provider's (hopefully) secure password database to millions of individual email accounts with varying and unverifiable levels of security.
- Man-in-the-Middle (MITM) Attacks: An attacker on the same unencrypted network as the user (e.g., public Wi-Fi) could potentially intercept the email containing the magic link and use the token to hijack the session. While secure transmission protocols like TLS for web traffic and SMTP help mitigate this, they do not protect against all scenarios.
- Session Fixation: In this attack, a malicious actor tricks a user into clicking a specially crafted magic link that contains a session identifier pre-determined by the attacker. When the user successfully authenticates, their session becomes associated with the attacker's identifier, allowing the attacker to take it over.
- Clickjacking: An attacker can embed the legitimate magic link login page within a transparent iframe on a deceptive website. A user might be tricked into clicking what they think is an innocuous button, but they are actually clicking the hidden magic link, authenticating a session that the attacker can then capture.
- Link Forwarding and Social Engineering: A non-technical user might be socially engineered into forwarding their magic link email to an attacker, inadvertently granting them full access. This is a user education challenge inherent in the design.
The Dfns Vulnerability Case Study: How a Flaw in Redirects Exposed a Systemic Risk
In February 2023, the security firm Dfns discovered a critical vulnerability that demonstrated a systemic risk in how magic links were implemented by several major authentication and crypto wallet providers. This attack is particularly insidious because it
does not require the attacker to compromise the user's email account.
The attack unfolds as follows:
- The attacker finds an application API endpoint that generates a magic link and allows the
redirect_url(the page the user lands on after logging in) to be specified in the request. - The attacker calls this API, providing the victim's email address and a
redirect_urlthat points to a malicious website controlled by the attacker. - The application sends a completely legitimate email with a valid magic link to the victim.
- The victim, seeing a genuine email from a trusted service, clicks the link.
- The link first authenticates the victim with the legitimate service, creating a valid session.
- The service then honors the malicious
redirect_urland sends the user—along with their new, valid session token—to the attacker's website. - The attacker's site intercepts the session token and now has full control of the victim's account.
The impact of this discovery was significant, leading some providers like Magic.io to deprecate and no longer support magic links for sensitive operations. The primary mitigation is to never allow an unauthenticated API request to specify the redirect URL, or to validate any provided URL against a strict, pre-approved allowlist. This case study highlights how a single, subtle implementation flaw can completely undermine the security of the entire system.
The security of magic links is not a simple upgrade but a fundamental shift in the threat model. The common narrative of "passwordless is good" dangerously oversimplifies the reality. While password-based attacks are mitigated, the entire model now hinges on the security of the user's email account—a factor outside the SaaS provider's control—and the perfection of the protocol's implementation. The Dfns case study shatters this simple narrative by proving that even with a secure email account, a protocol-level flaw can lead to total compromise. A product leader must understand they are not just "improving security"; they are swapping a known, battle-tested threat model for a newer, more dynamic one that is prone to subtle but catastrophic implementation errors. For any SaaS application handling high-value data, such as in finance or healthcare, the risk profile associated with email dependency and protocol fragility may be unacceptable, necessitating more robust solutions like AI-enabled development or certificate-based authentication.
A Comparative Analysis of Modern Authentication Methods
Choosing an authentication strategy requires a clear understanding of the trade-offs between user experience, security, implementation complexity, and business objectives. Magic links do not exist in a vacuum; they must be evaluated against other prevalent methods like social logins and the emerging standard of passkeys.
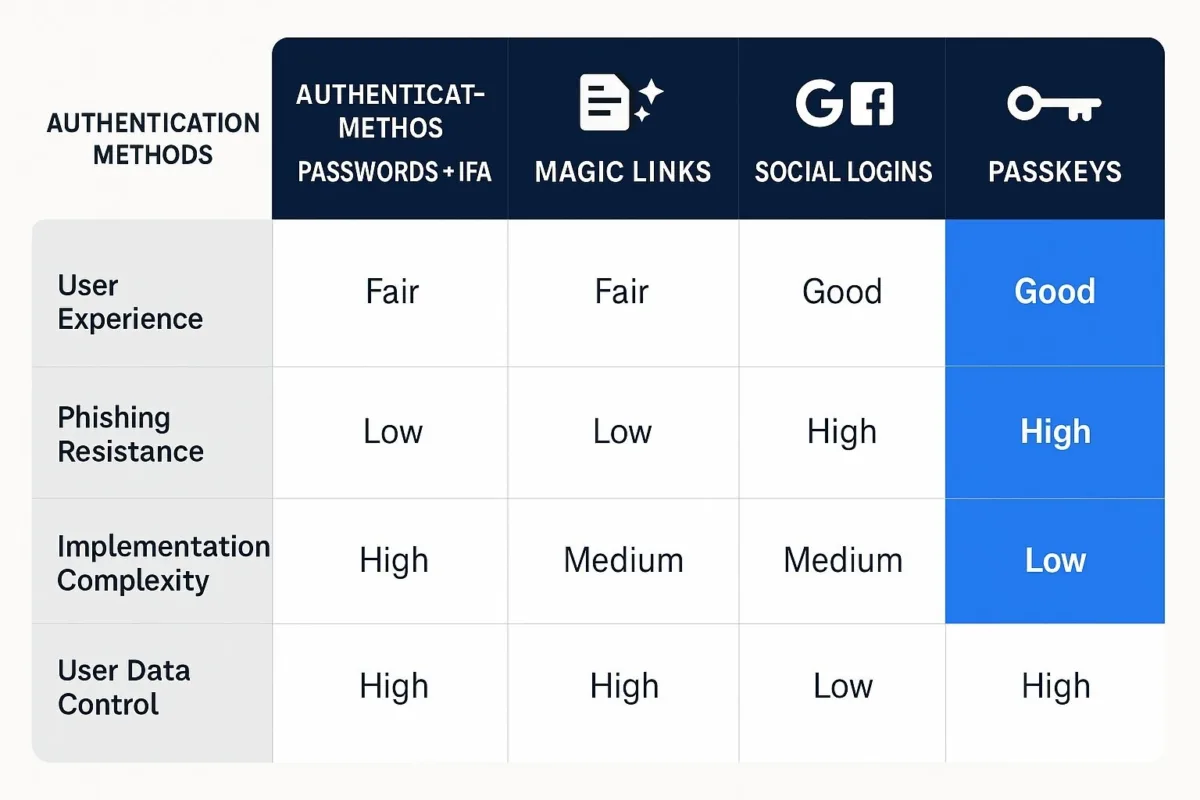
Table 2: Comparative Authentication Matrix
This matrix provides a high-level comparison of the primary authentication methods, allowing for a quick evaluation of their respective strengths and weaknesses.
| Attribute | Passwords + MFA | Magic Links | Social Login (e.g., Google/Apple) | Passkeys (WebAuthn) |
|---|---|---|---|---|
| User Experience (UX) Friction | High: Requires password creation, recall, and management; MFA adds steps. | Medium: Requires context switching to email; subject to delivery delays and cross-device issues. | Low: Often a single click; familiar flow for users. | Very Low: Seamless biometric or PIN authentication; no context switching. |
| Phishing Resistance | Low: Passwords and OTPs can be phished. | Medium: Link itself can be phished or intercepted; vulnerable to redirect attacks. | Medium: The Identity Provider (IdP) can be phished, but major providers have strong defenses. | High: Cryptographically resistant to phishing by design; private key never leaves the device. |
| Implementation Complexity (In-House) | Medium: Requires secure password hashing, storage, and MFA integration. | High: Requires secure token logic, state management, and robust email deliverability infrastructure. | High: Requires correct implementation of complex OAuth 2.0/OIDC protocols and handling provider-specific quirks. | Very High: Requires deep understanding and implementation of the complex WebAuthn cryptographic standard. |
| User Data Control | Full: The application controls all user data. | Full: Requires a verified email, ensuring direct access. | Low: Dependent on the IdP; email can be hidden by proxy (e.g., Apple). | Full: The application controls all user data. |
| Adoption Readiness | Universal: Universally understood and supported. | High: Relies on ubiquitous email access. | High: Dominated by a few major providers (Google, Apple) with massive user bases. | Growing: Supported by all major browsers and platforms, but user familiarity is still developing. |
Magic Links vs. Social Logins: The Trade-off Between User Data Control and IdP Security
When comparing magic links to social logins, the decision centers on a strategic trade-off between security robustness and control over customer data.
- User Experience: Both methods aim to reduce login friction. Social login is often perceived as faster because it typically keeps the user within a single, continuous flow without the need to switch to an email client. However, for specific workflows like one-click newsletter subscriptions where an email address is already known, a magic link can provide an even more seamless experience.
- Security: Social logins that leverage OAuth/OIDC from major providers like Google or Apple offload the security burden to a dedicated Identity Provider (IdP). These companies have world-class security teams, advanced multi-factor authentication (MFA) options, and sophisticated anomaly detection systems that monitor for suspicious login activity. This centralized, professionally managed security is generally considered superior to relying on the varied and often weak security of millions of individual users' email accounts.
- Adoption and Data Control: Social login has seen high adoption rates. One B2C case study showed usage jumping from 10% to 29% of all logins within two months of launch, with Google being the dominant provider. However, this convenience comes at a significant cost: loss of direct control over user data. "Sign in with Apple," for instance, allows users to hide their real email address behind a proxy, severing the direct line of communication that is critical for marketing, CRM, and customer support. Magic links, in contrast, are predicated on the use of a real, verified email address, ensuring the SaaS business captures this vital piece of customer data.
- Privacy: A growing user concern is the extensive data tracking associated with social logins, where platforms like Google and Facebook can use login activity for advertising and profiling. Magic links and passkeys do not involve this kind of third-party data sharing, offering a more private authentication experience.
Magic Links vs. Passkeys: Comparing a Transitional Solution to the Future Standard
The comparison between magic links and passkeys is one of a transitional technology versus the clear future standard for passwordless authentication.
- Underlying Technology: Magic links operate by transmitting a temporary secret (the tokenized link) over a communication channel like email. Passkeys are fundamentally different, being built on the WebAuthn standard which uses public-key cryptography. With passkeys, a secret (the private key) is stored securely on the user's device and never leaves it. The device simply uses this key to cryptographically "sign" a challenge from the server, proving possession without ever exposing the key itself.
- Security: This architectural difference makes passkeys inherently more secure. They are designed from the ground up to be phishing-resistant; an attacker cannot steal a passkey in the same way they can intercept a magic link. Magic links remain vulnerable to a host of threats, including email account takeover, SIM swapping attacks (for SMS-based links), and Man-in-the-Middle attacks.
- User Experience: The login flow for passkeys is demonstrably superior. It is faster and involves no context switching. The user authenticates directly on the website or app using their device's built-in biometrics (Face ID, fingerprint) or PIN. This completely avoids the UX pitfalls of magic links, such as email delivery delays, spam folder issues, and cross-device failures.
- The Industry Verdict: The consensus among security experts and major technology platforms is clear: passkeys offer a better balance of security and convenience and represent the future of authentication. Magic links are increasingly viewed as a legacy or transitional form of passwordless login.
Magic links occupy an increasingly awkward middle ground in the modern authentication landscape. When compared to social logins, they provide better control over user data but at the cost of a weaker and more fragmented security model. When compared to passkeys, they offer a vastly inferior security posture and a more fragile user experience. This positions magic links as a compromise solution that fails to excel in either security or UX when measured against the best-in-class alternatives. For a SaaS product manager, the choice between magic links and social login is a strategic decision about the value of direct customer data, while the choice between magic links and passkeys is a decision between adopting a transitional technology and investing in the future-proof standard.
Implementation Blueprint: A Guide to Secure and Effective Deployment
For organizations that, after weighing the risks and benefits, decide to implement magic links for specific use cases, a rigorous and security-first approach is paramount. A successful deployment is less about the core authentication logic and more about mastering token architecture, mitigating a wide range of vulnerabilities, and ensuring reliable email deliverability.
Part A: Secure Token Architecture
The security of the entire system rests on the integrity of the token embedded in the magic link.
- Token Generation: Tokens must be generated using a cryptographically secure pseudo-random number generator (CSPRNG). They must be sufficiently long and complex to be unpredictable and resistant to guessing or brute-force attacks.
- Token Expiration: Every token must have a short and strictly enforced time-to-live (TTL). The consensus from security practitioners suggests a lifespan of a few minutes, with recommendations typically falling in the 10-15 minute range, to strike a balance between user convenience and security. This short window minimizes the opportunity for an attacker to exploit an intercepted or old link.
- One-Time Use: A token must be invalidated immediately upon its first successful use to prevent replay attacks, where an attacker reuses a captured link. This necessitates maintaining a server-side state, for example by storing a list of valid tokens and deleting them upon use, or by keeping a denylist of used tokens. This requirement directly contradicts the "stateless" benefits often associated with using JSON Web Tokens (JWTs) for this purpose.
- Secure Storage and Handling: Tokens must be stored securely on the server, ideally in a hashed format, to prevent misuse in the event of a database breach. While JWTs can be used to embed claims like expiration time, they result in excessively long and unwieldy URLs. A shorter, opaque token that is looked up in a secure server-side database is often a more robust and manageable approach.
Part B: Mitigating Core Vulnerabilities
A secure implementation requires a defense-in-depth strategy that addresses each of the known attack vectors. The following checklist provides an actionable guide for developers and security teams.
Table 3: Magic Link Security Vulnerability & Mitigation Checklist
| Vulnerability | Description | Mitigation Strategy |
|---|---|---|
| Email Account Compromise | An attacker gains access to the user's email inbox and can intercept magic links. | Implement application-level Multi-Factor Authentication (MFA) as an additional security layer. Educate users on the importance of securing their email accounts with MFA. |
| Open Redirect | An attacker crafts a link that redirects the user to a malicious site after login to steal the session token. | Strictly validate any redirect_url parameter against a predefined allowlist of trusted domains. Never allow the redirect URL to be set by an unauthenticated API request. |
| Cross-Device/Browser Vulnerability | An attacker initiates a login and tricks the user into clicking the link on a different device, authenticating the attacker's waiting session. | Enforce same-device, same-browser validation. This is typically done by setting a secure, HttpOnly cookie or state token in the browser that initiates the request and verifying its presence when the magic link is clicked. |
| Link Interception (MITM) | An attacker on an unsecure network (e.g., public Wi-Fi) intercepts the email and steals the link. | Enforce Transport Layer Security (TLS/HTTPS) for all application traffic. Ensure the email provider uses secure transmission protocols like SMTP over TLS. |
| Session Fixation | An attacker provides the user with a link containing a known session ID, hijacking the session post-authentication. | Always generate a new, secure session identifier upon successful authentication via the magic link. Do not reuse any existing session identifiers. |
| Clickjacking | An attacker embeds the login page in a hidden iframe on a malicious site to trick the user into clicking the link. | Implement X-Frame-Options: DENY or Content-Security-Policy: frame-ancestors 'self' HTTP response headers to prevent the login page from being framed by other sites. |
| Token Guessing / Brute Force | An attacker attempts to guess valid tokens or floods the system with login requests. | Use long, high-entropy tokens generated by a CSPRNG. Implement strict rate limiting on both login attempts per user/IP and on magic link generation requests. |
Part C: Optimizing Email Deliverability
The entire magic link system is critically dependent on the email reaching the user's primary inbox quickly and reliably. This is a significant and often underestimated challenge.
- Domain Authentication: This is the foundational requirement. Configure Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) records for your sending domain. These DNS records prove to receiving mail servers that your emails are legitimate and not spoofed.
- Sender Reputation: Use a dedicated subdomain (e.g.,
auth.yourapp.com) for sending transactional emails like magic links. This isolates their sender reputation from your marketing emails, so a problem with one does not affect the other. New sending domains and IPs should be "warmed up" by sending low volumes of email initially and gradually increasing the volume over time. - Email Content and Formatting:
- The email's content must be simple, transactional, and focused on a single call-to-action: clicking the link. Avoid marketing language, excessive imagery, or multiple competing links.
- Use a clear, recognizable "From" name and a direct, unambiguous subject line (e.g., "Your [App Name] login link").
- Ensure all URLs within the email, including those for images, match the sending domain. Mismatched domains are a major red flag for spam filters.
- Crucially, avoid using link shorteners and disable open/click tracking for magic link emails. These tools, common in marketing, rewrite links to go through a tracking redirect, which is highly suspicious behavior for a transactional authentication email and can severely damage deliverability.
- Keep the total email size small (under 102KB to prevent clipping in Gmail) and always include a plain-text version for maximum compatibility.
- Preventing Conversation Threading: Email clients like Gmail often group emails with similar subjects into a single conversation thread. This can cause users to click on an old, expired magic link instead of the new one they just requested. To prevent this, ensure each magic link email has a unique subject line (e.g., by dynamically inserting a timestamp) or uses unique
In-Reply-ToandReferencesheaders. - User Guidance: Proactively guide users by providing clear instructions to check their spam or promotions folders and to add your sending address (e.g.,
login@yourapp.com) to their contacts or allowlist.
The process of implementing magic links is not primarily an authentication project; it is an email deliverability and security architecture project. The most common and critical failure points lie outside the core token validation logic, in areas like email infrastructure and subtle security flaws like open redirects. This reality makes the "build vs. buy" decision heavily skewed towards "buy" for any organization that is not a dedicated identity and security specialist. The sheer number of potential pitfalls—from cryptographic best practices to DMARC policies—creates a massive surface area for error. The risk and ongoing maintenance cost of a homegrown solution are likely to far exceed the subscription cost of a specialized identity platform like Auth0, Okta, or Clerk, which have dedicated teams to solve these complex problems.
Strategic Recommendations and Future Outlook
The decision to adopt magic links requires a nuanced strategic assessment that balances immediate UX goals with long-term security posture and technological trends. While they offer a solution to password fatigue, they are a transitional technology with significant drawbacks.
Decision Framework: When to Use Magic Links (and When to Avoid Them)
Magic links are not a one-size-fits-all solution. Their suitability is highly dependent on the specific context of the application and its users.
Recommended Use Cases:
- Applications with Infrequent Logins: For services where users log in rarely (e.g., monthly or quarterly), password recall is a major barrier. The "password reset every time" model of magic links is a natural fit for this scenario, as it aligns with the user's likely behavior.
- Low-Security Consumer Applications: In B2C contexts where maximizing top-of-funnel conversion and reducing onboarding friction are the primary goals, and the data being protected is not highly sensitive, the UX benefits of magic links may outweigh the security risks.
- Specific, Bounded Workflows: Magic links excel as a tool for discrete tasks, such as granting temporary access to external collaborators, enabling one-time document sharing, streamlining waitlist onboarding, or providing guest access to a specific feature.
Use Cases to Avoid:
- Applications with Frequent Logins: For platforms that require daily or high-frequency use (e.g., enterprise productivity tools), the context switch to email for every login introduces significant friction and is a poor user experience compared to persistent sessions, password managers, or passkeys.
- High-Security and Regulated Environments: For applications in fintech, health-tech, or any enterprise SaaS that handles sensitive customer or financial data, the inherent security risks are likely unacceptable. The reliance on variable email security and the existence of protocol vulnerabilities make magic links a poor choice where trust and security are paramount.
- As a Primary, Forward-Looking Authentication Strategy: Given the clear industry momentum towards superior alternatives, choosing magic links as the sole, long-term authentication strategy for a new application is a technologically backward-looking decision.
The Hybrid Approach: Using Magic Links as a Component, Not a Panacea
Rather than a binary adoption, the most effective strategy is often to integrate magic links as one component within a more comprehensive authentication system.
- As a Fallback and Recovery Option: Offer a magic link as a more user-friendly alternative to the traditional multi-step password reset flow. This provides convenience for users who have forgotten their password without making it the only method of entry.
- As a Step-Up Authentication Method: Use a magic link to re-verify a user's identity before they perform a sensitive action, such as changing their primary email address, deleting their account, or authorizing a large financial transaction.
- As Part of User Choice: The most resilient and user-centric approach is to offer a suite of authentication options on the login screen. By presenting choices like "Sign in with Google," "Sign in with a passkey," and "Email me a login link," the platform empowers users to select the method that best suits their needs and security preferences, while providing valuable data on which methods are most popular.
The Inevitable Rise of Passkeys: Positioning Your SaaS Product for the Future

The long-term strategic direction for passwordless authentication is clear. Passkeys, built on the FIDO Alliance's WebAuthn standard, are the superior alternative that SaaS companies should be prioritizing.
- The Superior Technology: Passkeys solve the same "password pain" problem as magic links but do so with a far more robust security model that is resistant to phishing and a significantly better user experience that is faster and free of context switching.
- The Strategic Imperative: While end-user adoption and understanding of passkeys are still in their growth phase, they are backed by all major technology platforms, including Apple, Google, and Microsoft, and are being positioned as the new industry standard. SaaS companies that adopt passkeys signal to their users and the market that they are modern, secure, and forward-thinking.
The ultimate recommendation for SaaS product leaders, CTOs, and founders is to invest development and strategic resources in a passkey-first authentication strategy. Magic links should be viewed as a tactical, transitional tool. They can serve to bridge the gap while passkey adoption matures or be deployed for the specific niche use cases where they provide clear value. However, they should not be the strategic destination. The future of secure, frictionless, passwordless authentication is not dependent on the fragile and decades-old email protocol; it is device-bound, cryptographic, and already here.
About Baytech
At Baytech Consulting, we specialize in guiding businesses through this process, helping you build scalable, efficient, and high-performing software that evolves with your needs. Our MVP first approach helps our clients minimize upfront costs and maximize ROI. Ready to take the next step in your software development journey? Contact us today to learn how we can help you achieve your goals with a phased development approach.
About the Author

Bryan Reynolds is an accomplished technology executive with more than 25 years of experience leading innovation in the software industry. As the CEO and founder of Baytech Consulting, he has built a reputation for delivering custom software solutions that help businesses streamline operations, enhance customer experiences, and drive growth.
Bryan’s expertise spans custom software development, cloud infrastructure, artificial intelligence, and strategic business consulting, making him a trusted advisor and thought leader across a wide range of industries.


